当前位置:网站首页>Attack and Defense Technology Part I - know the enemy (attack means)
Attack and Defense Technology Part I - know the enemy (attack means)
2022-07-22 00:53:00 【Planet Guardian】
List of articles
- information gathering
- fingerprint identification
- Break through the border / Dot
- Remote code execution (RCE)
- WebShell
- rebound Shell
- Interactive Shell
- PowerShell
- DNSLog
- CC attack
- Stand by attack
- C End attack
- Authority maintenance
- Elevated privileges
- Post penetration / Domain infiltration
- Horizontal movement
- Vertical expansion
- Centralized system
- Operational platform
- middleware
- back door
- Memory horse
- Trojan horse
- Shellcode
- agent / Tunnel
- Domain preposition
- Hash passing
- DNS Rebinding
- Black box scanning / White box scanning
- Remote control /C2
- Weak password
- Hit the library
- Account cracking
- Password cracking
- Catalog explosion
- Virtual machine escape
- Sandbox escape
- Don't kill the Trojan horse
- Rootkit
- Reverse proxy / Forward agency
- Template Injection
- social engineering
- Phishing attack
- Harpoon attack
- Supply chain attack
- Near source attack
- Puddle attack
- Buffer overflow attack
- Replay attack
- Common attack tools
information gathering
- Information Collection refers to the use of various means , Collect pertinent information about the target unit , It covers a wide range of areas , Including regular domain names IP/ port / service 、Wb Site 、APP、 Components / Asset information such as middleware , Source code 、 Account, password and other sensitive information , Organizational structure 、 Subsidiary company 、 Supplier and other related information , Employee email / Telephone / Position and other personal information , Basically, it's just related to the enterprise / Everything related to external information is included .
- Through as comprehensive information collection as possible , The attacker can choose the appropriate breakthrough point and breakthrough technique in the subsequent attack , As well as further deepening as effectively as possible , Finally achieve the goal .
fingerprint identification
- Components are the smallest units in cyberspace ,Web Applications 、 database 、 Middleware and so on belong to components .
- Fingerprint is a piece of characteristic information that can identify the object type on the component , It is used to quickly identify target services in the process of penetration test information collection .
- Fingerprints generally contain web Service fingerprints and other service fingerprints .
- about web service , Fingerprint identification generally refers to the identification of web Apply front-end code features 、 route 、 Comparison of server response information , Identify Web Application name used by the application 、 edition 、 The process of frame information .
- Fingerprint identification of other services , Generally, it also sends specific data packets to the corresponding port , Determine the service type opened on the corresponding port through the response information 、 name 、 Version and other specific information .
- Fingerprint recognition plays an important role in information collection , Through fingerprint identification as comprehensive and detailed as possible , Attackers can quickly select the right vulnerabilities to break through , And use appropriate ways to make in-depth use .
Break through the border / Dot
- Boundary breakthrough refers to breaking through the network boundary of the target , The process from external network breakthrough to internal network , Also known as dot .
- In general , After the attacker has collected comprehensive information about the target , We will try to break through the boundary of the Japanese standard through various means , In order to further .
- At present, common border breaking methods , One is to use routine web Class vulnerability , Directly attack the network assets related to the enterprise ; The second is to use social engineering means such as fishing near the source , Attack people ; in addition , Target suppliers first 、 Upstream and downstream units attack , Then move back to the target unit , It is also one of the common breakthrough techniques in recent years
Remote code execution (RCE)
- RCE It is the abbreviation of two kinds of vulnerabilities , Respectively Remote Command/ Code Execute, Remote command / Code execution , It can be used in attack and defense drills RCE Obtain application server permissions , Enter the intranet .
1、 Remote command execution
- Remote system command execution ( Operating system command injection or command injection for short ) It is an injection vulnerability .
- The attacker injected Payload Will be executed as an operating system command .
- Only when the web When the application code contains an operating system call and user input is used in the call , Can be carried out OS Command injection attacks .
- They are not language specific , Command injection vulnerabilities may occur in all languages that let programs call system shell commands , Include C, Java, PHP, Perl, Ruby, Python etc. . Operating system usage web The privileges of the server execute arbitrary commands injected .
