当前位置:网站首页>"Review of software engineering in Wuhan University of technology" Chapter 6 | coding specification
"Review of software engineering in Wuhan University of technology" Chapter 6 | coding specification
2022-07-22 18:19:00 【Graski】
Catalog
Chapter six | Coding standards
【 Software programming efficiency 】
Chapter six | Coding standards
【 Coding standards 】
Basic overview
Software programming is a complex and iterative process , It's not just about writing code , It should also include code reviews 、 unit testing 、 Code optimization 、 A series of work such as integration debugging .
Software coding specifications are language specific , A set of rules that describe how to write code .
reality : Software life cycle 70% The cost is maintenance . Software is rarely maintained by original writers in its life cycle
Purpose : Improve coding quality , Avoid unnecessary program errors . Enhance the readability of the program 、 Reusability and portability


Good notes explain why , Not how : Do not repeat the description of the code in comments
When commenting, you need to think about what to write in the comment , Instead of scribbling
After writing the comments, review them in the context of the code , Do they contain the correct information
When modifying code , Maintain all comments around the code


【 Software programming efficiency 】
Code optimization
Optimization is equivalent transformation of code , Make the code running result after transformation the same as that before transformation , But faster execution or less storage overhead .
according to 80/20 principle , Realize the refactoring of the program 、 Optimize 、 Extensions and document related things usually cost 80% The amount of work .
Focus on improving overall efficiency 、 Supplemented by local efficiency
When optimizing the program , We should first find the bottleneck that limits efficiency
First optimize the data structure and Algorithm 、 Then optimize the execution code
T(n) and S(n) It is often opposite , Trade offs are needed . Optimize , It is a multi-objective optimal decision , When it is impossible to optimize all goals , Compromise is needed to achieve the overall optimization .
Correct code is more important than fast code , No optimization can destroy the correctness of the code
Never try to optimize your code without performing a pre - and post performance evaluation

【 unit testing 】
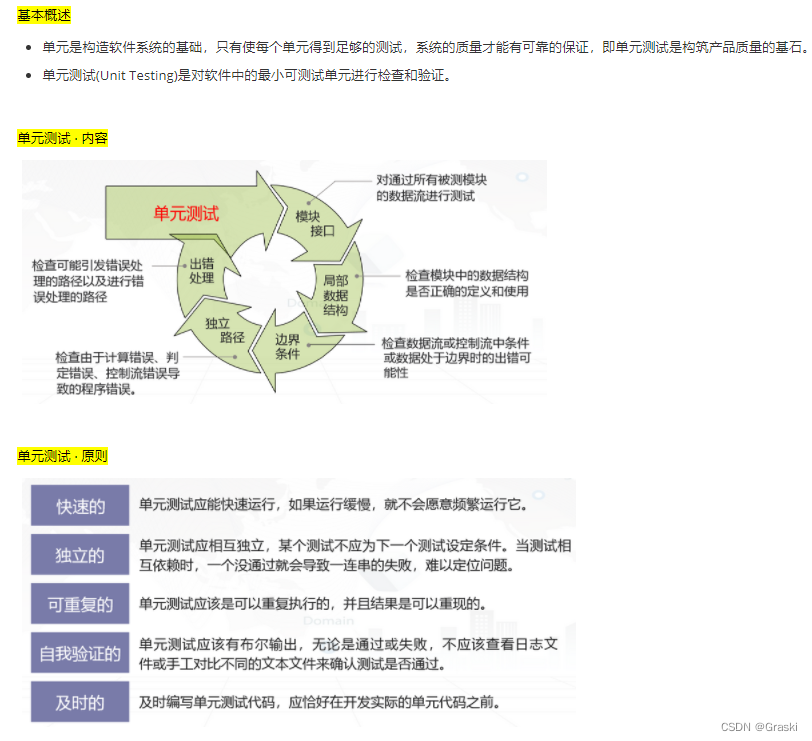
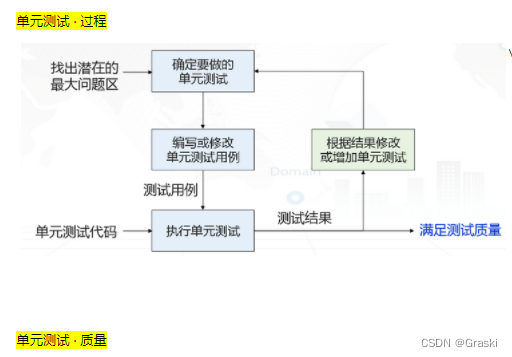
Test pass rate refers to the proportion of test cases that pass the test process , Unit testing usually requires the passing rate of test cases to reach 100%.
Test coverage is a measure of test integrity , You can know whether the test is sufficient and where the weakness is . Code coverage is a measure of unit testing , But also We cannot blindly pursue coverage .
Coverage criteria : Statement override 、 Determine coverage 、 conditional 、 Determine conditional coverage 、 Conditional combination covering 、 Path coverage
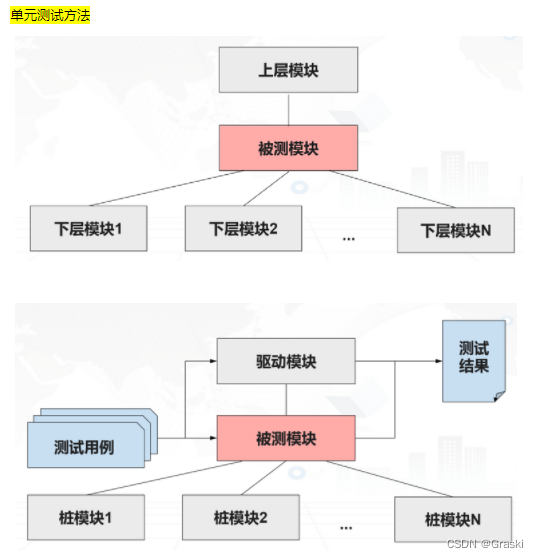
【 Unit test questions 】
choice question



