边栏推荐
- 她力量系列二丨UCLA李婧翌:女性最不需要做的就是「怀疑自己」
- linux安装oracle XE
- How to solve the blue screen problem in win8.1 system and how to solve the malicious hijacking of IE home page?
- 出现Permission denied的解决办法
- Aminer paper recommendation
- Kubernetes基础
- rp文件chrome浏览器查看插件
- What is the meaning of DNS hijacking, the principle of DNS hijacking and several solutions
- flask 跨域
- Leetcode206 - reverse linked list
猜你喜欢

Kubernets原理分解
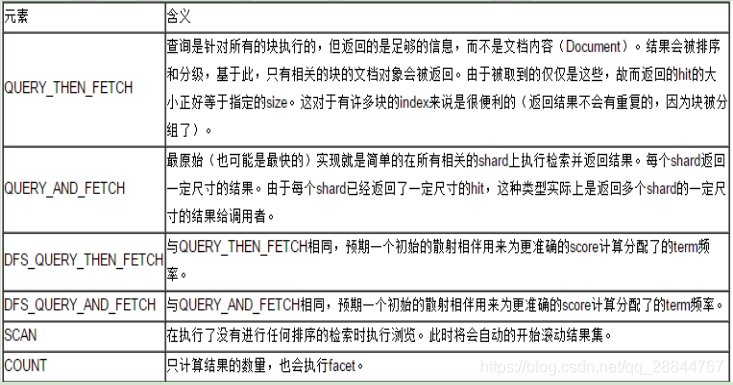
Introduction to elastic search: search full text search (7)

《因果学习周刊》第10期:ICLR2022中最新Causal Discovery相关论文介绍

RAG小结
Her power series 6 - Yang Di 1: when the girl grows up, she can be good at mathematics and chemistry, and scientific research can be very fresh

The well-known software adsafe conceals malicious code to hijack traffic from many websites

她力量系列三丨把握当下,坚持热爱,与食物图像识别结缘的科研之路
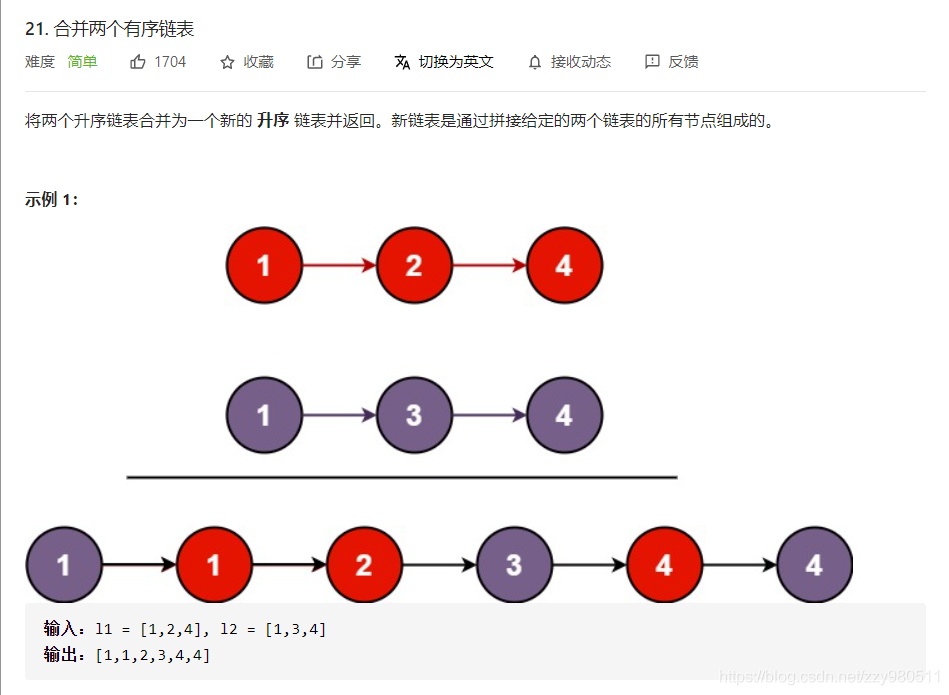
LeetCode21——Merge two sorted lists——Iteration or recursion

本地镜像发布到阿里云

16进制字符串与字节数组之间的转换
随机推荐
iptables实现负载均衡
Flask cross domain
Flask Cross - Domain
flask 跨域
AMiner论文推荐
Common tools for data development - regular sending of query results email
域名劫持定义及原理、域名被劫持解决办法有那些
机器学习入门:逻辑回归-2
LeetCode146——LRU Cache——DS Design
Introduction to machine learning: topic model-4
LeetCode32——next permutation
RP file Chrome browser view plug-in
canny边缘检测
CentOS安装mysql数据库
Leetcode0002——Add Two Numbers——Linked List
IDEA背景图片集
On the horizontal trigger and edge trigger of epoll
深入理解mmap函数
Reinforcement learning weekly 39: approximate optimal depth, multi-agent generalization, character animation reinforcement learning
rp文件chrome浏览器查看插件