当前位置:网站首页>Malloc and space Configurator
Malloc and space Configurator
2022-07-22 01:16:00 【Diligent_ wu】
malloc Principle :
1.malloc Start searching for free space , If you can find a suitable space, allocate it
2. If it cannot be found, call the system call brk Get more free space from the heap ( With 128 For boundaries ,brk or mmap)
3. call brk Then turn to the kernel state , At this time, the virtual address system starts to work , Expand the heap area of the process ( No more physical memory allocated )
4.brk Return to malloc,malloc Find the right space and return ( Switch from kernel mode to user mode )
5. Process gets resources , Continue to work
6. When there is code to read and write the newly applied memory, there is a page missing interrupt , At this time, switch from user mode to kernel mode , The operating system allocates physical memory at this time , Switch back to , The program continues .
Space configurator
STL-SGI Use a two-level space configurator to ensure the rational application of heap resources , exceed 128types Use of and space configurator , lower than 128 Byte use secondary space configurator , The following is the specific allocation process of the secondary space configurator 
边栏推荐
猜你喜欢
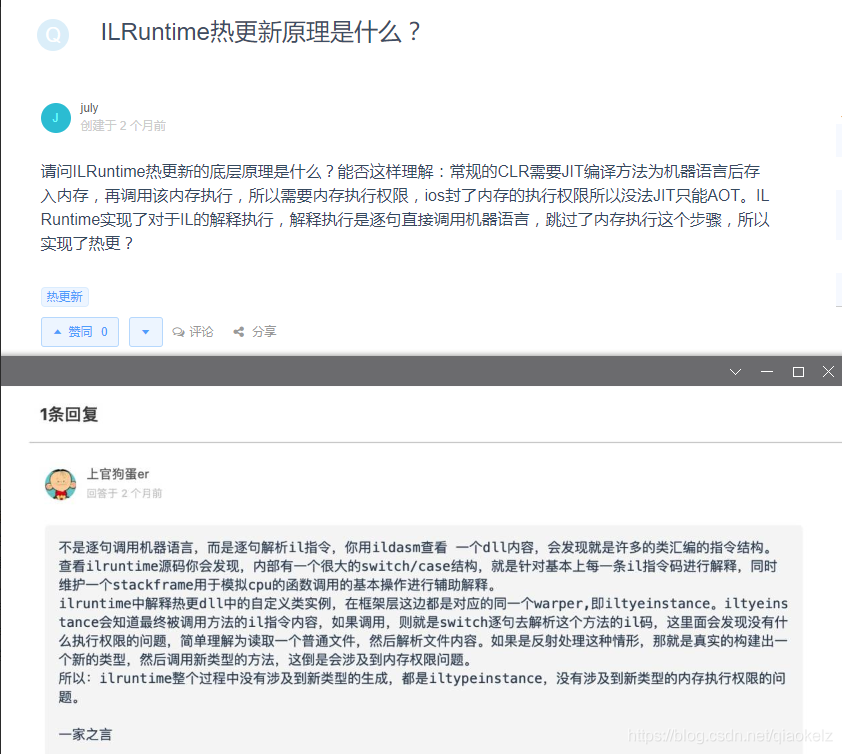
Unity learning notes - Hot update related
Time insertion syntax of Oracle table

11 ways to obtain SSL certificates for free

探寻机器人创客教育中的趣味

传输层协议解析——UDP和TCP

He Bin's full text in C language, with notes for his own use, gives latecomers some ideas

Analysis of steam education benefiting primary and secondary schools
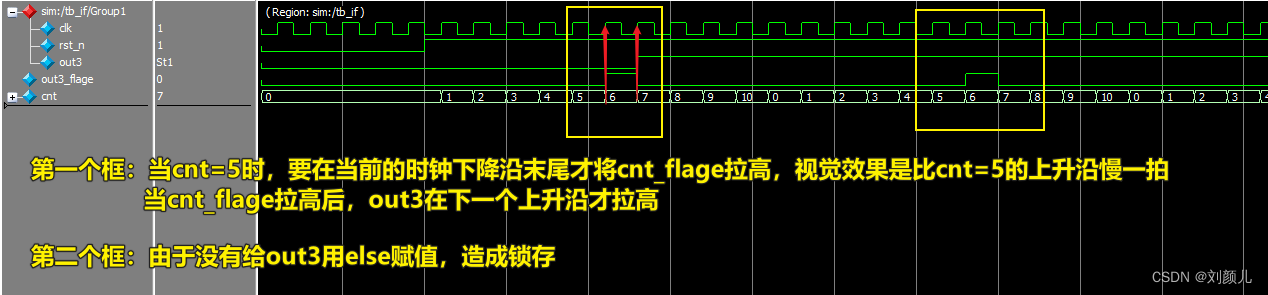
If else: is there a clock cycle difference between the judgment statement and the execution statement? Parallel execution? Is there a priority?

CUDA文件中无法打开源文件<stdio.h>

malloc 和 空间配置器
随机推荐
逍遙管理器安裝
Cannot open source file < stdio. in CUDA file h>
Business based data governance, so that business data can play a long-term value
Business innovation driven by metadata to build new competitive advantages of enterprises
Design and implementation of tcp/ip protocol stack LwIP: Part Five
[network security] common questions in interview -- SQL injection
Redis 官方可视化工具,高颜值,功能真心强大!
Openshift security (17) - integrate compliance scanning of openshift compliance operator into rhacs
Lecture 1 Overview
DOM -- style operation
KY novel collection rules (5 collection rules)
Leetcode [sword finger offer II 068. find the insertion position
Installation du gestionnaire de loisirs
uniapp 使用 u-view 框架小程序的样式问题集合
查看IAR工程所用版本号
IP address segment classification
If else: is there a clock cycle difference between the judgment statement and the execution statement? Parallel execution? Is there a priority?
Interpreting the maker education model in line with the mainstream of the new era
Tokio channel performance test
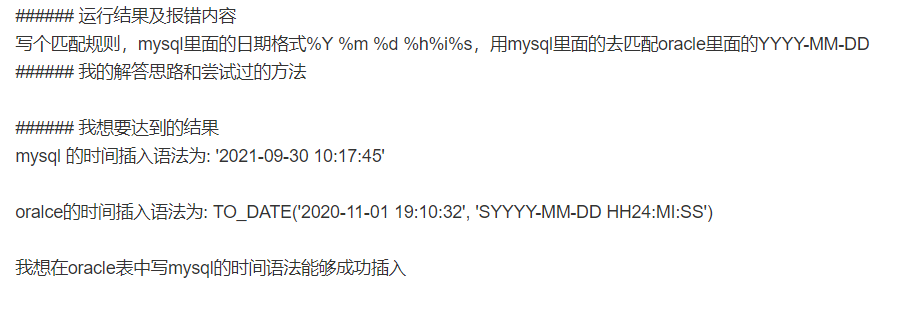
Time insertion syntax of Oracle table