当前位置:网站首页>Knock on the blackboard! There are so many core knowledge points of kubernetes architecture
Knock on the blackboard! There are so many core knowledge points of kubernetes architecture
2022-07-22 11:16:00 【Dbaplus community】

Catalog
One goal : Container operation
Three centers in two places
Four layer service discovery
Five kinds Pod Shared resources
six CNI Common plug-ins
Seven layer load balancing
Eight dimensions of isolation
Nine network model principles
One goal : Container operation ; Three centers in two places ; Four layer service discovery ; Five kinds Pod Shared resources ; six CNI Common plug-ins ; Seven layer load balancing ; Eight dimensions of isolation ; Nine network model principles ; Ten categories IP Address ; 100 level product line ; A thousand level physical machine ; Ten thousand level container ; Like no billion ,K8s There are 100 million : 100 million daily service people .
One goal : Container operation
Kubernetes(k8s) Is an open source platform for automated container operations . These container operations include : Deploy 、 Expansion between scheduling and node clusters .
1) Specific function
Automate container deployment and replication .
Real time elastic shrinkage of container size .
Containers are organized into groups , And provide load balancing between containers .
Dispatch : Which machine does the container run on .
2) form
kubectl: Client command line tools , As the operation entrance of the whole system .
kube-apiserver: With REST API Service forms provide interfaces , As the control entrance to the whole system .
kube-controller-manager: Perform background tasks of the whole system , Including node status 、Pod Number 、Pods and Service And so on .
kube-scheduler: Responsible for node resource management , Receive from kube-apiserver establish Pods Mission , And assign it to a node .
etcd: Responsible for service discovery and configuration sharing among nodes .
kube-proxy: Running on each computing node , be responsible for Pod Network proxy . From time to time etcd Get service Information to do the corresponding strategy .
kubelet: Running on each computing node , As agent, Receive the Pods Tasks and management containers , Get container state periodically , Feedback to kube-apiserver.
DNS: An optional one DNS service , For each Service objects creating DNS Record , So all of Pod You can go through DNS Access to services .
3)K8s The architecture topology of

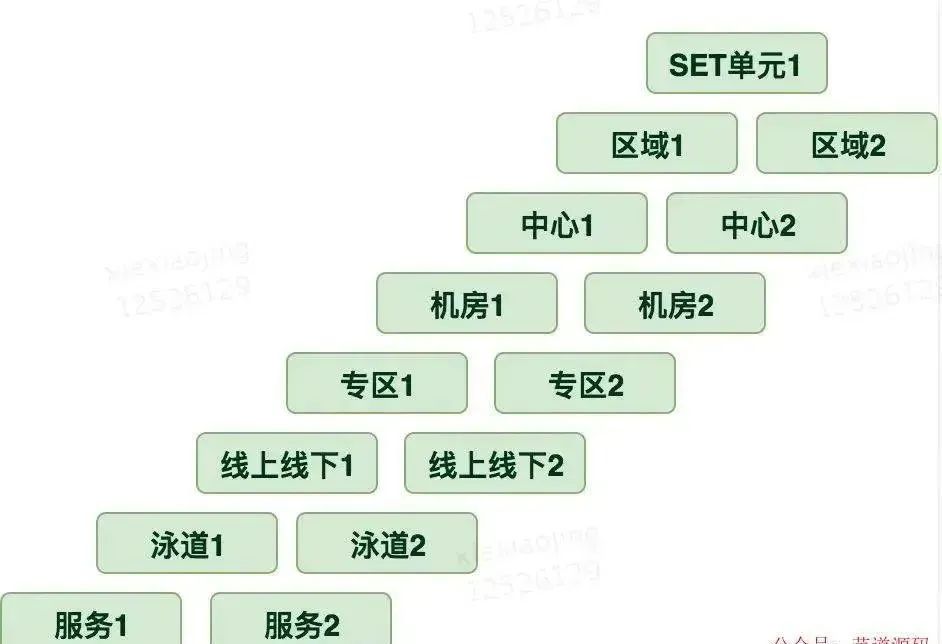
Three centers in two places
The three centers of the two places include the local production center 、 Local disaster recovery center 、 Remote Disaster Recovery Center .