2、 Remote code execution
- Code injection attacks are different from command injection attacks .
- Because of requirements design , Sometimes the background needs to execute the user's input as part of the code , This creates a remote code execution vulnerability
- Including the use of code to execute functions and the use of unsafe deserialization ( for example Struts2).
- Its actual harmfulness depends on the limitations of the server-side interpreter ( for example ,PHP, Python etc. ).
- In some cases , An attacker may be able to upgrade from code injection to command injection .
WebShell
- webshell In order to asp、PHP、jsp perhaps cgi A code execution environment in the form of web page files , Mainly used for website management 、 Server management 、 Permission management and other operations .
- Easy to use , Just upload a code file , Visit through website , Many daily operations can be carried out , It greatly facilitates users' management of websites and servers .
- Because of this , There are also a small number of people who use the modified code as a backdoor , In order to control the website server .
rebound Shell
- rebound Shel! As the name suggests, it is a reverse connection Shell.
- During the attack, due to network restrictions , The attacker cannot directly connect to the attacked host SSH、TELNET、RDP And other remote control services , At this time, the attacker rebounds Shell The tool or command starts on the attacked host bash or cmd etc. Shel( Program , And redirect the input and output of the program to the host of the remote attacker through the network , It is convenient for attackers to directly control the target host .
Interactive Shell
- Interactive mode is to execute on the terminal ,Shell Waiting for user input , And immediately execute the submitted command .
- This pattern is called interactive because Shell Interact with users .
- This pattern is also familiar to most users : Sign in 、 Execute some orders 、 sign out .
- Rebound is often used in attack and defense drills Shell Get interactive Shell.
PowerShell
- PowerShell Is a powerful interactive command line Shell( And scripting language , Default installed in Windows On the operating system ,2016 Support open source and cross platform .
- because PowerShell Having a wide range of windows Internal access , therefore , Attackers using this technology to attack mainly include the following aspects : Create file free malicious code that runs in memory without leaving any traces on the disk 、 Perform complex operations through extensive access within the operating system 、 Persistent persistence is achieved by periodically loading malicious code into memory 、 Discover information and collect and disclose data 、 Move horizontally through the network .
Use by attackers PowerShell To adopt the following defense evasion techniques :
- Load and execute malicious code directly in memory ;
- The abuse of Powershell Commands and scripts to execute . In the attack and defense drill , If the attacker finds a function point of command execution , Can be carried out by Powershel Script to make the victim machine online to the attacker C2 Server .
DNSLog
- DNSLog It is a common anti connection detection technology .
- Usually in the process of vulnerability exploitation , Applications are isolated due to intranet 、 The program has no output and other restrictions , Unable to immediately feed back the results to the attacker , At this time, the attacker will capture the side effects produced during the attack as side channel information .
- The attacker carries a custom domain name when launching an attack , If the attack succeeds , The application will automatically resolve the domain name carried in the attack code , At this time, the domain name held by the attacker ns The server is aware of this process ,DNS Requests will be an important side effect of the attack .
CC attack
- CC attack (ChallengeCoHapsar) yes DDoS A common type of attack , The attacker uses the proxy server to generate a legitimate request to the victim host , Realization DDoS And camouflage .
- CC An attack is an attack against HTTP Business attack means , This attack mode does not require too much attack traffic , It is a precise blow to the bottleneck of service-side business processing , Targets include : A large number of data operations 、 Database access 、 Large memory files, etc , The attacker controls some hosts to send a large number of data packets continuously to the other server, resulting in the depletion of server resources , Until the crash
Stand by attack
- The so-called side station , It refers to the server corresponding to the target application site IP Other applications open on other ports of , Through attacks against these other applications , It is called side attack .
- Generally speaking , The main application system of the target is relatively well protected , And there may be weak points in the side station , Once the server is accessed through the side station , Then the main application system is likely to fall .
