当前位置:网站首页>Kingbasees Security Guide for Jincang database -- 2.2. prevention of kingbasees' threats to database security
Kingbasees Security Guide for Jincang database -- 2.2. prevention of kingbasees' threats to database security
2022-07-22 16:38:00 【Thousands of sails passed by the side of the sunken boat_】
KingbaseES It is a self-developed high-level database security product , It fully conforms to the national security database standard GB/T 20273-2006 Structured protection level ( The fourth level ) Technical requirements of , This level is approximately equivalent to TCSEC B2 level . Among domestic database manufacturers , It took the lead in passing the Ministry of public security Compulsory safety certification of computer information system safety product quality supervision and Inspection Center , And obtain a sales license .KingbaseES Through the new structured system design and enhanced diversified mandatory access control model framework , Independently developed a number of high-level security features , And complete implementation package Including the separation of privileges 、 Identification 、 Diversified access control 、 User data protection 、 Technical and functional requirements of all structured protection levels including audit .
KingbaseES Different solutions are used for different security threats , As shown in the following table :
Type of threat | Safety elements | Preventive techniques |
|---|---|---|
Identity counterfeiting | Identity Authentication | Through user identification and identity authentication based on enhanced password , Including complex passwords for database users Check the degree 、 Set the validity period of the account password 、 Account abnormal login lock 、 Account login letter Information display and other security policy management mechanisms .KingbaseES It also supports a variety of third-party authentication services Be sure to enable strong authentication , for example ,Kerberos、ssl、radius etc. . Use autonomous access control (DAC) To subject ( Such as user ) Operation object ( As shown in the table ) Carry out authorization management The reason is , Use mandatory access control (MAC), Assign security marks to the controlled subjects and objects , then According to these marks, access arbitration is carried out to resist the security threat of phishing attacks . |
Tampering | Integrity protection | Record the check value for each data block . When reading data , First, complete the consistency verification . If problems are found , Timely error reporting , Prevent errors from spreading , Prevent error escalation . Recalculate the check value of data before writing data to resist the security threat of tampering attacks . |
Deny | Audit | Through the audit function , Automatically record all user operations on the database and put them into the audit log , Auditors (sao) You can analyze the audit log , Take effective measures against potential threats in advance Measures to achieve the effect of repudiation . |
Information disclosure | encryption / Data desensitization / Object reuse | Through transparent encryption 、 Data desensitization 、 Functions such as object reuse , When the data is written to the disk Line encryption , When the authorized user re reads the data, decrypt it . Control the sensitive information transmitted to the client through policies , Where resources are applied for and released Clear the residual information on the media , To prevent information from leaking . |
Denial of service | Resource constraints | By limiting the available resources of users in a database connection application and the address of connection requests Check to resist denial of service security threats . |
Elevated privileges | Authorization management | Through the separation of powers, the management privileges are divided into three administrators , Database administrator 、 Security administrator and auditor Account administrator , Each administrator maintains users within their own permission . Yes SQL Injected behavior identifies and blocks the way its services are , Resist security threats such as privilege escalation . |
边栏推荐
- JVM memory model: runtime data area and thread
- 【Unity】 UI跟随3D物体,世界坐标转UI坐标
- [SSM]SSM整合①(整合配置)
- Simplified writing of not like in MySQL
- JVM: parental delegation mechanism for class loading
- DNS interview questions of computer network
- How to configure webrtc protocol for low latency playback on easycvr platform v2.5.0 and above?
- Process and thread interview questions
- Roson的Qt之旅#98-QML标签页控件TabView
- 梅科尔工作室——HarmonyOs第二次作业
猜你喜欢

The LAAS solution of elephant swap has risen rapidly and built a new defi2.0 protocol
像素和颜色

ERROR: Could not build wheels for pycocotools which use PEP 517 and cannot be installed directly
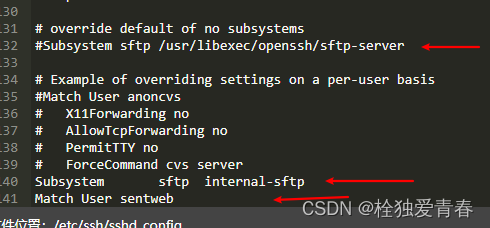
SFTP creation

交換機與路由器技術:標准ACL、擴展ACL和命名ACL

分布式调度框架Elastic-Job
![[initial exploration of STK] create a track to the moon](/img/dc/82398083a33d0cd91eaaeb679060c5.png)
[initial exploration of STK] create a track to the moon

高数_第3章重积分

stm32使用各种传感器的教程

JVM memory model: PC program counters
随机推荐
SFTP creation
nested subqueries
Hybrid混合开发与JSBridge
DNS interview questions of computer network
JVM: parental delegation mechanism for class loading
C language pthread_ Join() function
A few minutes before work, express quick start
洛谷_P1112 波浪数_思维_进制 / 构造 / 枚举
Lecture 7 pipeline, environment variables and common commands
Switch and router technology: static NAT, dynamic NAT, pat and port mirroring
The principle of embedded IDE, openocd introduction and how stlink connects STM32 board
Android interview: 2022 please keep this experience of Netease Android development and Tiktok e-commerce Android engineers
Diversified distribution methods of NFT
博途PLC信号处理系列之卡尔曼滤波程序(Kalman Filter)
What are the requirements for docking with the third-party payment interface?
MySQL starts the global log to locate and troubleshoot slow SQL
用c语言编写一个函数用来删除字符串中的空格并返回空格个数
JVM memory model: PC program counters
招股书写了“元宇宙“318次!飞天云动再战港股“元宇宙第一股“
AT4163 [ARC099D] Eating Symbols Hard