当前位置:网站首页>Protocol details of network principles
Protocol details of network principles
2022-07-21 02:11:00 【Curry won't throw three points】
Catalog
Transport layer based protocols
The original problem of the network
Transport layer based protocols
The original problem of the network
- We know that the transport layer is based on the premise that the host and the host can communicate , Let the process communicate with the process , Then the implementation of the transport layer should be based on the implementation of the network layer
- Data in the network , Between routers , Jump and jump , Two problems caused by transferring to the target host ( Discussion based on the perspective of network layer )
- To solve these problems , Let the interested people in the transport layer and application layer solve
Unreliable network transmission
- Data sent , The other party cannot guarantee to receive
- There is no guarantee that the other party will be received strictly in the order of sending ( Because of the router , The path and speed of data transmission may be different , For example, when we go to Beijing in the morning A Make a car ,B Chinese take the high-speed rail ,C Fly in the afternoon , So the possible order of arrival in Beijing is BAC It could be ABC BCA)
The Internet is not secure
- All the data sent , The routers along the way can be checked or modified , hacking , Tampering
- Others can fake the data you send
UDP agreement
- User message protocol , It is a very simple transport layer protocol , It just fulfills the most basic responsibility of the transport layer ( When the host and the host can be connected , Realize process to process connection )
- characteristic 1 There is no connection 2 Unreliable transmission 3 For datagram 4 Receive buffer , No send buffer , But the cost is cheap
- UDP It's not reliable : Not at all UDP What did the agreement do , Become unreliable , But because UDP You've done nothing at all? , Express the unreliability of the network layer directly to the application layer , So from the perspective of application layer , We just said UDP It's not reliable
UDP How it works
- UDP The head of the newspaper , The headers of all network protocols have responsibilities : How to unpack ( How to put data in Chinese header( Headlines ), and payload( The data content ) Separate )
- The problem of distribution , That is, how to implement application layer to application layer
Example
- The items we want to ship are payload, The package and the order on the bag are header
- We just enjoy UDP The process of service
- The delivery car is a service provided by the network layer
UDP Header format
UDP The head has 8 Bytes , from 4 Fields make up , Each field is two bytes ,
- 1. Source port : Source port number , Use when you need a reply , Set it all when you don't need it 0.
- 2. Destination port : Destination port number , You need to use .
- 3. length :UDP The length of the datagram ( Including the first and data ) Its minimum value is 8( Only the first one )
- 4. The checksum : testing UDP Is there any error in the transmission of datagram , If there is a mistake, discard ( The basic principle is to use hash function , As long as the data is the same , After function processing , The hash value must be the same )
The concept of buffer
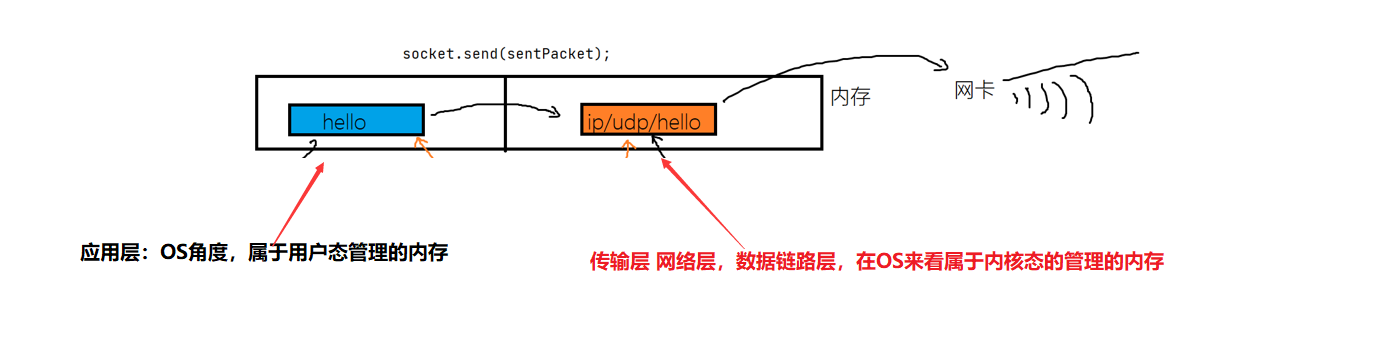
- What we call layering , It's all logical concepts , In terms of hardware , We only have memory ( User mode managed memory and kernel mode managed memory )
- Let's put this memory area , Used to store the data sent or received , It's called a buffer
- Its UDP Only receive buffer ( Just like we send express , There is a rookie post station for us to temporarily store )
In the application layer UDP Agreement , There is no send buffer , If UDP Data sent successfully , What phenomenon does it represent ?
UDP The data is just sent to the network ( In transit ), It's like in our lives , We succeeded in sending the letter , It just means that we sent the letter , I don't know where the letter has been received
UDP Sending process
- Receive data from the application layer ( Remove data from the memory area of the application layer ( User mode ) Copy to the memory area of the kernel )
- Get ready header part 1 Source port number (socket Object with ( Port of the local process ))2 Target port ( The application layer is responsible for filling )3 UDP length (header length + Data length ) By calculation 4 checksum, The checksum , By calculation
- header+payload Get message segment (datagram)
- Wait for the network layer to send successfully ( It means that the data is transferred to the network card )
- Notify the application layer of sending successfully
UDP Receiving process of
- Receive a new package from the network layer (UDP Datagram)
- According to the fixed length (8 Bytes ), Wipe split into headerz and payload—— Unpack
- Read header Four fields of , Source port , Target port , length , The checksum
- Judge whether the length is correct , If the length of the bag is incorrect, throw it away , No one needs to be informed ( Reflects the unreliability )
- Judge whether the checksum is correct ( Judge whether the data is inadvertently damaged ), If there are questions , Directly to throw away
- hold payload Put it in the receive buffer , Relevant information is also included
- Inform the application layer to get information ( Find the corresponding process according to the target port )
- Wait for the application layer to receive information from the receive buffer
- If you don't take it for a long time , You can also throw away the data
边栏推荐
- [OBS] text description of QT UI
- Unity shader implements the image with rounded corners and edge borders
- C语言二叉树+队列实现层次遍历
- Alert log alarm "minact scn: using scan error out with error e:12751" processing
- [leetcode] sword finger offer 53 - I. find the number I in the sorted array
- Exch2010: rebuild the entire DAG
- DP背包问题
- Clé
- What do 1U, 2U and 4U of the server mean?
- alert日志告警“minact-scn: useg scan erroring out with error e:12751”处理
猜你喜欢

