当前位置:网站首页>Network Security Learning (IX) comprehensive experiment & PKI
Network Security Learning (IX) comprehensive experiment & PKI
2022-07-21 11:12:00 【Shake light·】

step
1. Restore snapshot
2. Start virtual machine , Connect three computers to the same virtual network card
3. To configure win2008 and win2003 Of IP Address , take 2003 Of dns Set to 2008 Of IP Address 10.1.1.1
4.win2008 Install domain services
5. Check after installation win2008 Of dns, If it's a company server , Be sure to remember to configure DNS Transponder
6. take win2003 Join to domain , After restart, log in with the domain administrator account , install DHCP and web service
7. open DHCP service , Right click authorization

8. To configure DHCP service ,dns Configure to win2008 Of IP Address :10.1.1.1
9. Profile sharing service
10. Configure Web Services
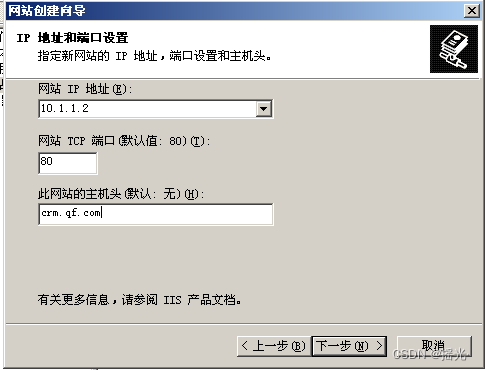
Website ip The address is set to win2003 Of IP Address
Again win2008 Add relevant dns analysis , The address is win2003 The address of

Set the homepage of the website to index.html
If you need web pages to pass domain authentication , You can change it in the web page properties , Check windows Digest authentication for domain servers

Click Select —— Select the specified domain

that will do
PKI Public key infrastructure
effect : Ensure the security of information through encryption technology and digital signature
form : Public key cryptography 、 digital certificate 、CA、RA
Three elements of information security
Confidentiality
integrity
Authentication / Non repudiation of operation
Which? IT Domain use PKI
1)SSL/HTTPS
2)IPsecVPN
3) Partial remote access VPN
Public key cryptography
effect : Realize the encryption of information 、 Digital signature and other security
encryption algorithm :
1) Symmetric encryption algorithm : The encryption and decryption keys are the same as :DES,3DES,AES
If x+5=y It's an algorithm
x It's the original data / original text
y It's ciphertext
5 yes key/ secret key
2) Asymmetric encryption algorithms such as :RSA,DH,
Both sides of the communication generate a pair of public and private keys
Both parties exchange public keys
The public key and the private key are mutually encrypted and decrypted
Public and private keys cannot be pushed against each other
HASH Algorithm :MD5,SHA
HASH Value is irreversible , Used to verify integrity ,
hash Value is also called summary
digital signature
The ciphertext obtained by encrypting the digest with its own private key is a digital signature

In the figure , Big fly , Xiaofei uses RSA encryption algorithm
Dafei holds his father , Private key , Xiaofei's public key
Xiaofei holds his own father , Private key , Dafei's public key
Dafei sends text “ The rockets ”, Use Xiaofei's public key encryption , So Xiaofei can use his private key to unlock , But I don't know who the news comes from , Is the data complete
So use hash algorithm
Dafei sends text “ The rockets ”, Use Xiaofei's public key encryption , Re pass hash The algorithm gets a hash value , Encrypt this value again , Encrypt the value with your private key , This value is called a digital signature
Xiaofei accepts this value , Use Dafei's public key to unlock , Get the value a, I know the news comes from Dafei
Then we received the text encrypted by Dafei with Xiaofei's public key , Unlock with your private key , Then carry it out hash encryption , Get the value b
if a=b, Then the data is complete
namely :
First determine the source of the document , Verify the integrity again , Finally decrypt the file
The only loophole :
Big fly hackers Xiaofei
Public key 123 abc 456
Private key 321 cba 654
When Dafei and Xiaofei exchange public keys , Blocked by hackers , After the exchange, the results are as follows
Big fly :
Public key 123 From hackers abc
Private key 321
hackers :
Public key abc Intercept Da Fei 123
Private key cba
Xiaofei :
Public key 456 Received from hackers abc
Private key 654
As a result, hackers become intermediaries , Stole the information of two people
Vulnerability solutions :
Public key transmission is not secure , Give the public key to the authority (CA Certification authority ) To transmit , and RA yes CA The branch of , It doesn't usually work
certificate
Certificates are used to ensure the legitimacy of public secrets , The certificate format follows X.509 standard
The digital certificate contains information :
User's public key value
User identification information ( Such as name and email address )
The period of validity ( Validity of certificate )
Issuer identification information
Issuer's digital signature
The digital certificate is provided by an authoritative and impartial third party organization, namely CA Issue
PKI experiment
1. Restore snapshot , To configure ip Address ,dns
2. Install related services
2-1 Select the configuration IE ESC