The target main application site is 192.168.123.123 Of 80 Open port applications ,
If the same is found through scanning IP:102.768.123.123 Of 8888 There is another site application on the port ,
in the light of 8888 Compared with the main application system, the attack behavior of the port application is a side attack .
C End attack
- Generally speaking , The server in the computer room IP Will be more concentrated , If the target server P Focus on specific C paragraph , Then you can scan C Others in the paragraph IP To find servers that may be missing during the information collection phase , This is for C Duan's motha service attacks , It's called C Segment attack .
Authority maintenance
- - Victor controls the permissions of the target host , It generally refers to maintaining the connection between the lost host and the remote control server .
- Permission is generally maintained through scheduled tasks 、 Subsequent items 、 Repair the registry and other ways to achieve .Jeva Memory horse is invalid after restart , Therefore, there is also the saying of Authority maintenance , For example, by replacing jar Package, etc .
Elevated privileges
- Privilege escalation refers to the elevation of the attacker's privileges , Generally refers to the elevation of permissions on the operating system .
- After the attacker routinely obtains the privileges of the server , Often the current user is not an administrator ( Like just web Service permission or database permission ), Some operations will be blocked ,
- Therefore, the attacker will try to promote the current operating user to the administrator through vulnerabilities and other means , This process is called right raising .
Post penetration / Domain infiltration
- Generally speaking, post penetration refers to breaking through the network boundary of the target and finishing the dot , After being able to access the intranet .
- Domain penetration pointer pair Wdows AD The infiltration process carried out by the domain , The general ultimate purpose is to obtain the operation permission of the domain control host ,
- After domain penetration , Generally, attackers can obtain the account and password information of all employees ( Generally speaking, passwords are ciphertext , But it can basically be cracked into plaintext , And the ciphertext will not affect the use ).
Horizontal movement
- Horizontal movement usually refers to permission acquisition in the same area of the intranet ,
- If you follow DMZ In the district 10.10.10.2 The server got DMZ In the area 10.10.10.24 Operating system permissions of the server .
- Lateral mobility is widely used in complex intranet attacks , It's also APT( Advanced Sustainable threat ) An important part of the attack .
- Lateral movement is mainly in AFT Play a role in the subsequent attack , It is used to steal a large amount of information assets and conduct deeper penetration .
- except AFT Beyond threat events , At present, extortion and internal threats faced by enterprises are mostly related to “ Move horizontally 〞 of .
Vertical expansion
- Vertical expansion refers to the movement between different areas of the intranet , If you follow DMZ The server in the zone got IDC Server permissions in the zone , It can be called longitudinal movement .
- Generally speaking , Through vertical expansion , Attackers can gain different network privileges , And gradually approach the final goal .
Centralized system
- Centralized system refers to the application that can batch manage servers or save a large number of server connection credentials within an enterprise ,
- Common centralized systems include : Domain control 、 Fortress machine 、 Operation and maintenance management system 、 Allow command execution on the client Zabbix Or common desktop management system
- Centralized system is the internal system that attackers often attack , Once taken down , The host controlled by the centralized system can also be regarded as controlled , It's devastating .
- Common attack ports of centralized system include the host of centralized system 、 Access control 、 To configure 、 Weak password, etc .
Operational platform
- The operation and maintenance platform refers to the application that can operate and maintain the management server in batches within the enterprise , The basic operation and maintenance platforms belong to centralized systems , It's an attack
One of the systems that the attacker will focus on during the attack
middleware
- Middleware usually refers to the connection should A kind of software between using system and exploring system , It belongs to a large category of basic software , The overall function is to provide an environment for the operation and development of the application software on the upper layer of the machine , Common are Tomcat、websphere、Weblogic wait .
- Because middleware is widely used in actual production , Once the middleware is found to have serious vulnerabilities , The impact is generally extremely extensive , Such as Tomcat Ghost cat loophole 、weblogic Deserialization vulnerability of , These vulnerabilities are also one of the means that attackers like to exploit .
back door
Backdoor refers to a method of bypassing security control to obtain access to programs or systems , Is to stay in the computer system , A way for a special user to control a computer system in a special way . Its main purpose is to facilitate the secret entry or control of the system again in the future .