An important problem to be solved by the two places and three centers is data consistency .k8s Use etcd Component as a highly available 、 Highly consistent service discovery repository . For configuration sharing and service discovery .
It has been recognized as a country Zookeeper and doozer Inspired projects . In addition to having all their functions , Also have the following 4 Characteristics :
Simple : be based on http+json Of api Let you use it curl The command is easy to use .
Security : Optional SSL Customer authentication mechanism .
Fast : Each instance supports 1000 write operations per second .
trusted : Use Raft The algorithm fully realizes the distributed .
Four layer service discovery
Let's start with a diagram to explain the network layer 7 protocol :
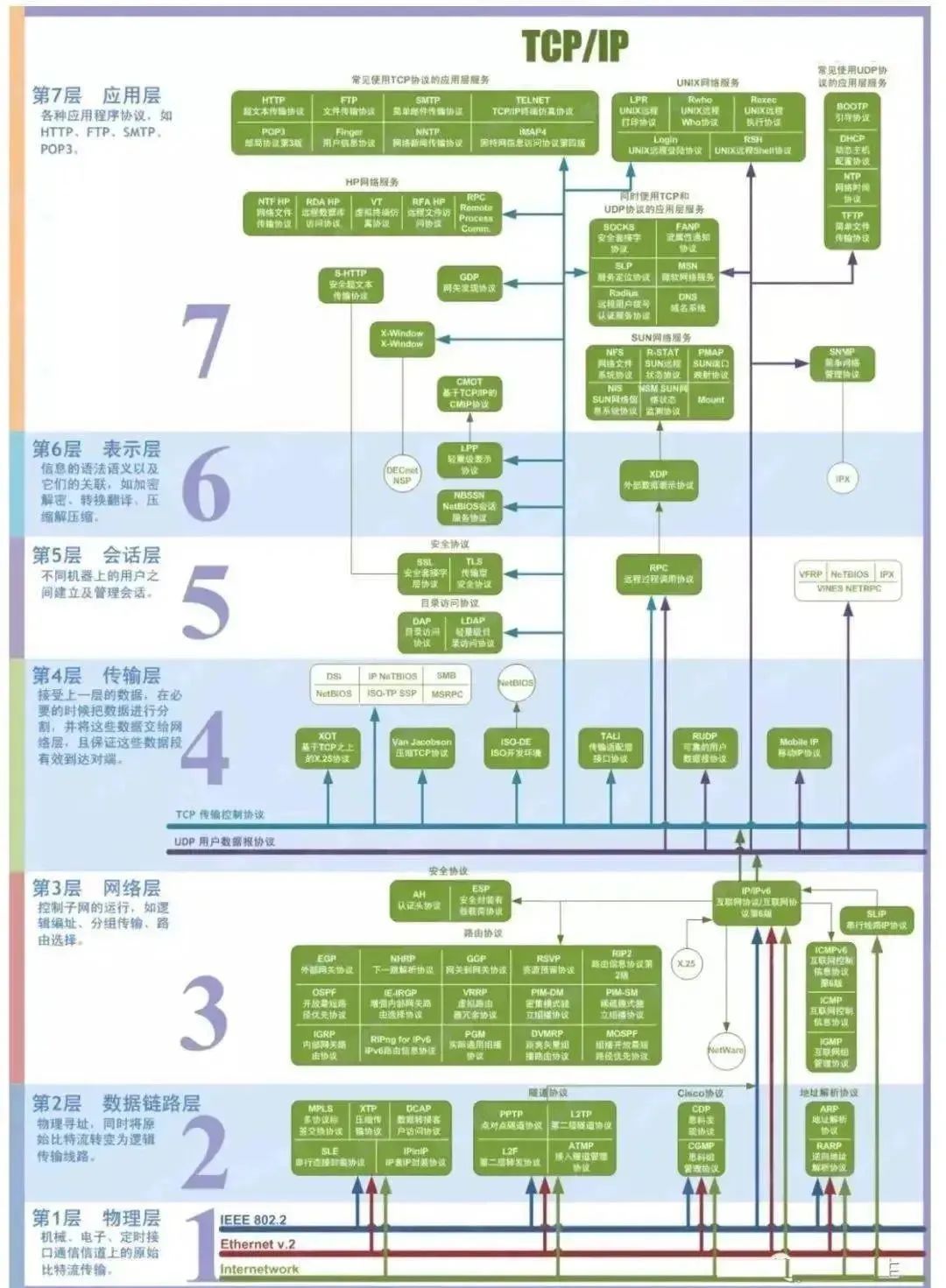
k8s Two ways of service discovery are provided :
environment variable
When creating a Pod When ,kubelet It's time to Pod In the cluster Service The relevant environment variables of . It should be noted that , Think of one Pod To inject some Service Environment variables of , You have to Service It's better to compare first Pod establish . This point , It almost makes this way of service discovery unavailable .
such as , One ServiceName by redis-master Of Service, Corresponding ClusterIP:Port by 10.0.0.11:6379, Then the corresponding environment variable is :

