当前位置:网站首页>User identity authentication of industrial Internet based on HHT transformation of mouse behavior
User identity authentication of industrial Internet based on HHT transformation of mouse behavior
2022-07-22 11:55:00 【Midoer technology house】
Abstract
The rapid development of industrial Internet has aroused widespread concern about network security , End user authentication technology has become a research hotspot . According to the human-computer interaction characteristics of industrial Internet , Designed an experimental website , Collected the website 24 The mouse behavior data of users in an uncontrolled environment for two and a half years is taken as an example , Using Hilbert Huang transform (HHT, Hilbert-Huang transform) Extract the frequency domain characteristics of mouse behavior signals , Combined with time domain characteristics , formation 163 Dimensional time-frequency domain joint characteristic matrix , Used to characterize user mouse behavior patterns . Use Bagged tree、 Support vector machine (SVM, support vector machine)、Boost tree
边栏推荐
- 3 亿
- Use opencv and OS or pathlib Path gets the path name and image name, and saves the image to the specified path
- 基于FPGA-Jetson的智能电网硬件实时联合仿真
- Relational operator 3 (Gretel software - Jiuye training)
- Dokcer running Nacos container automatic exit problem
- 第01篇:分布式注册中心
- PyQt5制作一个精致的视频播放器*附源码
- Redis的主从复制
- Frame coding of h264 -- dialysis (I frame +p frame +b frame coding) principle and process
- Meta's latest image generation tool is popular, and it can actually draw dreams into reality!
猜你喜欢

去中心化边缘渲染元宇宙协议Caduceus如何引爆Metaverse Summit 2022

Go语言 并发与通道

Redis的 缓存穿透、击穿、雪崩

加密市场飙升至1万亿美元以上 不过是假象?加密熊市远未见底

Go语言 反射

布隆过滤器与布谷鸟过滤器(经典版)
![[英雄星球七月集训LeetCode解题日报] 第21日 堆](/img/6c/34eb23942306a67ebfc18afc0f2556.png)
[英雄星球七月集训LeetCode解题日报] 第21日 堆
![[how to optimize her] teach you how to locate unreasonable SQL? And optimize her~~~](/img/74/5ec407849153383da61e71620553ca.png)
[how to optimize her] teach you how to locate unreasonable SQL? And optimize her~~~

【快速上手教程5】疯壳·开源编队无人机-飞控固件烧写
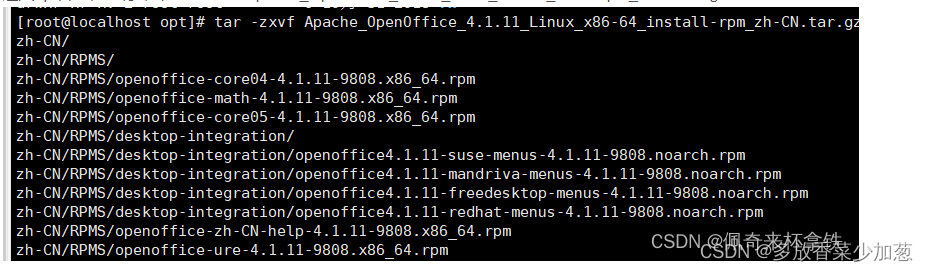
OpenOffice startup and auto startup settings
随机推荐
马斯克上传大脑很疯狂,Neuralink却早已一地鸡毛
Why do you work as a test / development programmer? Description of all partners
Screen adaptation method of mobile web app (summary)
网信办严厉查处诱导未成年人参与直播打赏行为:直播打赏行业乱象必须整治
LeetCode·987. Vertical traversal, bucket sorting and Simulation of binary tree
Meta's latest image generation tool is popular, and it can actually draw dreams into reality!
面向mMTC的5G网络多随机接入机制性能优化策略
Redis是如何实现点赞、取消点赞的?(荣耀典藏版)
[Bi design project recommendation] those interesting Bi design projects that seniors have done - Bi design project sharing (MCU embedded Internet of things STM32)
Chen Chunhua's diploma was questioned, and the latest response from Peking University came
Meta: predict the potential impact of the metauniverse from the development and innovation of mobile technology
Week 5 Linear Models for Classification (Part A)
Framework定制系列(十)-----SystemUI定制状态栏statusbar和导航栏navigationbar教程
加密市场飙升至1万亿美元以上 不过是假象?加密熊市远未见底
工业互联网的概念、体系架构及关键技术
经典网络架构学习-ResNet
001_ Getting started with kubernetes
Force deduction ----- negative numbers in the statistical ordered matrix
基于SSM+MySQL+JQuery的医药管理系统
关系运算符3(阁瑞钛伦特软件-九耶实训)