The backdoor sources on the host mainly include the following :
1、 The attacker used deception , By sending e-mail or files , And induce the operator of the host to open or run the mail or file with Trojan horse program , These Trojan horse programs will create a back door on the host ;
2、 The attacker captured a host , After obtaining its control , Create a back door on the host , For example, install Trojan horse programs , For the next intrusion ;
3、 Another kind of back door is introduced in the process of software development . In the software development phase , Programmers often create backdoors in software to facilitate testing or modifying defects in programs , But when the software is released , The back door was intentionally or unintentionally ignored , Not deleted , Then the software is born with a back door , The host that installs the software inevitably introduces a back door .
Memory horse
- Memory horse is a common means of no file attack , With the increasing popularity of attack and defense drills , Flow analysis 、EDR And other professional safety equipment are widely used by blue side , Traditional file upload webShell Or backdoors that reside as files are more and more easily detected , Memory horses are using more and more .
- Memory horses are roughly classified as follows :Filter type 、servlet type 、Listener type 、Agent type 、controller Type, etc. .
- The memory horse is mainly used to directly insert the running attacker into the running service Webshell, Service backdoor that does not depend on the existence of entity files , It's very difficult to detect .
Trojan horse
- Trojan horse is a piece of malicious code with special functions hidden in normal programs , It has the ability to destroy and delete files 、 Send the password 、 Record keyboards and attacks Dos Back door program with special functions .
- Trojan horse is actually a program used by computer attackers to remotely control the computer , Parasitize the control program in the computer system under control , collaborate from within with forces from outside , To be infected with trojan virus computer operation .
- The general Trojan horse program is mainly to find the back door of the computer , Waiting for an opportunity to steal passwords and important files in the controlled computer .
- The controlled computer can be monitored 、 Illegal operations such as data modification .
- Trojans have strong concealment , Can suddenly launch an attack according to the hacker's intention .
Shellcode
- shellcode Refers to self-contained binary code that can complete special tasks , It's a piece of code executed to exploit a software vulnerability .
- Shellcode It's often written in machine language , By hijacking pc Inserting a segment into the instruction register allows CPU Executive Shellcode Machine code , Allow the computer to execute any of the attacker's instructions , Depending on the task, it may be to issue a system call or establish a high authority Shell,Shellcode Hence the name .
- Its ultimate goal is to gain control of the target machine , Therefore, it is generally sent into the system by attackers to execute by exploiting the vulnerabilities of the system , So as to obtain the execution environment of special permission , Or set up a privileged account for yourself .
agent / Tunnel
- agent : Just like the literal meaning , That is, the communication between the user and the target is through the agent “ Take care of 〞.
- If say C yes AB Proxy for access between , Then the actual communication is as follows , And the server B It can only be perceived that the request comes from the agent C, Can't feel A The existence of .
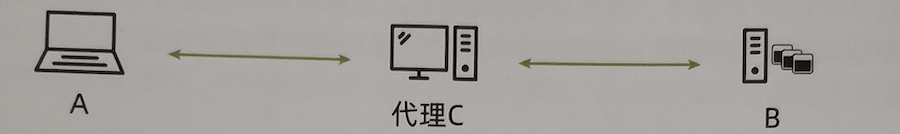
The concept of tunnel is in the context of attack and defense drill , And agents are relatively close , It is generally used for attackers to penetrate from the external network to the internal network .
Domain preposition
- Domain preposition (Domain fronting), It is a hidden connection to the real endpoint to avoid Internet Application Technology .
- When operating on the application layer , Domain fronting enables users to access HTTPS Connect to blocked Services , On the surface, it seems to be completely different from another
Communicate with the site , It is often used to hide the server used by attackers in attack and defense drills .
Hash passing
- FTH, yes pass the hash Abbreviation , because windows AD Authentication features of the domain ,
- The attacker obtained the user password ntim hash Under the circumstances , Even if you don't know the plaintext, you can complete the authentication .
- So this kind of attack is called pass the hash That is, hash transfer .
DNS Rebinding
- In the process of browsing the web , The user enters the web address containing the domain name in the address bar .
