当前位置:网站首页>The communication process and principle of peer-to-peer host are very simple
The communication process and principle of peer-to-peer host are very simple
2022-07-22 00:06:00 【Sicheng code block】
Hello everyone , Today, let's share the communication process and principle of peer-to-peer hosts
Explanation of peer-to-peer network :
Peer to peer network adopts decentralized management , Each computer in the network can work as both a client and a server , Each user manages the resources on his machine .
Look at this network topology :
Let's sort it out :( Analysis of experimental environment )
We can see
pc1 192.168.10.10 255.255.255.0 54-89-98-EB-33-3A
pc2 192.168.10.20 255.255.255.0 54-89-98-FD-58-3D
The result is : They are the hosts of the same segment ( In a network )
Yes, of course , And because of that , They can communicate
That's what it is pc2 Communication results on :

To configure pc1 Of ip
Be careful ip Address , Mask ,mac Address 
to pc2 Configure address 
That's what it is pc2 Communication results on :

We'd better study the process and principle that they can communicate
First , We need to know that they are used ICMP Protocol for communication , The two sides negotiate from the third level ( It's the network layer ), take ICMP Packets are encapsulated in ip Headlines , Source ip yes 192.168.10.10, Purpose ip yes 192.168.10.20, Send the data message to the data link layer
The data link layer will mac Address encapsulation , Contains source mac Address 54-89-98-EB-33-3A And purpose Mac 54-89-98-FD-58-3D, Then it will be sent to the physical layer
Finally, it is converted into an electrical signal and transmitted in the network medium
Here's a question :
Is how to know each other Mac Address of the ?
When the host is encapsulated in the data link layer Mac At the address , The host will find its own ARP( Address resolution protocol ) Address table , If he can find ip The address and the corresponding Mac Address , Will continue the subsequent packaging process , If no relevant records are found , Start the process of inquiry
pc1 In not in your own arp The cache table finds the corresponding information , It will be sent ARP Request message , This source ip Address and mac The address is pc1 Their own , Destination address ip It's each other's ,pc1 The purpose of sending Mac FF-FF-FF-FF-FF( This is a broadcast address , Hosts in a broadcast domain can receive ), For the understanding of broadcast domain, you can think of it as the same network , Because in our peer-to-peer network, there are only pc1,pc2 Two computers , therefore pc2 You can receive this broadcast address
This pc1 Among the broadcast messages sent pc1 Their own ip Address and mac A corresponding information of the address ,pc2 The cache table address of has its own ip Address and mac ,pc2 Will give pc1 Send a ARP And then give pc1
This is the time ,pc1 Will pc2 Of ip Address and mac Put your own AR Cache table address , After the pc2 Of ip Address and mac Assignment in mac Inside the bag , Then it will be sent to the physical layer
Finally, it is converted into an electrical signal and transmitted in the network medium
This is it. pc1 Of ARP Cache table ( There are pc2 Of ip Middle and Mac Address )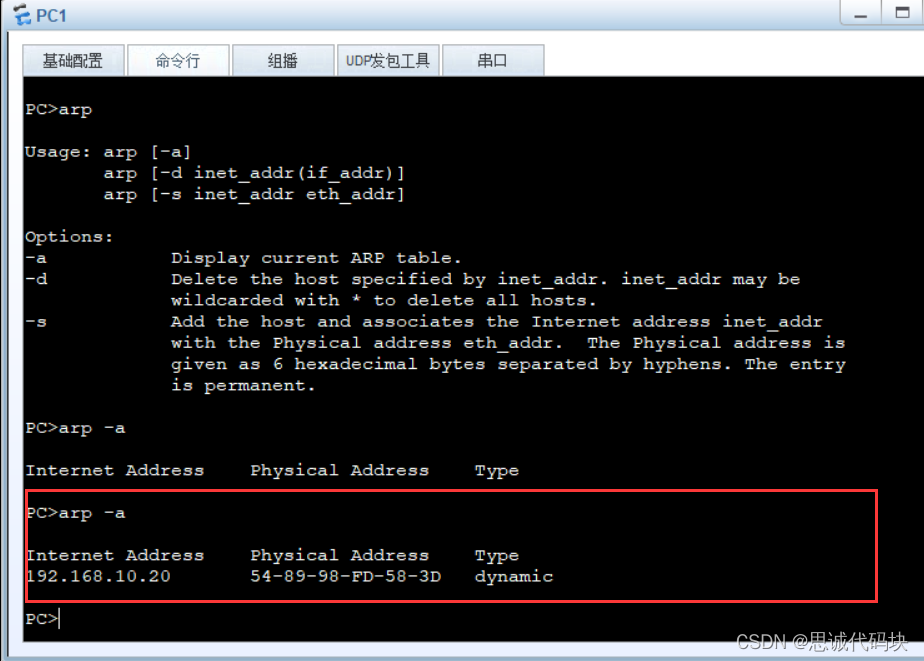
Okay , That's all for the communication process and principle of peer-to-peer host , Thank you.
边栏推荐
- Importance of database monitoring
- ASCII and hexadecimal conversion table
- Dbeaver vs Navicat: database tool duel
- How to do app installation test?
- LR load
- Peoplecode assigns values based on context references
- Use of source lnsight (read uboot under Samba share)
- Detailed explanation of NiO's three cores
- Use Mysql to query logs slowly
- Set up form
猜你喜欢

JMeter之WebService(soap)请求

Pychart 2019 usage settings make it easier for you to use!

NFS FTP PXE

Postman interface test and pressure test

Take you to easily decrypt the white box test and (Demo detailed explanation)

codis集群的搭建

Encapsulation of virtual machine

Lamp架构——mysql集群及组复制(3)

235. Nearest common ancestor DFS method of binary search tree

Practical exercise | export MySQL tables to CSV
随机推荐
Oracle uses data manipulation functions
How to write the use case of APP registration function?
Importance of database monitoring
win7系统忘记登录密码怎么办?(不用启动盘情况下)
Enterprises and individuals choose cloud terminals or cloud servers for cloud desktops? You will know after reading this article
Peoplecode variable
Piracy leads to device paralysis | official solemn statement: do not buy or download Navicat through unofficial channels
Peoplecode operator
SQL SELECT statement
Postman interface test and pressure test
Follow the guidelines and improve yourself quickly: how to quickly turn functional testing to automated testing
How to do regression test
Analysis of cross apply and outer apply query of SQL Server - Part I
What if win7 system forgets its login password? (without startup disk)
Variable usage method of BeanShell of JMeter
[common interview questions of network protocol]
Zabbix+ distributed database tidb realizes distributed database monitoring
Lamp Architecture - MySQL router (read / write separator)
Stack differences
Special test of APP compatibility