当前位置:网站首页>Attack and defense world ----- lottery
Attack and defense world ----- lottery
2022-07-21 19:41:00 【jjj34】
Knowledge point :
1.git Let the cat out of the
2.php Weak type comparison
After getting the website , Do a directory scan
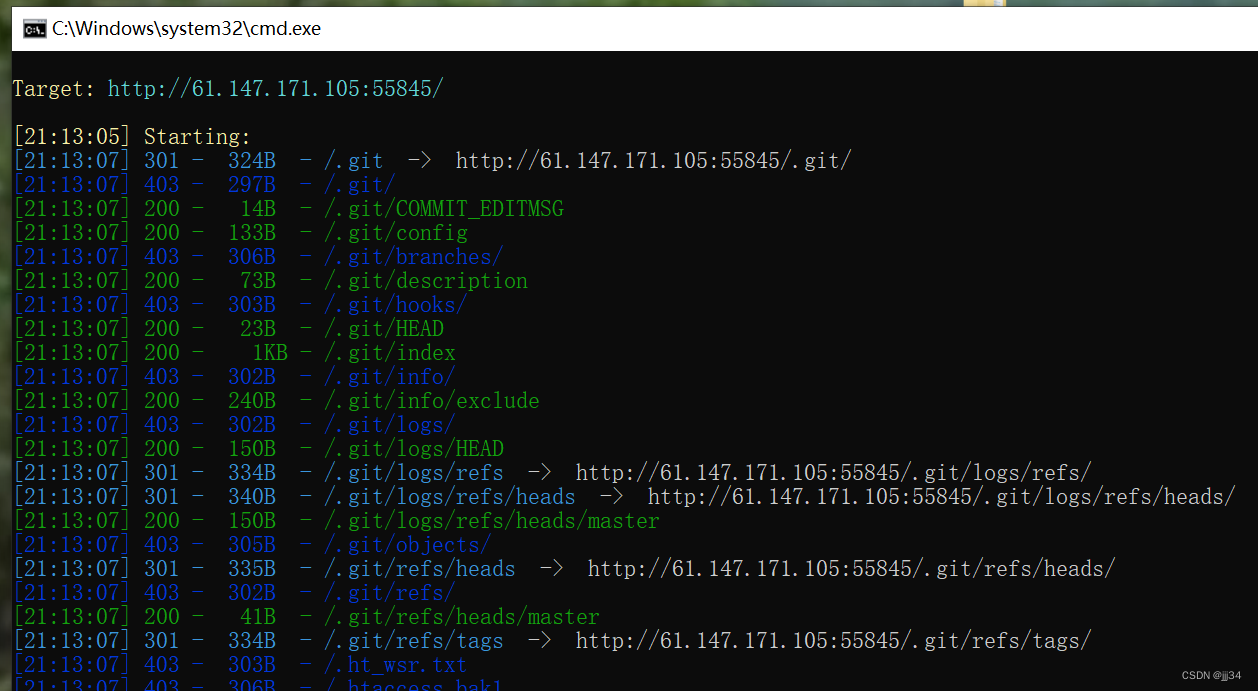
Found to have git Let the cat out of the
open kali, use githack Download

Get the source code and conduct code audit

from index.php Start auditing the purchase of combined websites flag page

Go to bug.php Found in js References to

stay js in , Found out api.php

Final , stay api.php The calculation method of scores is found in

be aware That's Two = Number , Therefore, there are weak type vulnerabilities, namely
true And anything == by true
Such as
true == 1 This is true
true == 2 This is also true
therefore , As long as we put numbers The values in the array are changed to true,true,true,true,true,true,true, Then it must be all right , You can get the highest bonus Ideas have , The next step is to capture and modify the value

take json in ,numbers Change the value of to array value

How many times , You can get enough money , Then buy flag
Be careful : Although we have source code , But you can't change the source code , Because these source codes are run on each other's servers ( You can buy it locally by changing the price )
边栏推荐
- 蚓激酶白蛋白纳米粒/红细胞膜定向包裹血红蛋白-白蛋白纳米粒的研究制备
- 2022 the hottest free Chinese version of the whole network - free sharing of "Application Tutorial of deep learning in image processing"
- Lombok简化开发
- Classic examples of C language: 21-30 examples: insertion sort, Hill sort 1, quick sort, Hill sort 2, recursion, completion, Fibonacci sequence, common divisor and common multiple, judging the number
- 机器学习 sklearn数据集
- Kubernetes technology and Architecture (V)
- Harbor scanner from principle to construction
- 攻防世界----favorite_number
- 电磁场与电磁波实验三 熟悉Mathematica软件在电磁场领域的应用
- Stop learning! These five programming languages are about to die out
猜你喜欢

342个中、英文等NLP开源数据集分享

MySQL optimization summary I

【C语言】文件相关函数详解

支持向量机(理解、推导、matlab例子)
动作活体检测能力,构建安全可靠的支付级“刷脸”体验

无线定位技术实验三 基于信号强度的位置指纹定位仿真

Preparation of hemoglobin albumin nanoparticles encapsulated by Lumbrokinase albumin nanoparticles / erythrocyte membrane

笔试强训第20天

Lombok simplifies development

Technical post | the three most common network card software problems of a40i are analyzed for you one by one
随机推荐
The ability to detect movement in vivo and build a safe and reliable payment level "face brushing" experience
hot wire! The PMP project management certificate is listed in the urgently needed professional personnel
Technical post | the three most common network card software problems of a40i are analyzed for you one by one
技術帖 | A40i最常見的3種網卡軟件問題,為你逐一分析
C语言学习
Tencent im practice: low code and ultra fast instant address book
45. Record the training process of orienmask and the process of deploying Yunshi technology depth camera
C what are the output points of DSP core resample of digital signal processing toolkit
Classic examples of C language: 21-30 examples: insertion sort, Hill sort 1, quick sort, Hill sort 2, recursion, completion, Fibonacci sequence, common divisor and common multiple, judging the number
Deep learning - (5) class of data imbalance_ weight
Okaleido tiger NFT is about to log in to binance NFT platform, and the era of NFT rights and interests is about to start
电磁场与电磁波实验二 熟悉Matlab PDEtool在二维电磁问题的应用
MySQL advanced (b)
26. GD32F103C8T6入门教程--正交编码器的使用
Harbor scanner from principle to construction
Use jpofiler tool to analyze the cause of OOM
受众分析与卸载分析全面升级,HMS Core分析服务6.6.0版本上新
蚓激酶白蛋白纳米粒/红细胞膜定向包裹血红蛋白-白蛋白纳米粒的研究制备
Solve the error: uncaught typeerror: cannot read properties of undefined (reading 'install')
LeetCode:1260. Two dimensional mesh migration [one dimensional expansion + splicing]