2-2 Ban

Open the role and install the following services
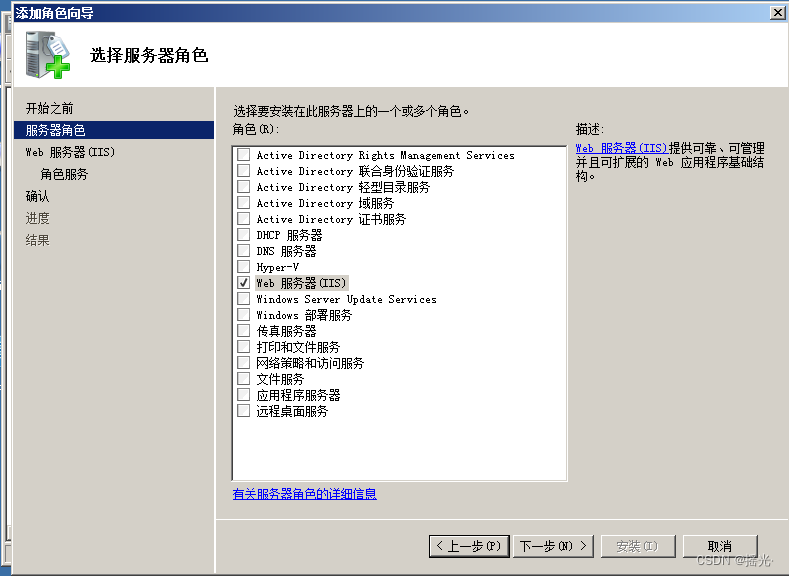


Configure a common IIS service , Check if you can access
3. install CA service
Check relevant services


Children are RA

newly build 
Choose encryption algorithm and key length , The longer it is, the harder it is to crack, and the slower it is to load 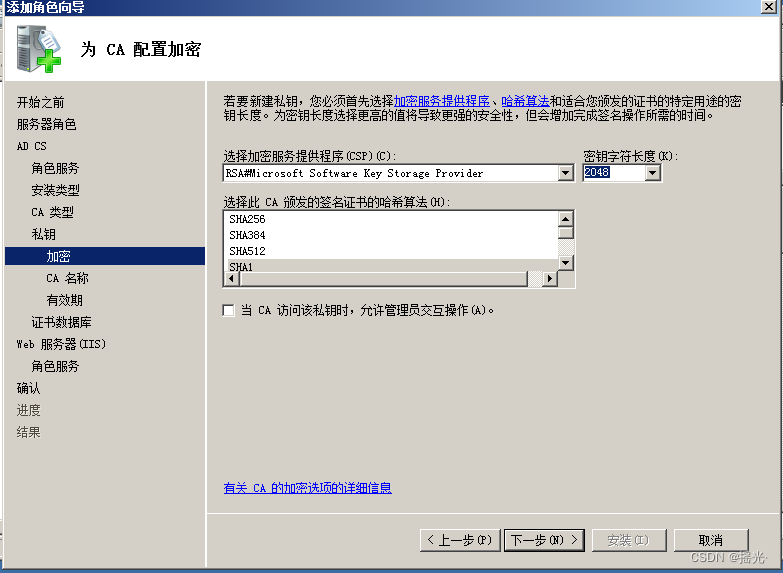
Don't give names indiscriminately 
choice CA Period of validity of the institution 
Don't make any changes 
4. To get the certificate
open IIS, Select the server —— Server certificate

Select Create server certificate

Common names cannot be scrawled , Write domain name

Choose encryption method
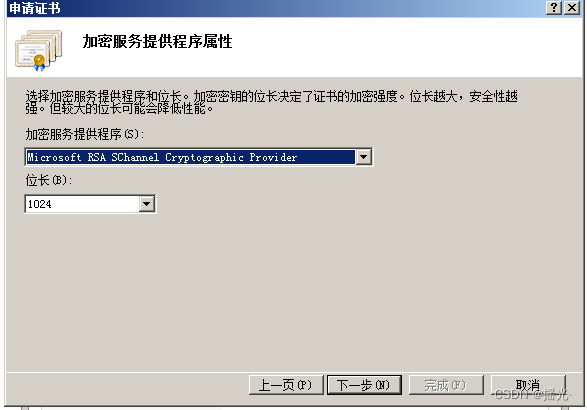
Specify where to put the certificate application documents —— complete