- Browser pass DNS The server resolves the domain name to IP Address , And then to the corresponding 1P Address request resource , Finally, we show it to the users . And for domain name owners , He can set the corresponding IP Address .
- When the user first accesses , Resolve the domain name to get a IP Address ; then , The domain name holder modifies the corresponding IP Address ; The user requests the domain name again , Will get a new IP Address .
- For browsers , The whole process is to visit the same domain name , So I think it's safe .
adopt DNS Rebinding attacks can bypass the same origin policy , Attack other devices on the intranet .
Black box scanning / White box scanning
- Black box scanning is generally to identify the type and version of the service remotely , Determine whether there are vulnerabilities in the service .
- In some newer vulnerability scanning software , Some more advanced technologies are applied , For example, simulate penetration attack .
- White box scanning is to scan vulnerabilities with host privileges .
The scanning object of black box scanning is the runtime Application , The scanning speed is slow and the coverage is low ; White box scanning focuses on scanning the source code vulnerabilities of the application itself , No runtime environment is required to scan , Fast scanning speed and high coverage .
Remote control /C2
Remote control and C2 Similar in concept .
- Remote control refers to remote control client or remote control server .
- C2 yes Command and Control Abbreviation , Command and control .
- Generally, it is also divided into C2 The service side and C2 client .
Remote control /C2 The server can control the machine with the client installed , Be able to execute specific commands or upload and download data , You can also forward traffic from the server to the Intranet environment where the client is located , Commonly used for intranet penetration .
Weak password
Weak password (weak password) There is no strict and accurate definition , It is generally believed that passwords that are easy to be guessed by others or cracked by cracking tools are weak passwords . for example “123〞、"abc〞 etc. , Because this kind of password is easy to be cracked by others , Thus, the user's Internet account is controlled by others , Therefore, it is not recommended to use .
The generation of weak passwords is related to personal habits and consciousness . Combinations that are prone to weak passwords include :
[1] Numbers or letters are arranged consecutively or mixed , Key secret letters are arranged consecutively , Such as :123456、qwerty、abcdefg、1123abc etc. ;
[21 Birthday , full name + Birthday , Such passwords can easily be cracked by social workers ;
[3] The phrase code , Such as :5201314 etc. .
Hit the library
The library collision attack is attributed to the repeated use of passwords . Because many people use passwords repeatedly for multiple accounts , Therefore, only a group of account passwords is enough to expose most or all of their accounts .
[1] Weak password sniffing : similar 111111、123456 This simple password is used by many people , Use such a weak password to test a large number of accounts , There is a certain probability to find some accounts that are really using weak passwords . Implementing such an attack generally requires that the attacker has mastered a large number of accounts and common weak password libraries ;
[2] Use drag library data : This is a way to attack with a higher success rate , The principle is that most people tend to use the same password on multiple sites . When an attacker successfully invades a site with weak security protection ability A, And get all the user name and password combinations of its database , Then take these combinations to the site B Try ;
[3] Brute force cracking against high authority accounts : Strictly speaking, brute force cracking and database collision are two types of attacks , This is mainly for some high authority accounts ( Such as website administrator ) Use a lot of passwords to test , The target of the account you want to steal is very clear .
Account cracking
[1] Account enumeration
Account enumeration is one of the common account breaking behaviors , Its main purpose is not to obtain a valid account password combination , Just get a valid user name . Generally, it can be used for other attacks after obtaining the user name , For example, the password is broken for existing users or the user name is used for directional phishing ;
[2] Account brute force cracking
The traditional account brute force cracking refers to the exhaustive password of a specific account , If a system is found admin account number , Then obtain by exhausting passwords adlmin The right password , However, this burst method is not effective in systems or applications with account locking mechanism , Even in some scenarios, it will lead to business interruption ;
[3] Code spray
This scenario is generally because the user name rule of the enterprise is relatively simple , An attacker can generate the correct user name ; Or the attacker obtains the internal user name list of the enterprise through other means in advance . After the attacker obtains valid account information , You can use a fixed password , Exhausting the form of user names to quickly find effective account password combinations . Such as : The fixed password is Qwer1234, Quickly enumerate all user names to find the employees who use the password in the enterprise . Because the conventional account locking mechanism and risk control mechanism are aimed at a single account , Therefore, this method can bypass the account locking and risk control mechanism .