Judgment questions
Don't fix bad programs , To rewrite . T
Short answer

边栏推荐
- Gbase8s database set collection statement
- pm的报警告:“npm WARN config global --global, --local are deprecated
- Gbase8s database set constraints statement
- 学IT,你后悔了么?
- GBase8sUNION ALL 运算符
- Multi type low rate DDoS attack detection method based on hybrid deep learning
- 计算存款利息
- 如何消除 MySQL表中的字段特别设置的字符集和排序规则?
- Concurrent model values actor and CSP
- Gbase8s database set database object mode statement
猜你喜欢

QT笔记——Qt动态属性 之 unpolish() 和 polish()
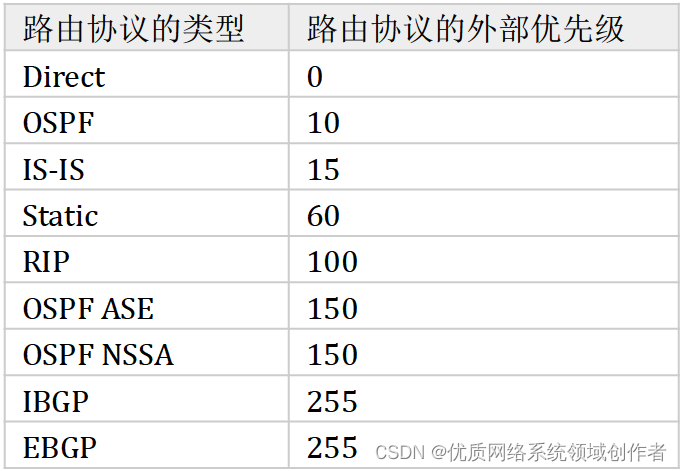
What is the routing protocol

云原生强势发展,企业该如何抓住业务机遇

zmq无锁队列的浅解

A trick to teach you how to visualize recruitment data ~ is there anyone who can't analyze these data cases?

QT筆記—— QTableWidget 之 拖拽行數 和 移動

QT笔记——操作Execl

并发模型值Actor和CSP

超实用转型攻略:《2022央国企云原生落地实用指南》正式发布

如何破解IT中年危机下的惨淡人生
随机推荐
如何搭建清晰易懂的数据看板?
以SPI的仿真文件学习TB写法
SQL多条件查询无法实现
云原生(十) | Kubernetes篇之Kubernetes简介
Shallow solution of ZMQ lockless queue
【Excle】生成guid和datetime导入测试数据到数据库
Aruba学习笔记04-Web UI --Configuration面板介绍
Anaconda 环境迁移
JS String charAt substring() substr slice toUpperCase toLowerCase indexOf
Go has a simple understanding of the interface
Ssl/tls protocol attack detection method based on stream spectrum theory
Gbase8s database intersect operator
Gbase8s database identity connection
Verilog for loop (1)
A trick to teach you how to visualize recruitment data ~ is there anyone who can't analyze these data cases?
Multi type low rate DDoS attack detection method based on hybrid deep learning
A survey of network defense decision-making methods based on attack defense game
QT笔记—— QTableWidget 之 拖拽行数 和 移动
Web3 sharing
「武汉理工大学 软件工程复习」第六章 | 编码规范