当前位置:网站首页>Network security in Secondary Vocational Schools - the thinking of reverse PE reverse problem solving in 2022 National Games
Network security in Secondary Vocational Schools - the thinking of reverse PE reverse problem solving in 2022 National Games
2022-07-21 01:30:00 【Beluga】
About getting started in reverse .
One 、 Language
1. assembly .
branch Inte| and AT&T Two kinds of grammar .win The platform is mainly Intel ,Linux Disassembly defaults to AT&T , at present CTF in Intel Compilation dominates . Recommended for entry, Wang Shuang 《 assembly language 》, Video tutorial recommendation b Station search small turtle , His teaching is very friendly to beginners
2. Programming .
Meeting C Language is good . To make win platform , You need to understand Windows Mechanism , Meeting win Programming is better 《Windows Programming 》, however API Check those that can be used .
After having a certain foundation in language, you can see 《 encryption and decryption 》
Recommend from win The platform starts playing .
Reading is too boring , recommend b Station search release reverse basic introduction , There are many reverse video teaching drops , Suitable for beginners
Two 、 Tools ( The debugger 、 Counter assembler )
1.win Under the OD、IDA、 windbg
2.Linux Under the gdb 、objdump、nm、Itrace Those auxiliary tools grope for themselves , The help documentation is quite complete
3、 ... and 、 About learning
1. Do more , Debug and analyze more by yourself , The real reverse level cannot be improved by reading , You can write your own program, debug and analyze it yourself .
2. Familiar with debugging tools
3. Conduct linux Before program analysis , Study first linux Basic operation of the system
4. Play appropriately crackme This kind of .crackme.de ,reversing.kr
5. Find some simple reverse 、pwn Of ctf Practice while learning
6. I love to crack 、 Look at the snow 、 These sites can be visited
Secondary vocational network security —2022 The national championship is in reverse PE Reverse Their thinking

1. On the desktop of the target server scene PE01.exe Static debugging of binary files , take main The entry address of the function is used as Flag Value submission ;
ida pro
open ida The file of , Drag the file into x64 Bit ida In the program



We're in ida, You can start static analysis of the program ,ida You can also dynamically analyze programs , I'll give a tutorial later
The title is ( On the desktop of the target server scene PE01.exe Static debugging of binary files , take main The entry address of the function is used as Flag Value submission ;)
It means we just need to find the program main Just enter the function

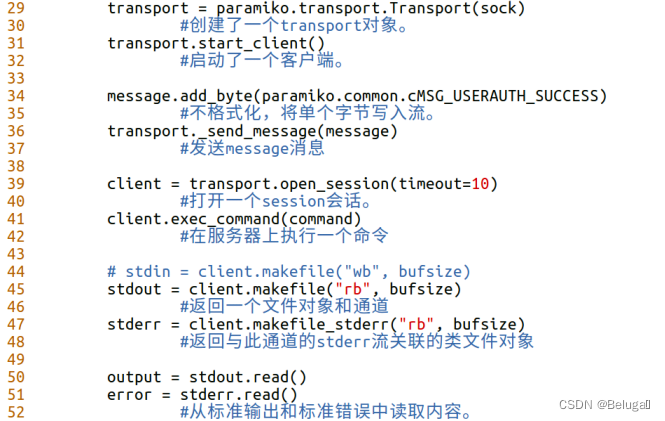
stay ida In the work bar on the left , It will display the entry addresses of various functions of the program and system , We can see , This procedure main The entry address of the function is
0x00000000004005BD
1
Or press the space

You can also see the entrance address here , If you can't see it, double-click in the taskbar on the left of the program main function
0x00000000004005BD
1
2. On the desktop of the target server scene PE01.exe Static debugging of binary files , Take the key function in the binary file to check the license as Flag Value submission ;
Press... On this interface f5


ida Try to restore the source code for us , Analyzing the program source code can find , The key letter to check the permit is
strcmp
strcmp Function is to compare the size of two strings , Returns... When two strings are the same 0, Returns a positive value when the first string is greater than the second string , Otherwise, a negative value is returned
1
3. On the desktop of the target server scene PE01.exe Static debugging of binary files , find Flag1 Value and submit ;
stay ida Press inside shift+f12 You can find the string in the program