Password cracking
Password cracking refers to the process of reversing the password from the ciphertext to the plaintext password , Common password cracking methods include brute force cracking through password dictionary or direct query of plaintext password through public password Library .
Catalog explosion
Directory burst refers to the use of universal codes to web Attack of path enumeration by application . Through directory burst , Attackers can generally obtain web Backup files on the site 、 Hide pages or interfaces with weak points .
Virtual machine escape
Virtual machine escape means that the attacker obtains the privileges of the virtual machine , Exploit the vulnerability of virtual machine or break through the virtual machine manager by other means (Hypervisor), The process of obtaining the administrative rights of the host operating system , Finally, you can control other virtual machines running on the host . Virtual machine escape breaks the boundary between permission and data isolation , It has become a national trend in the era of Cloud Computing , One of the daunting major security threats , It opens a new way for attackers .
Sandbox escape
Sandbox is an execution environment that restricts program behavior according to security policy , That is to say, let the program continue to run after finding suspicious behavior , It stops when it turns out to be a virus . Sandbox escape is in the code execution environment , Free from all kinds of filters and restrictions , In the end, I succeeded in getting shell The process of permission . Attackers often try to hide malware attacks to avoid sandbox detection , There are three types of methods :
[1] Check whether the sandbox exists before attacking , If detected by sandbox , It will automatically adjust to the non threat operation mode , To escape detection ;
[2] Use the weakness or vulnerability in the sandbox technology system to realize escape ;
[3] When analyzing sandbox , Will use some unopened attack attributes to achieve the goal .
Don't kill the Trojan horse
The Trojan horse in the kill Free Trojan horse generally refers to the remote control content client , Anti virus refers to the host installed with anti-virus software , This Trojan will not be identified as a Trojan file , It can execute the well normally, so that the host can go online to the remote control server and be controlled by the attacker , Or execute other malicious commands normally without being recognized by anti-virus software . Among them, the killing free part , It may be an exemption for specific killing software , It is also possible to use the general software to avoid killing ( That is, for all killing software, no killing )
Exemption mainly includes static exemption and dynamic exemption .
- Static anti-virus means that the Trojan itself will not be recognized by anti-virus software when it is not running , Generally, you can remove the characteristic fragments of the Trojan horse ( Signature ), And by encrypting malicious code fragments , Dynamic decryption only at runtime , To achieve the effect of static killing free .
- Dynamic anti-virus means that Trojans are not recognized by anti-virus software when running , At present, the most common dynamic killing free technology is to load the attacker's malicious code through the application in the killing software white list ( That is, white plus black ) Finally, dynamic killing free .
Rootkit
Rootkit It is a method of modifying the operating system kernel or changing the instruction execution path , To hide system objects ( Including documents 、 process 、 drive 、 Registry entries 、 Open ports and network connections ), In order to escape or circumvent the standard system mechanism .
Rootkit Stealth attacks fall into two categories :
[1] Memory resident Rootkit Stealth attack : No magnetic file ,Rootkit All are loaded and run in memory , After the target machine shuts down , The file image that implements the attack deletes itself 、 Auto disappear , Cause undocumented ;
[2] Camouflage memory Rootkit Stealth attack : Even if there are disk files , But after it runs in memory, it implements memory view camouflage , Deception related real-time detection and evidence collection tools , Result in obtaining perjury .
because Rootkit It is recognized as the most difficult hidden means to detect in the industry , Therefore, it is often used by attackers in high-quality APT attack ,
For example, implant a persistent back door .
Reverse proxy / Forward agency
Reverse proxy :
- Generally, when the server can communicate with the Internet server , The intranet server establishes a stable tunnel by accessing the external server , And forward the external traffic to the agent of the intranet .
- Faster than forward proxy , But the characteristics are more obvious , Easy to find .