Log in to the certificate application website (10.1.1.1/certsrv) —— Apply for a certificate

senior 
The second item 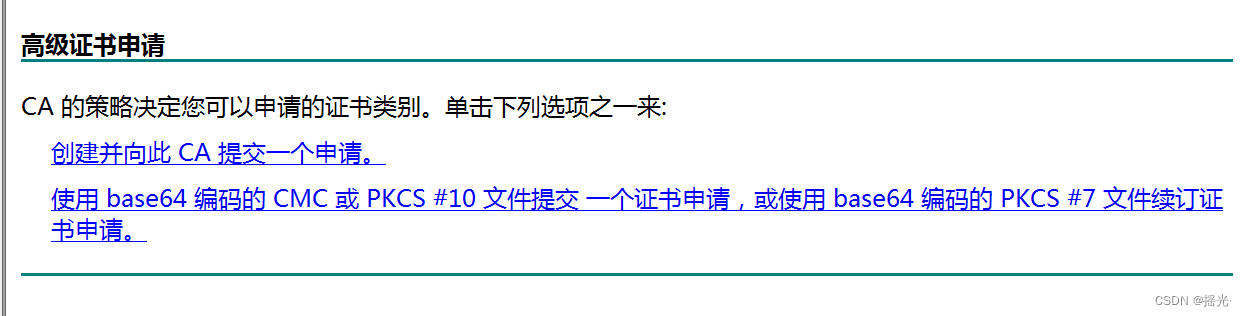
Copy the contents of the file just obtained 
wait for CA agree! 
4. Issued by
Open certification authority —— Pending applications —— Issue according to the operation in the figure 
2. Enter the certificate application website again —— The second item


download

5. Installation certificate
Complete certificate application

Give a certificate name

Set certificate for website —— Edit binding

add to , Instead of editing or deleting
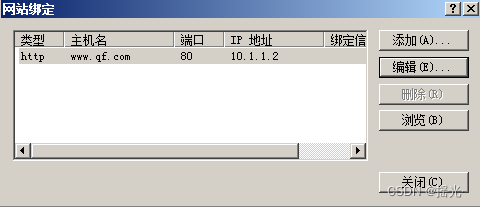
Choose Certificate —— complete
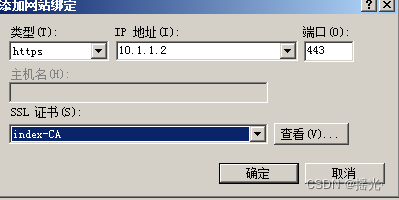
Set up SSL—— Right side application

Visit the website —— continue —— complete ( It can also be opened IE Set up the trust certificate )
If the SSL Set as required , Then the user needs CA Certificate , Or certificate website , Select browser certificate , And the default website also needs a certificate , The method is roughly the same
边栏推荐
- 张小泉,冤吗?
- Debezium grabs data from Oracle to Kafka
- 李宏毅2020机器学习深度学习笔记1+2 &&深度学习基础与实践课程笔记2
- [2022 Huawei developer competition series live broadcast] who can't wait for the wonderful combination of database veterans + best-selling authors?
- 会员数继续下滑,Netflix能靠广告突围吗?
- Acwing game 60 [End]
- 李宏毅2020机器学习深度学习笔记2
- 论文笔记:Accurate Causal Inference on Discrete Data
- [wechat applet] xxxxx is not in the following list of socket legal domain names, please refer to the document
- Understand the secondary node of industrial Internet identity analysis
猜你喜欢
随机推荐
kubevirt 管理虚拟机
李宏毅2020机器学习深度学习笔记2
李宏毅老师2020年深度学习系列讲座笔记9
How to effectively avoid code being "poisoned"?
opencv图像数据增强
单元测试,写起来到底有多痛?你会了吗
21_生命周期
class, classloder, dex 详解
influxdb查询时间戳问题
Install MySQL through docker in centos7
Error when wmware enables virtualization function
[wechat applet] xxxxx is not in the following list of socket legal domain names, please refer to the document
视频物体分割VOS
19_内置指令
遮天三部曲
find_var.sh
Zhang Xiaoquan, are you wronged?
AI helps double carbon goal: let every kilowatt hour be optimized by us
SMS verification
JS smooth scroll to top