Here we can see all the strings in the program
flag The string can be seen here , But I didn't flag String in the program , Let's move on to the next question
4. On the desktop of the target server scene PE01.exe Static debugging of binary files , Try to crack the binary , Take the echo information after successful registration as Flag Value submission ;
You don't have to crack it , Then I'll explain how to crack , Or press shift+f12

The echo information after successful registration is :
Access Granted!
1
5. On the desktop of the target server scene PE01.exe Static debugging of binary files , Use the license code required for this activation as Flag Value submission ;
Or press shift+f12

The license code required for activation is :
AAAA-Z10N-42-OK
Because the topic doesn't call us dynamic debugging program , Just call us static analysis , So strings are written dead in the program rodata Duanli , Press down shift+f12 Take your time
边栏推荐
- What are the three cache update strategies?
- Tutorial on principles and applications of database system (036) -- MySQL index (II): create index
- 网络安全—综合渗透测试-CVE-2017-12629-Apache Solr远程代码执行
- Unity:PC开发,鼠标点击物体触发物体更换材质
- Miller gingival recession(牙龈退缩)与mucogingival junction(膜龈联合)
- Tutorial on principles and applications of database systems (029) -- data integrity of MySQL (II): defining primary keys
- Classes and objects (top)
- Blurred photos, second high-definition big picture, flying propeller ppde takes you to reproduce the image restoration model cmfnet
- [solve ax=b]
- mim命令
猜你喜欢

Light up through TCP

WebRTC系列-SDP之类关系梳理

Day106.尚医通:数据字典列表、EasyExcel、数据字典导入导出、集成Redis缓存

裕华万宝风扇安装顺序
网络安全—综合渗透测试-CVE-2018-10933-libssh漏洞分析

Dix minutes pour générer un effet de design intérieur de qualité film et télévision, comment mettre à niveau l'industrie de la maison traditionnelle avec Red Star McLaren Design Cloud

infraversion和superaversion

How can red star Macalline design cloud upgrade the traditional home furnishing industry in ten minutes to produce film and television level interior design effects

30万奖池等你来战!自然语言处理(NLP)赛事合集来啦

Classes et objets (en haut)
随机推荐
Tutorial on principles and applications of database system (027) -- MySQL modifying data in tables (III): update
已解决No module named ‘flask_misaka‘【BUG解决】
Baidu PaddlePaddle easydl helps manufacturing enterprises with intelligent transformation
SQL injection attack risk
Summer vacation safety second assignment
Luogu p1678 troubled college entrance examination volunteers
cannot import name ‘import_string‘ from ‘werkzeug‘【bug解决】
数据库系统原理与应用教程(022)—— MySQL 支持的数据类型总结
cannot import name ‘import_ String 'from' Werkzeug '[bug resolution]
Light up through TCP
洛谷 P1024 [NOIP2001 提高组] 一元三次方程求解
数据库系统原理与应用教程(032)—— MySQL 的数据完整性(五):定义自增列(AUTO_INCREMENT)
Blurred photos, second high-definition big picture, flying propeller ppde takes you to reproduce the image restoration model cmfnet
力扣124题:二叉树中的最大路径和
Create a file. If the superior (or superior, etc.) directory of the file does not exist, create the superior directory first, and then create the file
HW2021攻防演练经历碎碎念-见解
VMware startup error: exception 0xc00000005 and windwos11 have no Hyper-V solution
Is it difficult to develop a test platform?
数据库系统原理与应用教程(024)—— MySQL 修改数据表的结构
In the last interview, I knelt on redis, finished the internal redis documents given by cousin Ali, and finally entered the big factory