Forward agency :
- Generally, when the server cannot communicate directly with the Internet server , Proxy method used by the attack team .
- The more common method is to use port multiplexing to pass the attacker's traffic http/https After packaging, arrive at the intranet and forward the traffic , For attackers, requests and responses are received routinely http/https Respond to .
- Concealment is higher than reverse proxy , But it's slower .
Template Injection
Template engine can separate the interface and data 、 Separation of business code and logical code , This greatly improves the development efficiency , Good design also makes code reuse easier . meanwhile , It also expands the attack surface . Except for the regular XSS Outside , The code injected into the template may also cause RCE. Generally speaking , Such problems will occur in hirong ,CMS,wiki Produced in .
social engineering
Social engineering generally refers to the use of social engineering related means by attackers , Through near source and all kinds of fishing ( Telephone 、 WeChat 、 Mail, etc. ) Related techniques , Attack the target and finally obtain relevant permissions . In recent years, the difficulty of traditional attack methods has gradually increased , Many attack teams like to use social work methods to break into the intranet .
Phishing attack
Phishing attacks refer to attacks via email 、 WeChat 、 Induce internal personnel of the enterprise to click malicious links or open malicious documents by means of telephone , Directly obtain the office terminal permission of enterprise personnel .
Fishing attacks are usually combined with Trojan free , Members of the red team will collect contact information of relevant personnel of the enterprise , Prepare the corresponding script , Induce enterprise insiders to click , Enter the internal network for horizontal attack , Collect the internal information of the online personnel terminal .
Harpoon attack
Harpoon attack is more accurate than fishing attack , It is different from the regular phishing emails sent in large quantities , Harpoon attack refers to a fishing attack against a specific employee of a specific enterprise , Generally, it is mail phishing . Because after collecting information , The attacker customized the script , The target is more likely to be hooked , At the same time, phishing is also more difficult to intercept with common email gateways .
Supply chain attack
Supply chain attacks refer to attacks against software developers and suppliers . Because the supplier may develop software for the target unit 、 System operation and maintenance or direct network connection based on other business characteristics , Attackers can attack suppliers first , Get the source code from the supplier , Even connect directly to the intranet of the target enterprise through the supplier network . In actual attack and defense , Due to timeliness 、 Controllability and other reasons , Generally, we will not attack the developer infrastructure ( Such as developing plug-ins )、 Introducing malicious code into open source repositories .
such as , supplier A It provides a certain application system to a large number of banks , So for suppliers A The attack may be able to obtain the source code of the application system , In order to dig Oday To invade ; meanwhile , supplier A There may also be internal information that can directly connect or remotely operate the application system of each bank . So once the attacker takes the supplier A, It can be directly connected to the bank intranet . In recent years , Because the frontal attack is more difficult , Therefore, the proportion of supply chain attacks is increasing year by year .
Near source attack
Near source attack is an attack method that has been really implemented in attack and defense drills in recent years , It generally refers to the office environment that directly reaches the target , Obtain intranet permissions through various means , For example, attack. WiFi、 insert BadUSB Even connect the network cable directly . And tradition depends on Web The way of invasion is different , Once the attacker appears directly in the office environment , Basically, it is easy to obtain intranet permissions .
Puddle attack
Puddle attack is a more vivid way to describe , The essence is to implant malicious code into the application system commonly used by target employees , Capture the account information of the target employee or fish the target employee .
At present, the common water pit attack in attack and defense drill is carried out in the intranet office application , If in OA Malicious code is implanted into the system login function to record the account and password entered by employees , Or by popping up false prompts such as installing plug-ins to trick employees into executing Trojan horse programs ,
Buffer overflow attack
Buffer overflow is a very common and dangerous vulnerability , It exists in all kinds of operating systems 、 In application software . The cause of this vulnerability is that the programmer does not limit the length of user input to the buffer of the program , Lead to exceeding the expected length, thus destroying the operation of the program , The attacker can manipulate the attacked software and execute the code set by the attacker . Buffer overflow can be divided into 3 class : Destroy stack data 、 Destroy heap data 、 Change the class function pointer .