推荐一个截图工具-Snipaste

Shengsi YiDianTong | deep learning analysis of classical convolutional neural network

Restore the password parameter of a website login interface

Clé
Understand image storage and image security from image warehouse tools, image download acceleration tools, and security scanning tools
redis简单介绍及redis源码安装配置和docker安装和挂载

Idea多次启动同一个项目
EXCEL的去重去除某个字段后全部操作

深度学习2-线性单元和梯度下降

kvm虚拟化
随机推荐
【培训课程专用】TEE组件介绍
深度学习1-感知器
Interpretation of new features | the restriction of MySQL 8.0 on gtid is lifted
Activiti7 workflow and Alibaba components, second office OA, information management, ERP, etc
昇腾AI创新大赛 | 昇思赛道直播培训,高达1000万奖金的获取指南来啦
Clé
leetcode 剑指 Offer 32 - I. 从上到下打印二叉树
(pc+wap) Zhimeng template accounting service website
响应式织梦模板锁具锁芯类网站
C语言实现并查集
[5gc] 5g PDU session and session type
Redis master-slave replication & sentinel mode
关于:在 Office 2021 中自定义模板
DenseNet学习笔记(核心与resnet进行对比):
【培训课程专用】启动-异常学习笔记-代码导读
Chromeoptions common configuration and webui practice
[special for training course] start - abnormal learning notes - Code Guide
使用Dos命令生成目录文件树
自定义MVC增查
【AD学习记录】为什么原理图和PCB都在同一个文件夹下面了却,无法生成PCB?