当前位置:网站首页>Three steps to understand Kerberos Protocol easily
Three steps to understand Kerberos Protocol easily
2020-11-06 22:38:00 【Official account Bypass】
Kerberos It's an authentication protocol , It serves as a trusted third-party authentication service , By using symmetric encryption technology for the client / Server applications provide strong authentication . In domain environment ,AD Domain use Kerberos Protocol verification , Be familiar with and master Kerberos Protocol is the basis of learning domain penetration .
Kerberos Three main roles in the protocol :
1. Access to the service Client2. serviceable Server3.KDC: Key distribution center , It is installed on the domain controller by default AS: Authentication service TGS: Ticket granting service Kerberos Protocol authentication process :
The agreement can be divided into three steps : One is to obtain the bill permit , The second is to obtain service license bills , Third, access to services .
First step : Get a note permit note
KRB_AS_REQ: Used to direct to KDC request TGT
When the user enters the domain user and password on the client side , The client converts the user's password to hash As an encryption key , Encrypt the timestamp as request credentials .
cipher: Encrypted timestamp , That is, the current time of the client and the user's hash The result of encryption KRB_AS_REQ The packets are as follows :

KRB_AS_REP: Used by KDC Pass on TGT
Upon receipt of the request ,KDC from AD Domain database to find the user's hash Decrypt the timestamp to verify the user's identity . If the timestamp is within the allowed time range , Then it will generate a session key (Session key), With AS_REP The packet responds .
AS_REP Include information :
ticket: Use krbtgt hash encryption , Include user name / Session key and expiration time .enc-part: Using the user hash encryption , Contains the session key /TGT Expiration time and random number ( Anti replay )KRB_AS_REP The packets are as follows :

The second step : Get a service license ticket
KRB_TGS_REQ: Use TGT towards KDC request TGS
The client gets TGT And user key encryption enc-part, Using the user hash Decrypt enc-part Get session key (Session key), Then use the session key to change the user name / The timestamp is encrypted , Generate authenticator and TGT Send to TGS.
ticket: It's actually a picture of TGT, The client doesn't have krbtgt hash, So we can't decrypt TGT.KRB_TGS_REQ The packets are as follows :

KRB_TGS_REP: adopt KDC Pass on TGS
TGS received KRB_TGS_REQ After the request , Use krbtgt hash Decrypt ticket Get session key (Session key), Then decrypt it with the session key authenticator Get the user name and timestamp for authentication . After confirming the information , Create a service session key (Service Session key).
ticket: Encrypt with the corresponding service key , Contains the service session key / user name / Expiration time and other information , It's essentially a piece of ST(Service Ticket).enc-part: Contains the service session key encrypted with the session key (Service Session key)KRB_TGS_REP The packets are as follows :
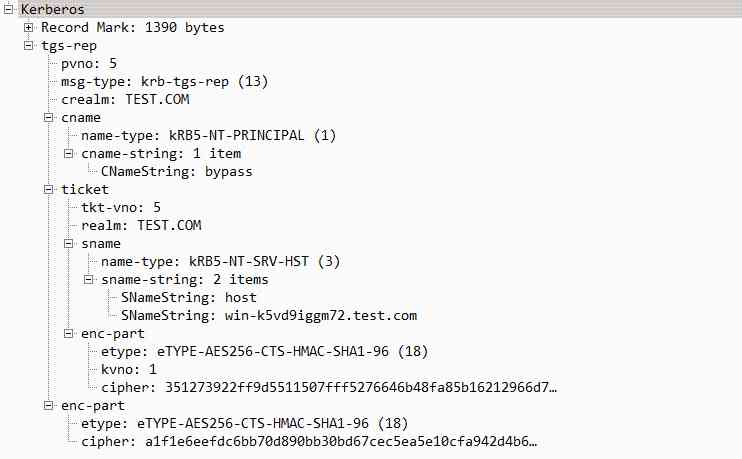
The third step : Get services
KRB_AP_REQ: Use TGS, The service authenticates the user
The client already has a valid TGS Can interact with services , Decrypt with session key enc-part, obtain Service session key (Service Session key), Put the user name / Information such as timestamps uses the service session key (Service Session key) To encrypt , Get new Authentication.
KRB_AP_REP: Used by a service to identify itself to a user
The server receives the request , Use your own hash Decrypt TGS Get the service session key (Service Session key) And authorized user information , Then decrypt it using the service session key Authentication, Compare user names and timestamps , If there are mutual verification marks , The client sends the session key to the encrypted service with a timestamp , The client decrypts the timestamp and verifies the server , And then you start asking for services .
This article is from WeChat official account. - Bypass(Bypass--).
If there is any infringement , Please contact the [email protected] Delete .
Participation of this paper “OSC Source creation plan ”, You are welcome to join us , share .
版权声明
本文为[Official account Bypass]所创,转载请带上原文链接,感谢
边栏推荐
- [doodling the footprints of Internet of things] Introduction to Internet of things
- VARCHART XGantt如何在日历上表示工作日
- Mobile pixel adaptation scheme
- Windows 10 蓝牙管理页面'添加蓝牙或其他设备'选项点击无响应的解决方案
- Characteristics of magnetic memory chip STT-MRAM
- 汽车维修app开发的好处与功能
- 实验一
- JS string - string string object method
- Reserved battery interface, built-in charge and discharge circuit and electricity meter, quickly help easily handle hand-held applications
- 三步轻松理解Kerberos协议
猜你喜欢

JS array the usage of array is all here (array method reconstruction, array traversal, array de duplication, array judgment and conversion)

Summary of common SQL statements

2020-08-29: process thread differences, in addition to the inclusion relationship, the underlying details?

2020 database technology conference helps technology upgrade

STM32F030F4P6兼容灵动微MM32F031F4P6

ado.net and asp.net The relationship between

image operating system windows cannot be used on this platform

Windows 10 Bluetooth management page 'add Bluetooth or other devices' option click no response solution

大佬们如何在nginx镜像里面增加模块?

Jenkins入门(二)声明式流水线Jenkins Pipeline
随机推荐
win7 APPCRASH(解决方法)(转)
三步轻松理解Kerberos协议
Markdown tricks
条形码识别性能低,如何优化Dynamsoft Barcode Reader解码性能
The Interpreter pattern of behavior pattern
【涂鸦物联网足迹】物联网基础介绍篇
The use of Xunwei imx6 development board device tree kernel menuconfig
VARCHART XGantt如何在日历上表示工作日
Js数组-数组的用法全在这里(数组方法的重构、数组的遍历、数组的去重,数组的判断与转换)
Ora-02292: complete constraint violation (midbjdev2.sys_ C0020757) - subrecord found
[byte jumps, autumn recruitment Posts open] ohayoo! Don't leave after school, I want to ask you to play games!!!
How to optimize the decoding performance of dynamsoft barcode reader
How to create an interactive kernel density chart
Utility class functions (continuous update)
The isolation level of transaction and its problems
August 14, 2020: what are the execution engines for data tasks?
Interviewer: how about shardingsphere
2020-09-04: do you understand the function call convention?
How to start the hidden preferences in coda 2 on the terminal?
Exclusive interview with Alibaba cloud database for 2020 PostgreSQL Asia Conference: Zeng Wenjing