In the attack and defense drill , Buffer overflow vulnerabilities are often used by attackers , for example CVE-2021-3156 Loophole , It's a loophole for raising rights that was previously disclosed , When in similar Unix When executing commands on the system , Not root Users can use sudo Command to root Authority to execute orders .
Replay attack
- Replay attack refers to an attacker sending a packet that has been received by the destination host , To deceive the system , Mainly used in the authentication process , Destroy the correctness of certification .
- Replay attacks can be initiated by , It can also be carried out by the enemy who retransmits the data from the interception well . Attackers use network monitoring or other ways to steal authentication credentials , Then send it back to the authentication server .
The basic principle of replay attack is to resend the previously heard data to the receiver intact .
- A lot of times , The data transmitted on the network is encrypted , At this time, the eavesdropper cannot get the accurate meaning of the data .
- But if he knows the role of these data , You can fool the receiver by sending these data again without knowing the data content .
- for example , Some systems will simply encrypt the authentication information and then transmit it , At this time, although the attacker cannot eavesdrop on the password , But they can first intercept the encrypted password and then replay it , So we can use this way to attack effectively .
Common attack tools
[1] Ice scorpion / Godzilla
Ice scorpions and Godzilla can be classified as a new generation after the rise of offensive and defensive exercises webshel! Management tools , With traffic encryption
And powerful features , And it has or can have the function of managing memory code after secondary development , It was very
Favored by multi attack teams ;
Ice scorpion project address :https://github.com/rebeyond/Behinder
Godzilla project address :https://github.com/BeichenDream/Godzilla
[2] Impacket
Linux Next is the suite for domain penetration , Project address :https://github.com/SecureAuthCorp/impacket
[3]Rubeus
Windows One of the tools for domain penetration under , Project address :https://github.com/GhostPack/Rubeus
[4] Proxychains
Linux Common traffic forwarding tools on the operating system , But cannot forward udp Traffic ;
[5] Proxifier
Windows Common traffic forwarding tools , Operate through the visual interface , It's friendly to users ;
[6] FRP
Common agent tools , Project address :https://github.com/fatedier/frp
[7] NPS
Common agent tools , Project address :https://github.com/ehang-io/nps
[8] CS
Common remote control software , Full name Cobalt strike, Official website address :https://www.cobaltstrike.com/;
[9] MSF
Common remote control software , Full name Metasploit, Official website address :https://www.metasploit.com/;
[10]Windows Power lifting AIDS
Official website address :https://i.hacking8.com/tiquan/;
[11] Sandbox as a service
Hybrid Analysis By Payload Security Free malware analysis services provided , Can use its unique
Hybrid analysis technology detects and analyzes unknown threats .
边栏推荐
- js获取服务端IP、端口、协议
- 数据可视化第五章
- 聊一聊损失函数
- Cloud native and low code platforms make agile enterprises
- Draw the corresponding rectangular box on the picture according to the returned picture and coordinates
- the volume for a file has been externally altered so that the opened file is no longer valid
- Applet sharing how to pass parameters
- Connect mysql database in tableau
- 原生小程序使用 vant-weapp 引入
- KY小说采集规则(5条采集规则)
猜你喜欢
随机推荐
牛客刷题——剑指offer
如何导出异步的数据两种方法
C语言 柔性数组
js获取服务端IP、端口、协议
数据可视化第五章
Use of forkjoin
How bad can a programmer be?
[AR Foundation] AR Foundation基礎
h5 实现公众号登录
Successfully install pyinstaller (solve the problem of PIP install pyinstaller installation failure)
手机app抓取工具手机版selenium—Appium,Mitmdump手机抓包
Applet sharing how to pass parameters
Directly output JSON file from scratch
A simple and easy-to-use translation program
攻防技术第一篇之-知彼(攻击手段)
小程序分享如何传递参数
传统企业是否需要数据中台?
MySQL and Mongo database warehousing in scratch pipeline
从0到1 拿下C语言—程序结构及使用示例
HALCON和OPENCV最终选择了后者