DNS
Can pass cluster add-on Easy way to create KubeDNS Let's talk about Service Perform service discovery .
There are two ways , One is based on tcp, as everyone knows ,DNS Is based on UDP Of , They're all built on four layer protocols .
Five kinds Pod Shared resources
Pod yes K8s The most basic operating unit , Contains one or more closely related containers , One Pod Can be viewed as application-level by a containerized environment “ Logic host ”; One Pod Multiple container applications in are usually tightly coupled ,Pod stay Node Is created on the 、 Initiate or destroy ; Every Pod There runs a special one called Volume Mount the volume , So they communicate and exchange data more efficiently , At design time, we can make full use of this feature to put a set of closely related service processes into the same Pod in .

The same Pod It's only necessary to pass through localhost Can communicate with each other .
One Pod Application containers in share five resources :
PID Namespace :Pod Different applications in can see the progress of other applications ID.
Network namespace :Pod Multiple containers can access the same IP And port range .
IPC Namespace :Pod Multiple containers can be used SystemV IPC or POSIX Message queues communicate .
UTS Namespace :Pod A host name is Shared by multiple containers in .
Volumes( Shared volume ):Pod Each container can be accessed in Pod Level defined Volumes.
Pod Through the life cycle of Replication Controller To manage ; Defined by template , And then assign it to a Node Up operation , stay Pod After the included container runs ,Pod end .
Kubernetes by Pod Designed a unique network configuration , Include : For each Pod Allocate one IP Address , Use Pod Name as the host name for communication during the period .
six CNI Common plug-ins
CNI(Container Network Interface) Container network interface , yes Linux A set of standards and libraries for container network configuration , Users need to develop their own container network plug-ins according to these standards and libraries .CNI Only focus on solving the resource release of container network connection and container destruction , Provide a framework , therefore CNI Can support a large number of different network modes , And it's easy to implement .
Here's a diagram of six CNI Common plug-ins :

Seven layer load balancing
When it comes to load balancing, we have to mention the communication between servers first .
IDC(Internet Data Center), Also called Data Center 、 Computer room , To put the server .IDC Network is the bridge of communication between servers .

The picture above shows a lot of network devices , What are they for ?
Router 、 Switch 、MGW/NAT It's all network devices , According to performance 、 The internal and external networks are divided into different roles .
Intranet access switch : Also known as TOR(top of rack), It's the device that the server connects to the network . Each intranet access switch is down connected 40-48 Servers , Use a mask for /24 As the intranet segment of the server .
Intranet core switch : be responsible for IDC Traffic forwarding and cross connection of each intranet access switch IDC Traffic forwarding .
MGW/NAT:MGW namely LVS For load balancing ,NAT It is used for address translation when intranet devices access the Internet .
Internet core router : Through static internet operators or BGP Internet meituan unified external network platform .
Let's talk about the load balancing of each layer first :
Second level load balancing : be based on MAC Two layer load balancing of address .
Three layer load balancing : be based on IP Address load balancing .
Four layer load balancing : be based on IP+ Port load balancing .
Seven layer load balancing : be based on URL Load balancing of application layer information .
Here is a diagram to talk about the difference between layer 4 and layer 7 load balancing :

Service There could be a lot of , If each is bound to one node Host port , The host needs to open the peripheral port for service invocation , Management confusion .
Unable to apply firewall rules required by many companies .
The ideal way is through an external load balancer , Bind fixed ports , such as 80, Then according to the domain name or service name to the following Service ip forward ,Nginx It's a good solution to this demand , But the problem is that if you have the experience service to join , How to modify Nginx Configuration of , And load these configurations ?Kubernetes The solution is Ingress. This is a base 7 Layer scheme .
Eight dimensions of isolation
K8s On the side of cluster scheduling, we need to make corresponding scheduling strategies for the isolation from top to bottom, from coarse-grained to fine-grained .
Nine network model principles
K8s The network model should conform to 4 There are two basic principles ,3 It's a network requirement principle ,1 There are two principles of architecture ,1 individual IP principle .
Every Pod All have an independent IP Address , And assume that all Pod All in a directly connected 、 In the flat cyberspace , Whether it's running on the same Node You can go through on the Internet Pod Of IP To visit .
K8s Medium Pod Of IP It's the minimum size IP. The same Pod All containers in share a network stack , The model is called IP-per-Pod Model .
Pod from docker0 The actual distribution of IP.
Pod What you see inside IP The address and port are consistent with the outside .
The same Pod Different containers in share network , Can pass localhost To access each other's ports , Similar to the same VM Different processes in the world .
IP-per-Pod The model allocates from the port 、 Domain name resolution 、 Service discovery 、 Load balancing 、 From the perspective of application configuration ,Pod It can be seen as an independent VM Or physical machine .
All containers can be dispensed with NAT To communicate with other containers .
All nodes can be in different NAT In the same way as all containers, heartache , vice versa .
The address of the container is the same as the address seen by others .
To conform to the following Architecture :

From the architecture above IP The concept goes from the outside of the cluster to the inside of the cluster :



边栏推荐
猜你喜欢

Intelligent operation and maintenance scenario analysis: how to detect abnormal business system status through exception detection

Interview difficulties: difficulties in implementing distributed session, this is enough!

BGP-边界网关协议
![Robot modeling and 3D simulation based on ROS [physical / mechanical significance]](/img/c7/997a2da050cf80183f75c9873efb59.png)
Robot modeling and 3D simulation based on ROS [physical / mechanical significance]

路由策略-

TCP 滑动窗口详解(非常实用)

Dokcer运行Nacos容器自动退出问题

What are the five standards for the dual prevention mechanism of hazardous chemical enterprises and what are the contents

TypeScript—快速入门
![Women's health and health information network dream weaving template (with mobile terminal) [test can be built]](/img/c3/63c511f492ff20880dec5dc4108bce.jpg)
Women's health and health information network dream weaving template (with mobile terminal) [test can be built]
随机推荐
《时代》杂志重磅封面:元宇宙时代将改变世界
2021年全国职业院校技能大赛网络搭建与应用之虚拟化配置答案
双指针(一)
黄金买卖在哪里交易安全
Intel E3 V1 V2 V3 CPU parameters
Robot modeling and 3D simulation based on ROS [physical / mechanical significance]
服装ERP上线后,这些问题必须重视
【红队】ATT&CK - Active Scanning(主动扫描)
啊啊啊啊?margin-top的百分比到底相对于谁
Delivery practice of private PAAS platform based on cloud native
向量化引擎对HTAP的价值与技术思考
Keyframesextractutils Py, dynamically supports three framing methods, key parameters can be configured, and the code has been optimized for better effect and performance.
Ah, ah, ah? Who is the percentage of margin top relative to
sql语句,分组后,组内根据datetime字段排序,保留日期最新的一条组内记录,删除其他项。(用于组内重复数据的剔除)
云呐-咸宁通信机房动环监控系统,电信动环监控系统
ACM mode when brushing questions
危化品化工企业双重预防机制五有标准是什么包括哪些内容
tsconfig.json文件的作用
2022 audio and video technology vane
ICML 2022开奖!复旦、上交、厦大多篇工作入选杰出论文